We’ve all seen it; maybe it’s on your own computer, or that of a friend, your spouse, child, or parent. Your home page has been changed to some search engine you’ve never heard of, there’s a new, annoying toolbar in your browser. Maybe you’re getting popup ads or have a rogue security product claiming you’re infected and asking you to buy the program to remove the infection. Even worse, you don’t know how it got there! Welcome to the world of Potentially Unwanted Applications (PUAs.) Chances are that these programs were inadvertently installed while installing software from sites that use “download managers” that add additional software to otherwise free downloads.
Many of these “download managers” and the additional applications they install use a Pay Per Install business model that is often used by unscrupulous individuals that use various techniques to trick you into clicking on their sites rather than the official download site for the software you’re attempting to download. These techniques include using advertisements on search engines and various Search Engine Optimization (SEO) techniques to get their sites to show up before the official downloads in search results. We’ve even seen fake image upload sites whose sole purpose is to direct you to a page that looks like an official download page for a program but uses one of these “download managers” instead.
So how do you avoid these “download managers?” It’s actually pretty simple. Whenever possible, download software from the software company’s official page (this is not always possible since some software is only available through third-party download sites.) As mentioned earlier, some of the most popular techniques to get you to install software using these “download managers” is through ads and SEO techniques on search engines, so we’ll show you how to locate the official download links in search results from Google, Bing, and Yahoo.
For this example we’ll search for the popular voice and video chat program Skype by searching for “download Skype.”
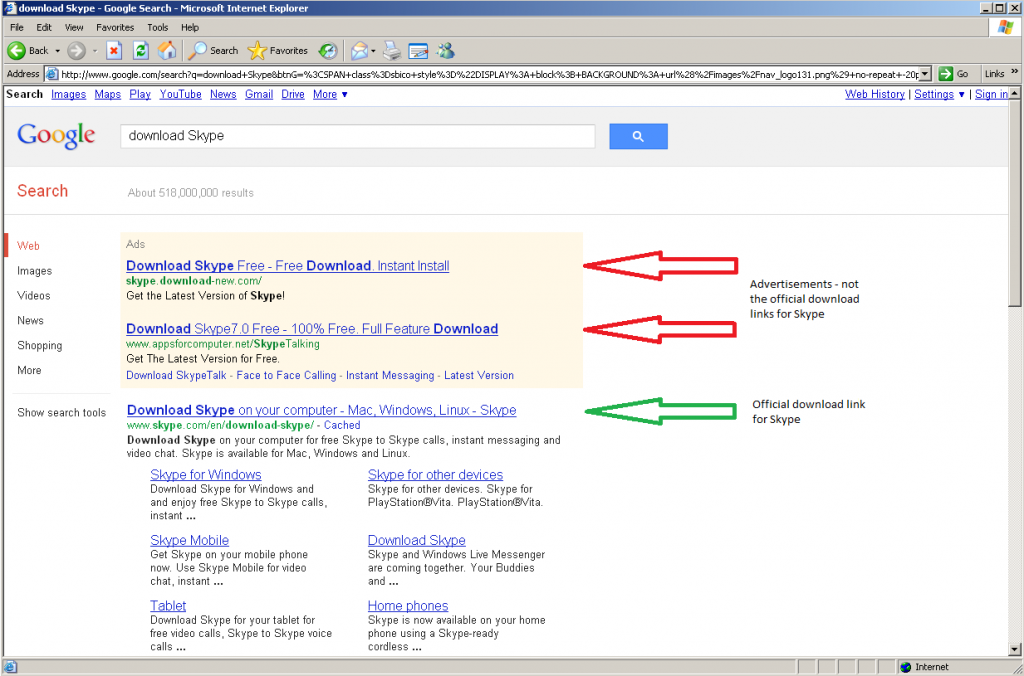
With Google it is rather easy to spot the official download link since the advertisements are clearly marked, and the first actual result is the official download link:
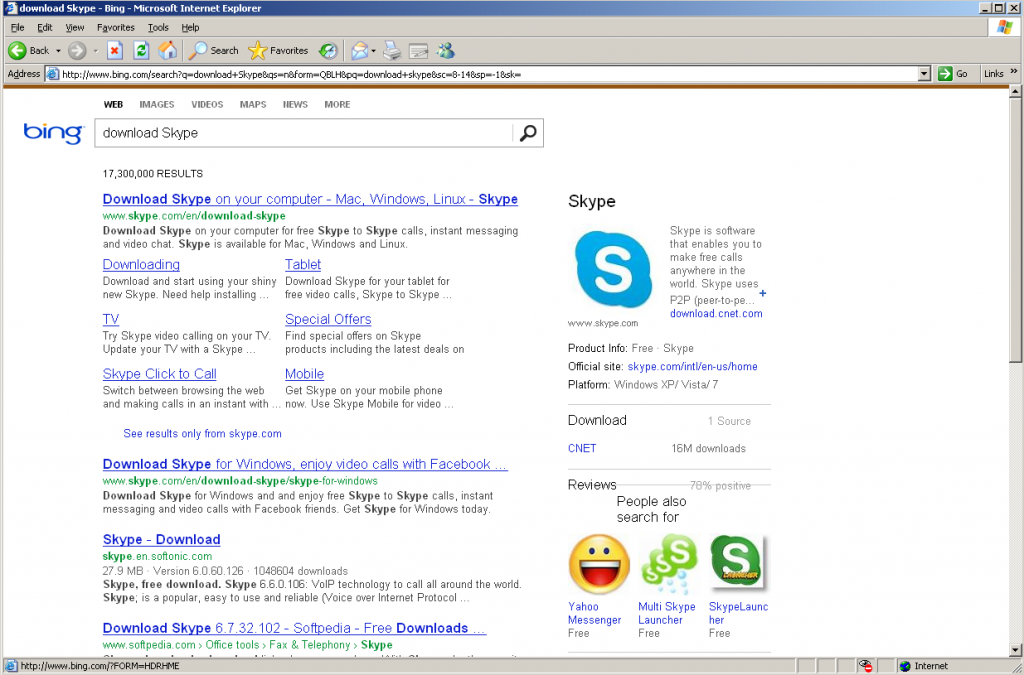
Let’s have a look at Bing next. Since both Skype and Bing are Microsoft products, the first two search results are for the official download links:
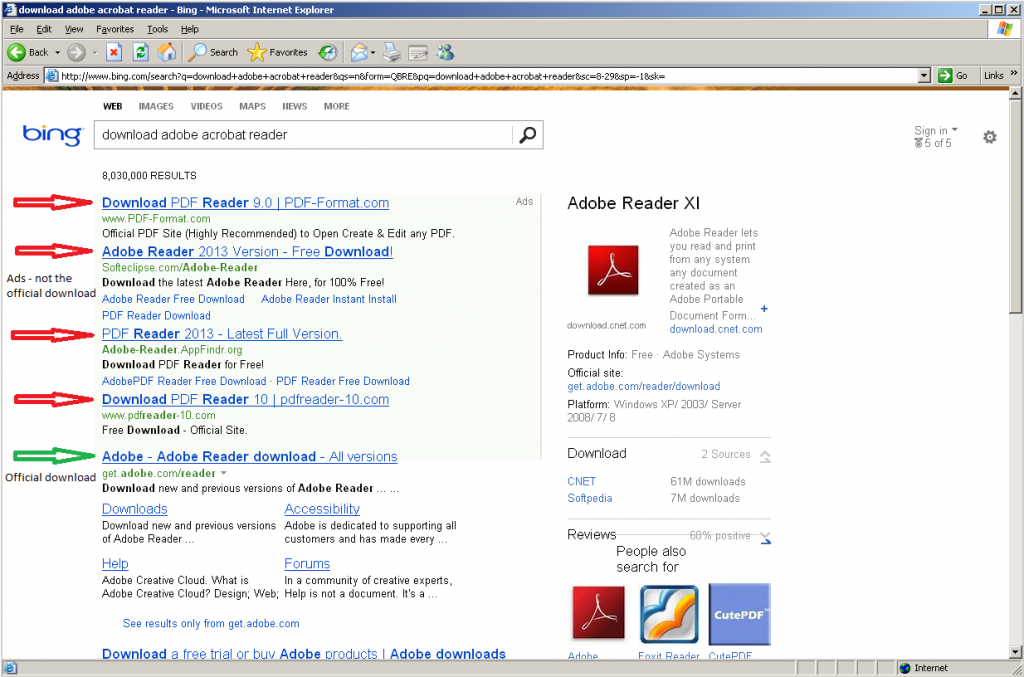
For a better example of Bing results, let’s search for Adobe Reader by searching for “download adobe acrobat reader.” This one is also pretty easy to spot since the ads are clearly marked.
