What happens once a cybercriminal has managed to obtain access to your credit card data by either compromising an insecure database, or through crimeware dropped on an affected host? Would he purchase blank plastic and holograms and embed the stolen data in an attempt to cash out as much money as possible, or would he look for alternative “risk forwarding” tactics to earn revenue while preserving his security and anonymity in the process?
It depends on the cybercriminal in question. In this post, I’ll profile a recently launched E-shop offering complete access to stolen credit cards data primarily belonging to U.S citizens.
More details:
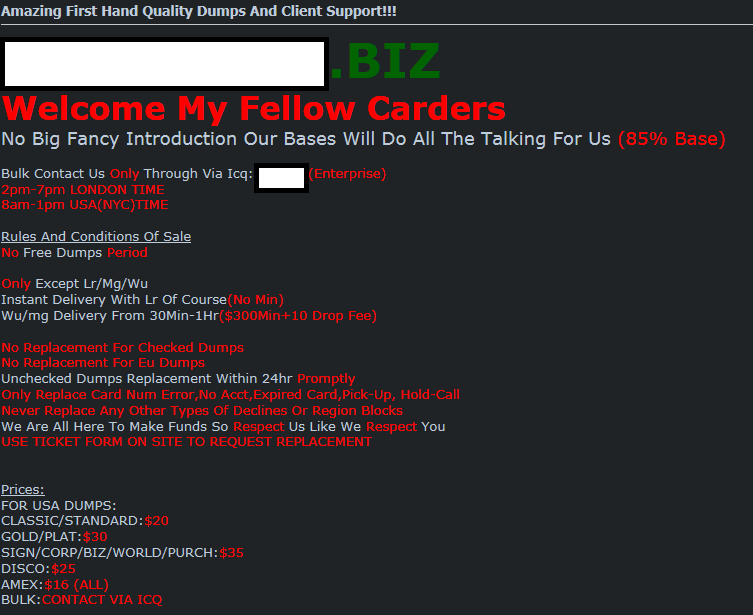
Sample screenshot of a forum advertisement promoting the service:
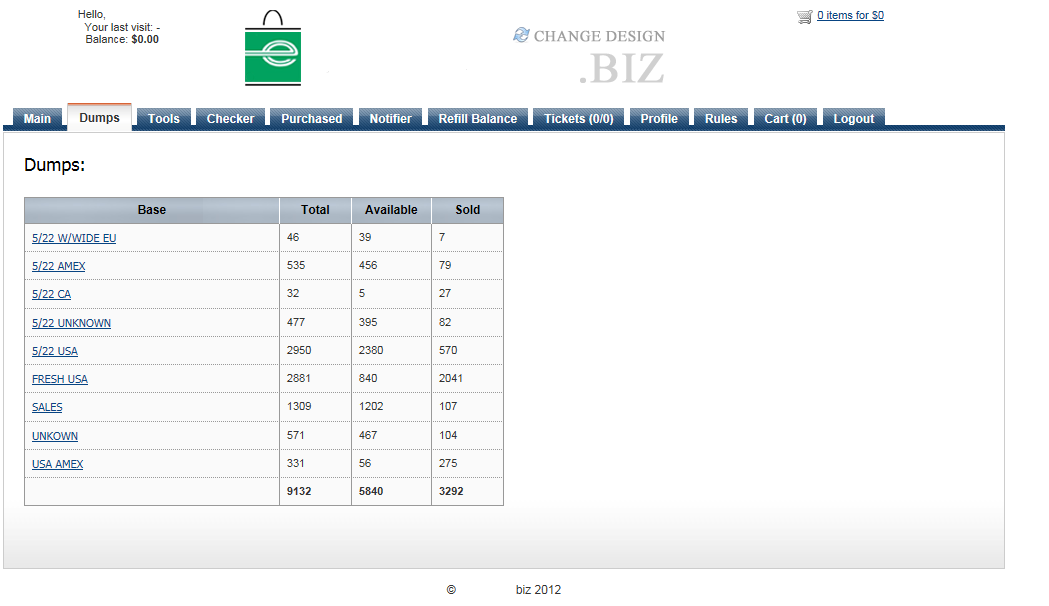
Once prospective cybercriminals register at the service, they’re exposed to a visually appealing menu:
- Related resources: If you’re interested in knowing more about the market for stolen credit cards data, consider going through my research “Exposing the Market for Stolen Credit Cards Data” published on October 31st, 2011.
