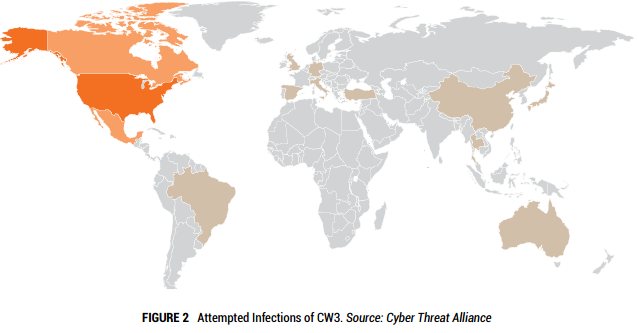
We know that Cryptowall 3.0 has been hugely successful for the cybercriminals netting them nearly $325 million in its debut year. With over 800 command and control URLs and over 400,000 attempted infections it is easily the most prolific threat of 2015.
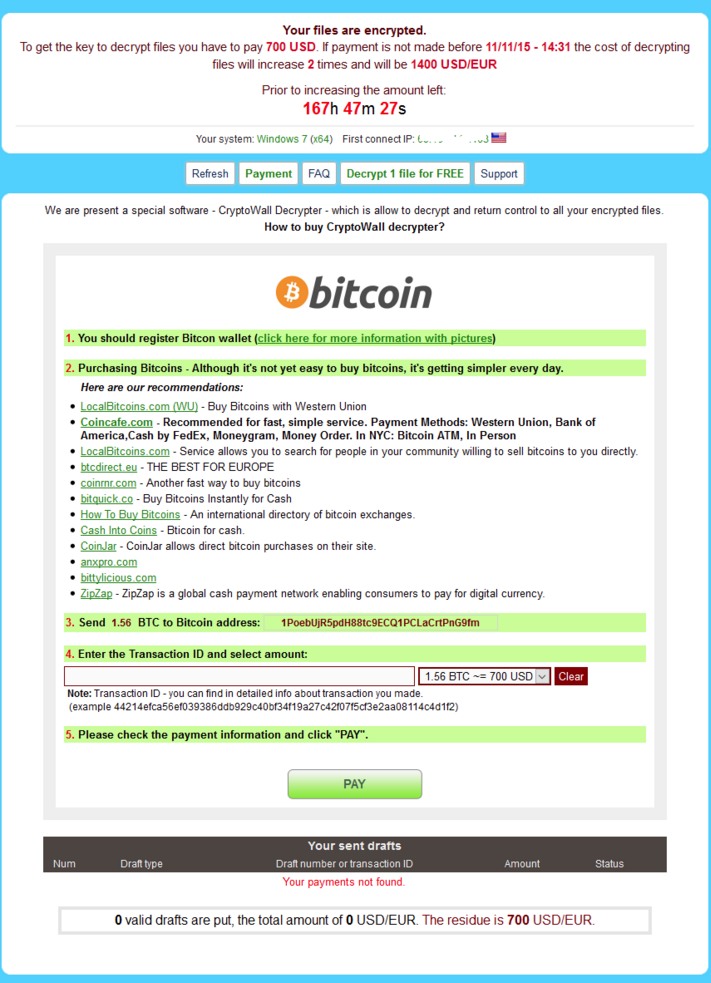
Here it is, what we’ve all been waiting for – the newest edition of Cryptowall. This ransomware comes out with new revisions almost as much as Apple does with iPhones. The bad news is that both will set you back $700.
