 In September, I posted an item about a dropper which we call Trojan-Dropper-Headshot. This malware delivers everything including the kitchen sink when it infects your system. It has an absolute ton of payloads, any of which on their own constitute a serious problem. All together, they’re a nightmare.
In September, I posted an item about a dropper which we call Trojan-Dropper-Headshot. This malware delivers everything including the kitchen sink when it infects your system. It has an absolute ton of payloads, any of which on their own constitute a serious problem. All together, they’re a nightmare.
Among the payloads, we’ve seen this monstrosity drop downloaders (Trojan-Agent-TDSS and Trojan-Downloader-Ncahp, aka Bubnix), adware (Virtumonde, Street-Ads, and Sky-banners), keyloggers (Zbot and LDpinch), clickfraud Trojans (Trojan-Clicker-Vesloruki and at least three other generic clickers), and a Rogue AV called Antivir Solution Pro. So this is one nasty beast that has no qualms about using the shotgun approach to malware infections.
But we also noticed that it has added yet another intriguing installer to its panoply of pests: It’s a small executable named seupd.exe (search engine updater?) that makes two minor (but obnoxious) modifications to Firefox. The result of these modifications changes the behavior of Firefox’s search bar, the small box that lets you send queries directly to search engines, located to the right of the Address Bar.
![]() The modifications are not immediately apparent unless you try to search Google for something, using either the Search Box or the Address Bar: Instead of sending your search to Google, the browser submits search queries to one of six different domains not owned by Google, but which appear to use the Google API to provide results — and, presumably, earn a little ad revenue on the side.
The modifications are not immediately apparent unless you try to search Google for something, using either the Search Box or the Address Bar: Instead of sending your search to Google, the browser submits search queries to one of six different domains not owned by Google, but which appear to use the Google API to provide results — and, presumably, earn a little ad revenue on the side.
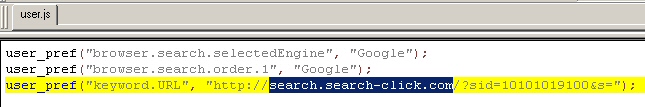
The modifications add a file named user.js to the currently logged-in user’s Firefox profile. The presence of a file by this name is not necessarily an indication of an infection, but in this case, the user.js file contains the instructions that tell the browser where it should submit searches when you have Google set as the default engine to use in the Search Bar’s dropdown menu.
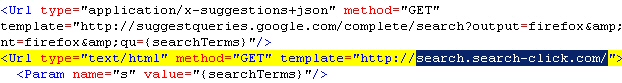
In addition, the Trojan drops a file named google_search.xml into the searchplugins directory beneath Firefox’s Program Files directory, and deletes the google.xml file that is normally there. It’s kind of slick because it maintains Google’s “suggest queries” feature to help you refine search terms in the Search Bar.
It also, unexpectedly, changes the icon that represents Google in the dropdown menu to an older version of the “G” than the icon used in a contemporary installation of Firefox. Here’s what the Google icon looks like in Firefox 3.6.x:
And here’s what it looks like on Firefox 3.6.x when the infection has taken hold. This is the same icon that Google used in Firefox 2.x for the Search Bar.
The tiny icon is embedded in the body of the xml file as base64-encoded text.
On an infected machine, search queries sent through either the Address Bar or the Search Bar are submitted to a subdomain of one of six different domains, depending on the installer you get: good-search.net, search-click.com, search-go.net, search-star.net, search-tab.com, or wish-search.com. The results look almost indistinguishable from a conventional Google search. All six are hosted on the same IP address, which makes them easy to block.
A couple of other vendors call this thing Gleishug, though I can’t figure out why this name was chosen. The word doesn’t appear to refer to anything in the internals of the file, and the only anagram of Gleishug that makes sense to me (at least as far as being obnoxious goes) is I Hug Legs. We’ve decided to go with the name Trojan-Gleishug for the sake of consistency with other vendors.
We remove the components and block the domains and their related IP addresses, but if you’re infected with this thing, it’s easy enough to get rid of manually: Just install Firefox over the top of itself, and the installer will replace the modified files with the originals. If you open up your user.js file and see anything resembling this screenshot, just delete that user.js file. The malware won’t reinfect your machine, so this is the easiest way to clear up the hijack.




















An example of malware getting smart – not completely destroying a system, but using it to get a little something on the side…