Based on historical evidence gathered during some of the major ‘opt-in botnet’ type of crowdsourced DDoS (distributed denial of service) attack campaigns that took place over the last couple of years, the distribution of point’n’click DIY DoS (denial of service attack) tools continues representing a major driving force behind the success of these campaigns. A newly released DIY DoS tool aims to empower technically unsophisticated users with the necessary expertise to launch DDoS attacks by simultaneously utilizing an unlimited number of publicly/commercially obtainable Socks4/Socks5/HTTP-based malware-infected hosts, most commonly known as proxies.
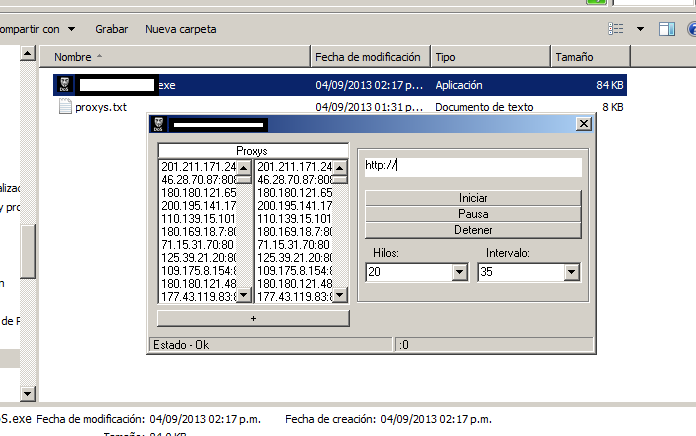
Sample screenshot of the DIY DoS (Denial of Service) tool:
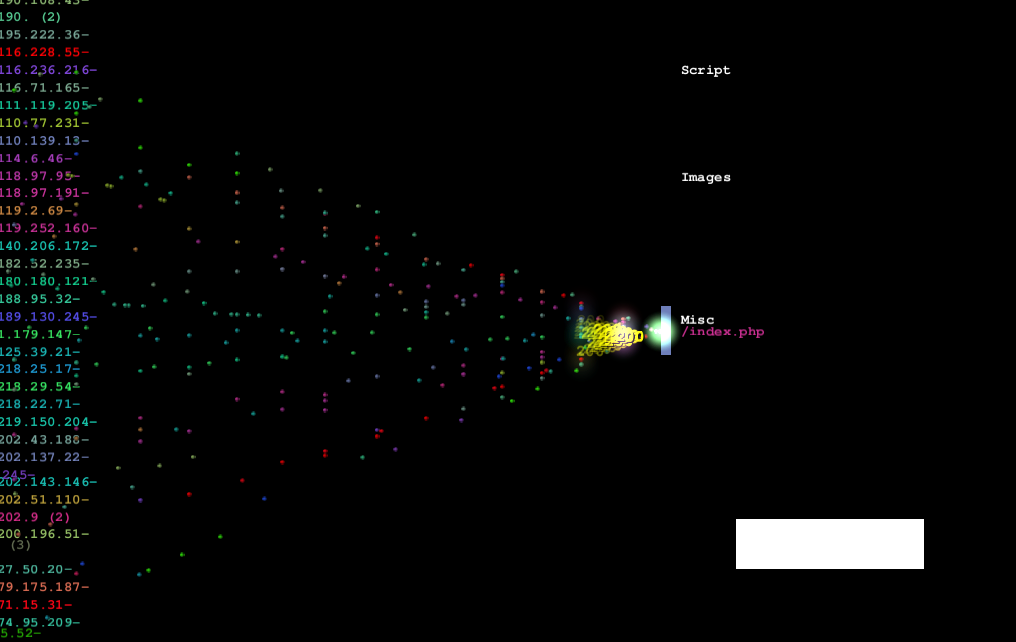
Sample visualization of the DIY DoS (Denial of Service) tool in action using logstalgia:
Despite the fact that the tool lacks diverse DDoS attack methods, as well as a Web-based/server based C&C (command and control) infrastructure, it can still prove to be a powerful tool in the hands of tens of thousands of users recruited/socially engineered into participated in a crowdsourced DDoS attack campaign. Especially in combination with the fact that we continue to observe new market entrants into the market segment for malware-infected hosts converted to Socks4/Socks5/HTTP proxies. As always, we’ll be keeping an eye on its future development, and post updates as soon as any significant updated get introduced.