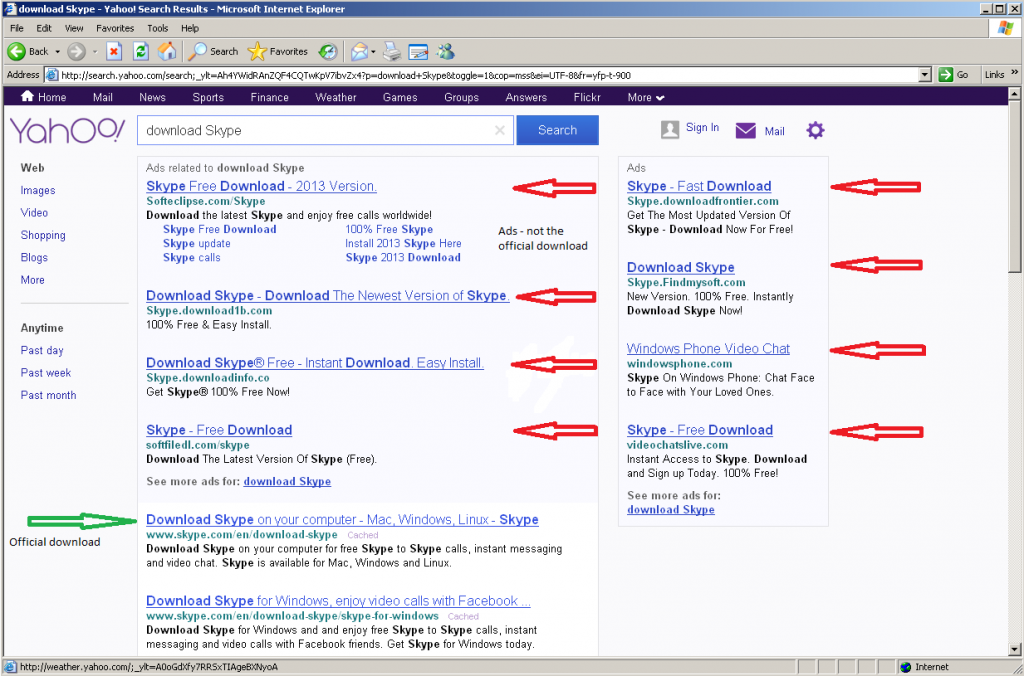
Now let’s have a look at the results for “download Skype” on Yahoo. Once again, the ads are clearly marked and the first actual result is the official download link.
Looking at these search results, you’ll notice a few things in common: The top results are all ads, and none of the ads point to the official download links, and the first actual link that is not an advertisement is the official download link. While this will not always be the case, it is common, and fortunately the three search engines we used in this example all do a very good job at identifying their advertisements. Does this mean that all ads are bad? Of course not! But when looking to download free software, the ads may not be your best choice. Also pay attention to the URLs, the official downloads are all on “skype.com” domains, while all the adds point to other domains.
Now you should have a better understanding of how some of those unwanted toolbars and search pages ended up on your computer, that clicking on the top result on a search page may not be the best way to go about downloading free software, and how to find the official download links for software on some of the most popular search engines. Pass this information onto others, and maybe you’ll save yourself a trip to a friend or family member’s house to remove an unwanted toolbar.