 Is the team behind the Koobface worm taking a stance on the Israeli-Palestinian peace talks, or is this notorious worm’s most recent, bizarre twist just a coincidence?
Is the team behind the Koobface worm taking a stance on the Israeli-Palestinian peace talks, or is this notorious worm’s most recent, bizarre twist just a coincidence?
We’ve seen Koobface hijack legitimate Web sites for more than a year, using them not only to host malicious payload files, but also to work as proxy command-and-control servers for the botnet. One such hijacked Web domain, migdal.org.il, popped up in a number of blog posts and on Web sites which list the domains used to host malware, as far back as this past May, when the Koobface crew began using a slew of new hijacked servers as distribution points for its malicious files.
And since the summer, Koobface has been delivering a password stealing Trojan among the several payloads it brings down to an infected computer. That Trojan’s name is migdal.org.il.exe, and the stolen passwords it scrapes from infected computers are sent right back to the migdal.org.il Web server, which is physically located at an ISP in the UK.
Migdal also seems to be (if you can believe the content posted to the Web site) a French jewish organization that provides aid and resources to Israeli children and border guards, and whose leadership opposes many of the Israeli concessions that Palestinian negotiators have requested during the long peace process. Have the Koobface gang gone political, or are they just capitalizing on a convenient situation with an abandoned Web site?
(Update: The site went down on September 3rd, the day after this post went live. Thanks, helpful ISP who shall remain nameless.)
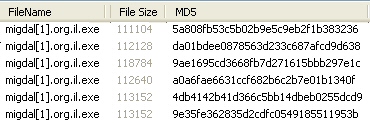
I took a closer look at the “Migdal” payload; It looks to me like a fairly conventional password stealer, in the same vein as SpyEye or Zbot, though it appears to be distinct from either of those more common Trojans. We’ve seen a bunch of these files show up as Koobface payloads in the past two months. All the samples appear to fall in the size range of about 110kb to 130kb.
On a test system, the Migdal Trojan stole some dummy passwords I’d entered into FileZilla, an FTP client application. Logs from various system monitors indicate the Trojan also searched the hard drive for other FTP clients (including Total Commander, TurboFTP and FlashFXP), and scoured the hard drive for Total Commander’s wcx_ftp.ini file, which that program uses to store FTP passwords.
It also retrieved dummy passwords stored in Firefox and Internet Explorer, and searched for (but did not find) the directory for both the standard installation of the Opera and the Opera 9 Beta browsers — something I hadn’t yet observed with either SpyEye or Zbot.
Once the passwords were retrieved by the Trojan, it submitted them to the Migdal server with an HTTP POST, generated a batch file to delete itself, ran the batch file, and was gone.
Here’s a look at that fake credential that’s a little easier to read (click for a full size pic):
So, not only have they hijacked the server to distribute additional malware, but they’re currently using it as a dead-drop for harvested stolen credentials.
The result of all this activity seems to be that the Migdal Web site has a very poor reputation, virtually across the board, from Webroot’s own reputation service, as well as those run by respected third parties such as SiteAdvisor, Web of Trust, Safe Web, and Google’s Safe Browsing (which feeds directly into Firefox). The site first appeared on a list of Koobface-hijacked sites listed on Dancho Danchev’s blog and on MalwareURL. We’ve tried repeatedly to contact the owners and the ISP which hosts the Web site, but so far we’ve received nothing but automated form letters in response.
So the question remains, is the Koobface gang merely taking advantage of a long-abandoned Web server to use it as a repository for stolen credentials, or is it abusing this server in particular to discredit this self-described “militant organization” that supposedly distributes flak jackets to children who live within missile-strike distance of Palestinian territories? Who knows? It’s certainly notable that the Koobface goons deliberately call attention to this particular domain name by naming the Trojan after the domain, but their motives are anyone’s guess.




















super
Nice post