 Phishing Trojans that try to remain below the radar are still prevalent, but a number of files coming through Threat Research point to a disturbing trend: Several new variants of existing malware families are taking a scorched earth approach to infected computers, rendering the PC unbootable (just check out the batch file at left for just one egregious example) once the malware has retrieved whatever data it’s trying to steal, or deliberately crashing it, repeatedly, if you try to remove it.
Phishing Trojans that try to remain below the radar are still prevalent, but a number of files coming through Threat Research point to a disturbing trend: Several new variants of existing malware families are taking a scorched earth approach to infected computers, rendering the PC unbootable (just check out the batch file at left for just one egregious example) once the malware has retrieved whatever data it’s trying to steal, or deliberately crashing it, repeatedly, if you try to remove it.
Since the middle of last year, we’ve seen a sprinkling of malware that also wipes out key files on the hard drive, sometimes preventing a reboot, after an infection. This isn’t hostageware, which overtly threatens to delete the contents of the hard drive if you don’t pay up, but something more sinister.
In some cases, the crashes we saw were the result of poor coding by the malware author. But increasingly it appears that this behavior is deliberate, and occurs without warning. And this unfortunate trend appears to be getting worse, leaving a raft of perplexed, angry victims unable to use their computers in the wake of an infection.
The commands within malware capable of rendering infected machines inoperable was first documented in detail last year. But recent files added to at least two of our definitions, Trojan-Downloader-Tacticlol and Trojan-Backdoor-Zbot, indicate that someone has begun to use this functionality.
Zbot
Many, if not most of the Trojans we investigate turn an infected computer into a node on a botnet. A computer on a botnet becomes a usable, rentable, or sellable asset to the person who controls the botnet. Bots can send spam, spread malware to other computers, engage in distributed denial-of-service attacks, serve as covert file storage areas, and a host of other undesirable activities.
The longer an infected PC remains infected and functional, the more the person or group controlling the botnet can do with it, and the more valuable it is. There is a financial disincentive for the botnet’s controller to terminate nodes on the network.
But Zbot isn’t like most botnet bots. It stays in communication with a centralized server, but it doesn’t do most of the other behaviors I listed above. The bot is remarkably efficient at stealing any saved credentials or other usable login data, then sending it onwards, within seconds of the infection taking hold on a PC. But that’s pretty much it.
After, say, two minutes post-infection, Zbot usually remains active, quietly logging any non-saved usernames and passwords a victim might enter into a Web form. But the fact is, most people instruct their applications and browsers to store usernames and passwords, so they don’t have to log into a Web site or application time and time again. It’s just easier that way. There’s a pretty severe case of diminishing returns from Zbots after the initial infection.
Several of our Threat Research and Advanced Malware Removal team speculated as to motives: Once Zbot has stolen the information it needs, these new variants may deliberately disable the PC as a distraction, making it more difficult for the victim to become aware that credentials were stolen and used until it’s too late.
In the case of these destructive Zbot Trojans, the system bluescreens soon after an infection. Because Zbot runs upon reboot, PCs infected with this variant go into a spasmodic reboot cycle. Booting from another device, like a boot CD, can permit a victim to remove the Trojan components (if you know where to look) and get back to work quickly. Less technically savvy victims are not so lucky.
Tacticlol
With the Tacticlol downloader, it’s not the spy itself but a downloaded payload that carries the seed of the PC’s destruction. Analysis of this particular spy took a long time because it won’t operate in a virtual environment, and I sent my test PC into death throes repeatedly.
Tacticlol — which arrives in your email inbox disguised as either UPS shipping information or some sort of Facebook account update — typically downloads at least one Rogue Antivirus payload when a victim unzips the attachment and runs the file. UPS shipping-confirmation spam and its ilk have been around the block a few times. The most recent flood of these downloaders began to hit inboxes in the past month. I’m still getting new ones.
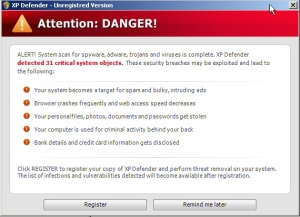
One of the spy’s payloads in this most recent distribution is a rogue called XP Defender. The rogue itself downloads additional payloads, some of which help it perform its curious brand of security theater.
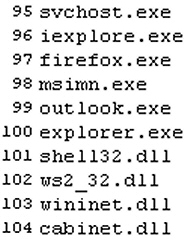
One of these payloads is a component which disables most common browsers, Outlook Express, and other Internet-enabled apps (a list of some of the apps and files it interferes with is below). It also contains within it a three-line batch file which, when run, deletes the NT Boot Loader file as well as the entire Windows directory and every system-critical file inside it. This not only renders the computer inoperable, but also requires a full Windows reinstallation (or, if you backed up an image of the drive with Acronis or Ghost, a reimage of the drive).
The program only executes the batch file when someone tampers with the component, so as long as you permit the rogue to harass you with bogus warnings, it won’t kill your computer. But it’s just a game of Russian roulette. Antivirus scans (from legitimate products) sometimes trigger the batch to execute, but at other times nothing happens and you can remove the file without problems.





















Lack of user education are the source of these attacks, if we execute our windows without administrative permissions, format as NTS and assign proper permissions, update our email client, in my opinion we never will suffer destruction of our PC.
-enrico the keylogger guy
Hi, Recently I had a w32 trojan rootkit virus that was delivered by fake ebay email. It changed nearly every file on my computer by changing their date to 08/04/2004 4:00am instead of 5:00am. Then it made computer unbootable…Hope this information helps out…IT also changed registry,making many settings locked.