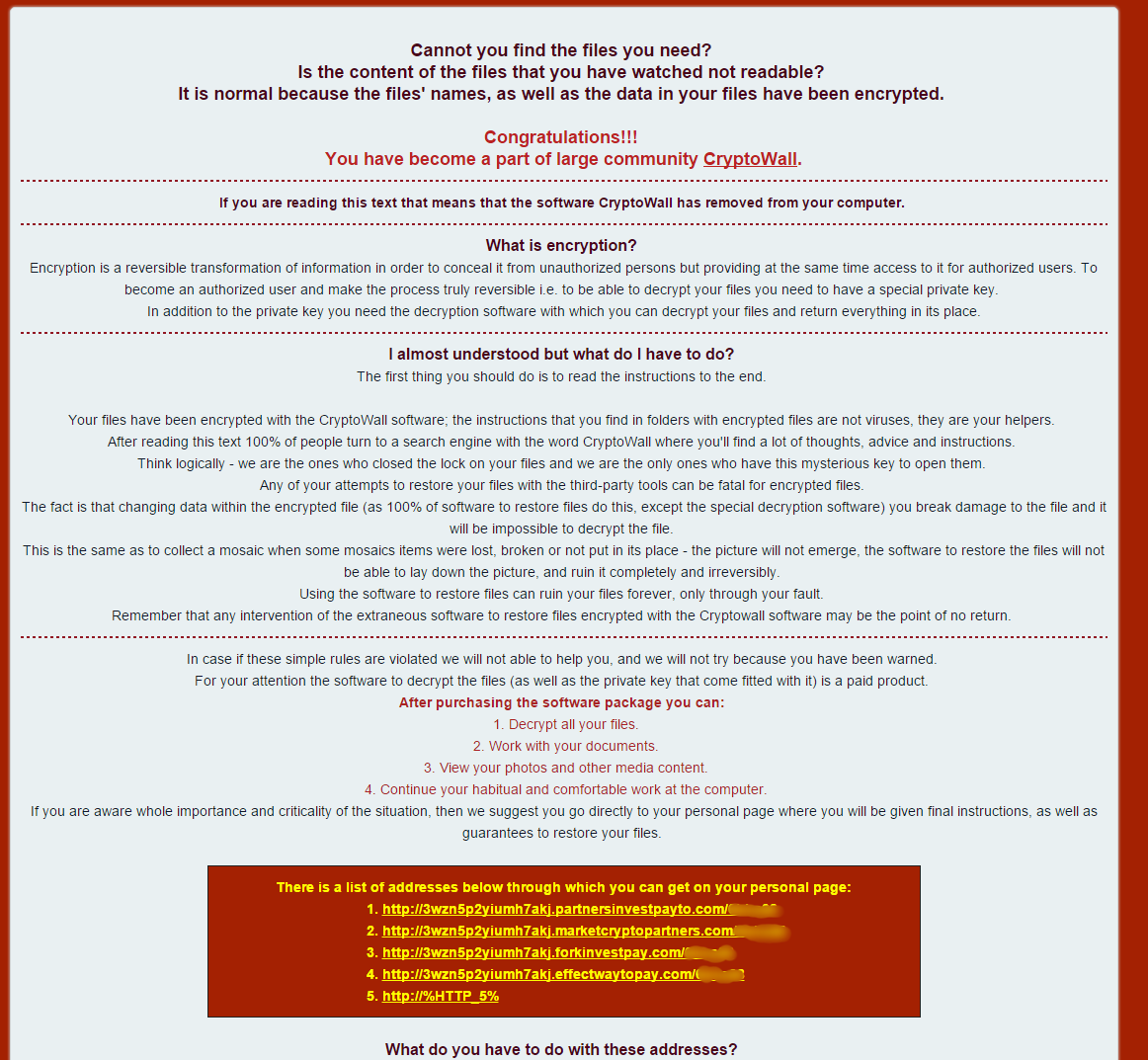
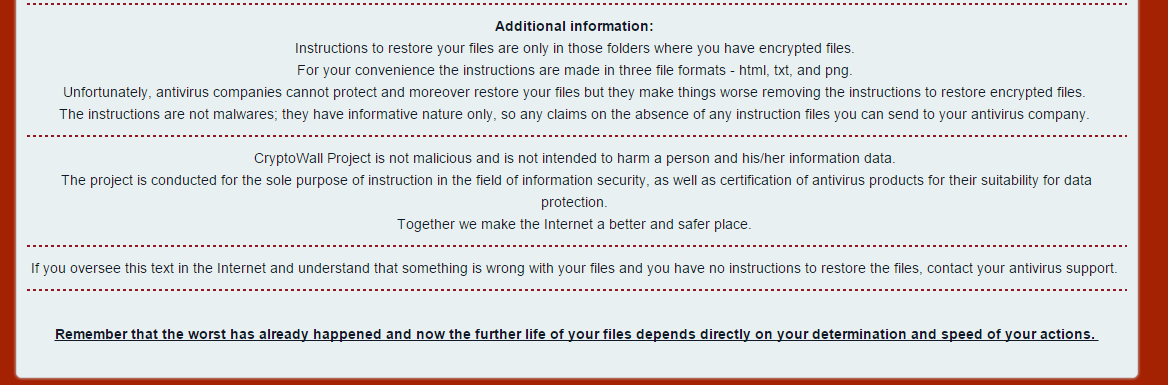
This is the locally saved html web page that it sends you to. If you don’t notice that, you’ll definitely notice that all your files have been encrypted and a new update is that the entire name of the file has been randomized so you no longer know which file is which. This is to create confusion on the severity of damage and increase the chance that you’ll pay out. As you can see from the first image they congratulate and welcome you to CryptoWall community – how nice. The rest of the instructions are pretty standard on informing you how install a layered tor browser and then connect to the darknet to pay them and get your files back. Notice the additional information they have at the bottom:
These guys actually claim that the CryptoWall is NOT malicious and not intended to harm your data “Together we make the Internet a better and safer place” – who are they fooling? Either way this is new and not seen on previous variants.
