Who said there’s such a thing as a trusted Java applet?
In situations where malicious attackers cannot directly exploit client-side vulnerabilities on the targeted host, they will turn to social engineering tricks, like legitimate-looking Java Applets, which will on the other hand silently download the malicious payload of the attacker, once the user confirms he trusts the Applet.
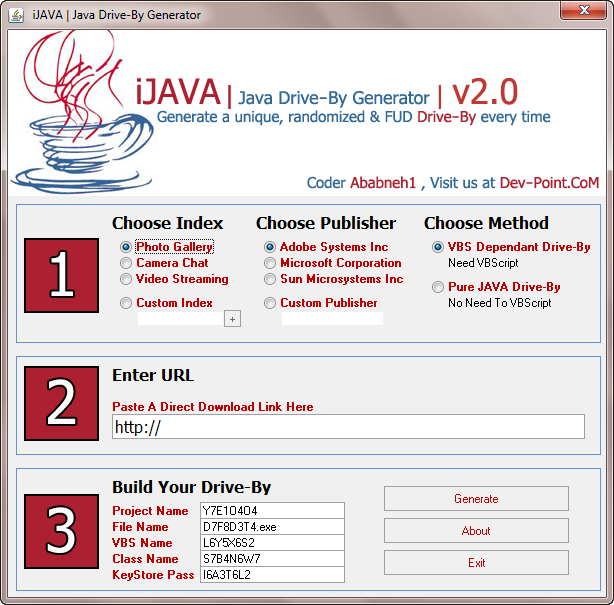
Let’s profile a DIY (do-it-yourself) malicious Java Applet generator currently available for download at selected cybercrime-friendly online communities:
Screenshot of the DIY malicious Java Applet generator:
By default, the DIY generator allows the creation of Java Applets mimicking a Photo Gallery, Camera Chat, Video Streaming, next to making it look like they’ve been issued by the following publishers – Adobe Systems Inc., Microsoft Corporation, and Sun Microsystems Inc. Naturally, they allow the use of Custom Publisher, making it fairly easy for a malicious attacker to impersonate a well known brand.
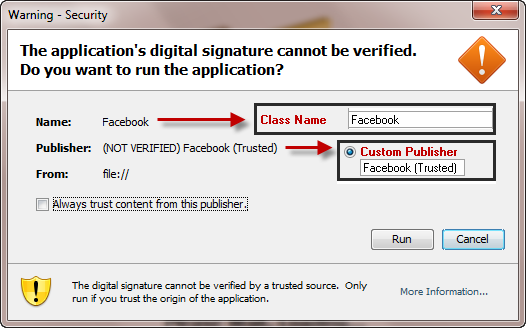
Here’s how a sample malicious Java Applet would look like, once generated:
As you can see, by default Java will notify the user that the publisher hasn’t been verified. However in this case, the malicious attacker simply used Facebook (Trusted) instead of just Facebook as a Class Name, attempting to socially engineer users into running the malicious Java Applet.
Users are advised not to execute unsigned Java Applets.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.







Glad I didn’t continue with McAfee which came as default on my Acer, but changed to Webroot, because this blog is great. It is very useful to be informed as well as ‘protected’. ‘Prevention is preferable to cure’ and a little knowledge goes a long way toward this! Thank you Dancho and thank you Webroot.