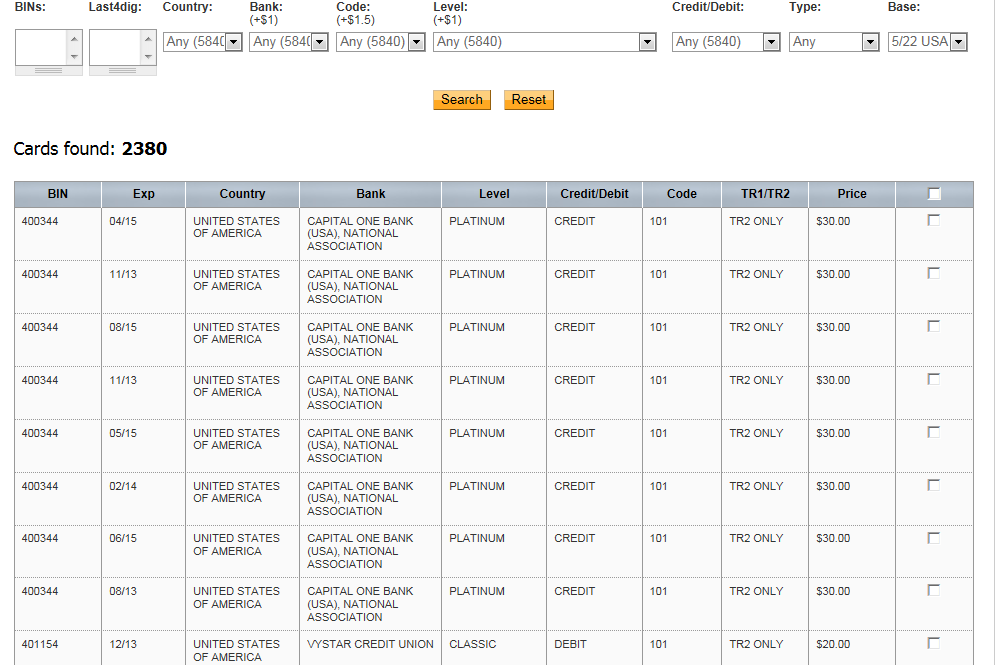
Sample stolen credit card databases available to prospective customers:
As you can see in the above screenshot, the service is currently offering 9,132 stolen credit cards for sale, and has already managed to sell 3292 credit cards to prospective cybercriminals. What’s the going rate for a sample stolen credit card? Depends on whether the card is debit or credit.
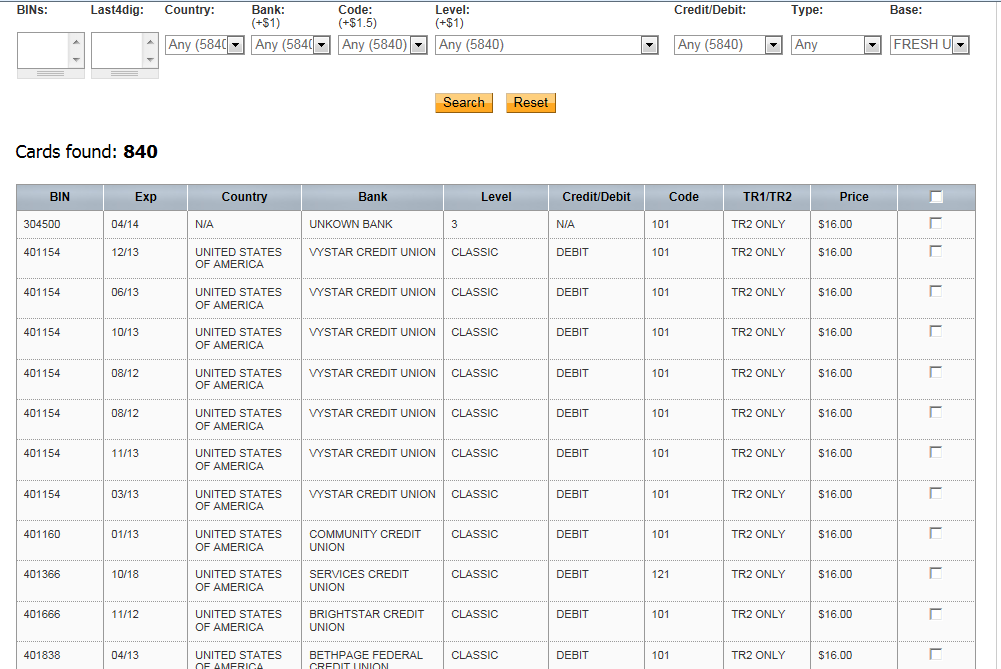
Sample listing of currently available stolen credit card details:
The prices vary based on the type of credit card. Debit cards go for a static $16, and credit cards go for a static $30 per item, with the service promising discounts for bulk purchases.
The service is also offering a well-developed search engine, allowing potential cybercriminals to better find what they’re looking for. A logical question emerges when you take into consideration the static prices for the stolen credit cards. Just like in a previous case of a vendor of compromised accounts selling a stolen credit card with a balance of $6,000 for $135, in this case we also have static prices for a dynamic asset whose actual account balance may be in the thousands. Why would a cybercriminal sell access to a stolen credit card details for such a low price, given that the actual balance of card may outpace his original price a thousand times?
Pretty simple. The practice is called “risk forwarding” which intersects with the E-shop’s owner desire to achieve instant financial liquidity of his assets. Instead of manually verifying the balance of the cards, he’s focused on bulk orders and forwarding the risk of getting caught to the prospective customers of his services.
We’ll continue monitoring the development of the service.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.









what an idea of selling stolen credit cards.is really they are working for online shopping.i want to see its usage.if card having money how mouh percentage money you except.