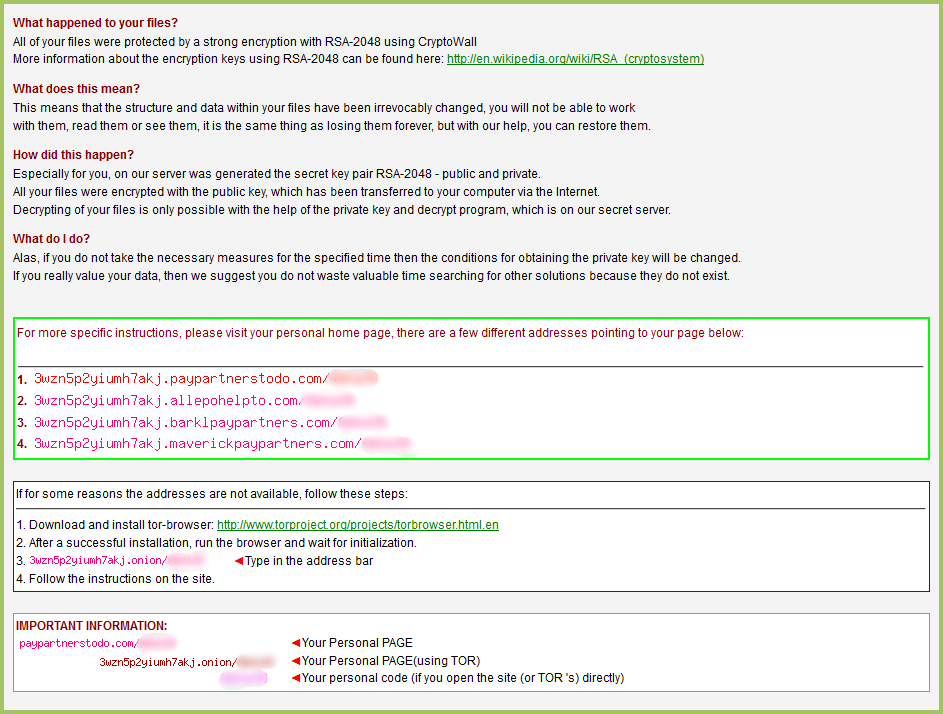
On to the payment website and and we can see they immediately want $700. It wasn’t even a year ago when the default payment was $300…
There are some new features like the a free decrypt which was first introduced by coinvault that we discovered a while back. It obviously has helped convince people that the decryption routine is fairly easy to get your files back and that the ransom is genuine and you will get your files back.
We’re currently reversing the sample and will have a more in-depth writeup of its infiltration, payload obfuscation, injection, and file encryption next week.
MD5 analyzed: E73806E3F41F61E7C7A364625CD58F65
Additional MD5 seen:
63358929C0628C869627223E910A21BF
5C88FCF39881B9B49DBD4BD3411E1CCF
32ACFA356104A9CE2403798851512654
CE38545D82858C7A7414B4BD660364A9
5384F752E3A2B59FAD9D0F143CE0215A
CF6D69E47B81FA744052DA33917D40F3
53C82D574E054F02B3163271262E0E74
A891CED376809CF05EFE4BB02EB2CBF3
5384F752E3A2B59FAD9D0F143CE0215A
Webroot will catch this specific variant in real time before any encryption takes place. We’re always on the lookout for more, but just in case of new zero day variants, remember that with encrypting ransomware the best protection is going to be a good backup solution. This can be either through the cloud or offline external storage. Keeping it up to date is key so as not to lose productivity. Webroot has backup features built into our consumer product that allow you to have directories constantly synced to the cloud. If you were to get infected by a zero day variant of encrypting ransomware you can just restore your files back as we save a snapshot history for each of your files up to ten previous copies. Please see our community post on best practices for securing your environment against encrypting ransomware.









Greetings from Colorado! I’m bored to tears aat work so I decided to check out your site on my iphone
during lunch break. I really like the imformation you present here and can’t
wait to take a look when I get home. I’m surprised at how quicck your blog loaded on my mobile
.. I’m noot even using WIFI, just 3G .. Anyhow, fantastic site!