For years, cybercriminals have been trying to capitalize on the multi-billion dollar PC gaming market. From active development of game cracks and patches aiming to bypass the distribution protection embedded within the games, to today’s active data mining of a botnet’s infected population looking for gaming credentials in an attempt to resell access to this asset, cybercriminals are poised to capitalize on this market.
What are some current trends within this market segment, and how are today’s modern cybercriminals monetizing the stolen accounting data belonging to gamers internationally? Pretty simple – by automating the data mining process and monetizing the results in the form of E-shops selling access to these stolen credentials.
In this post, I’ll profile a recently launched Russian service selling access to compromised Steam accounts.
More details:
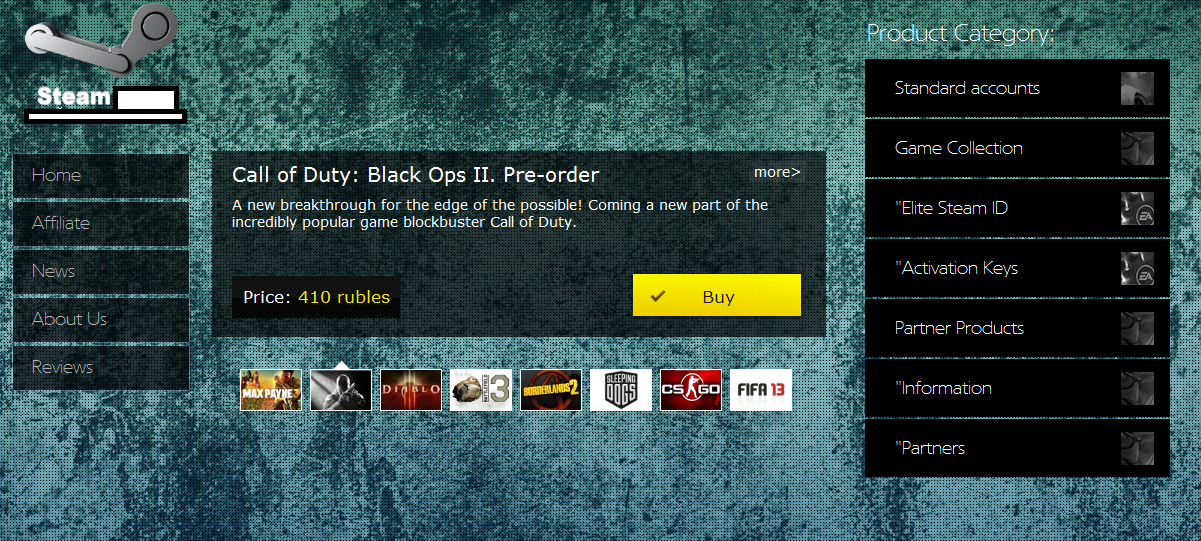
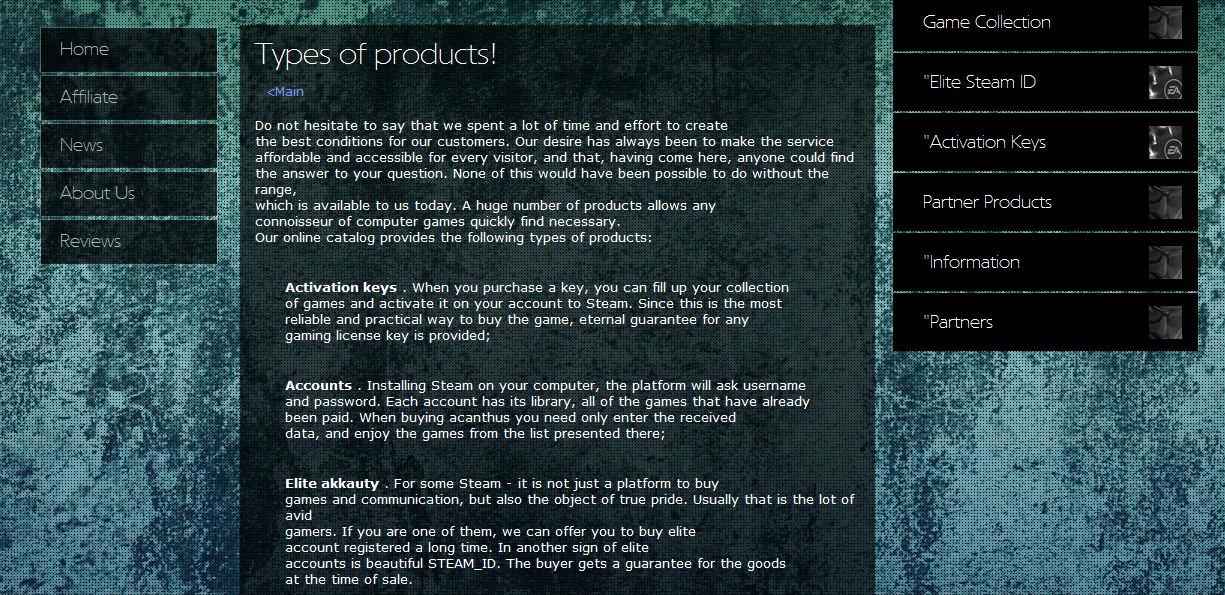
Sample screenshot of the Russian service selling access to compromised Steam accounts:
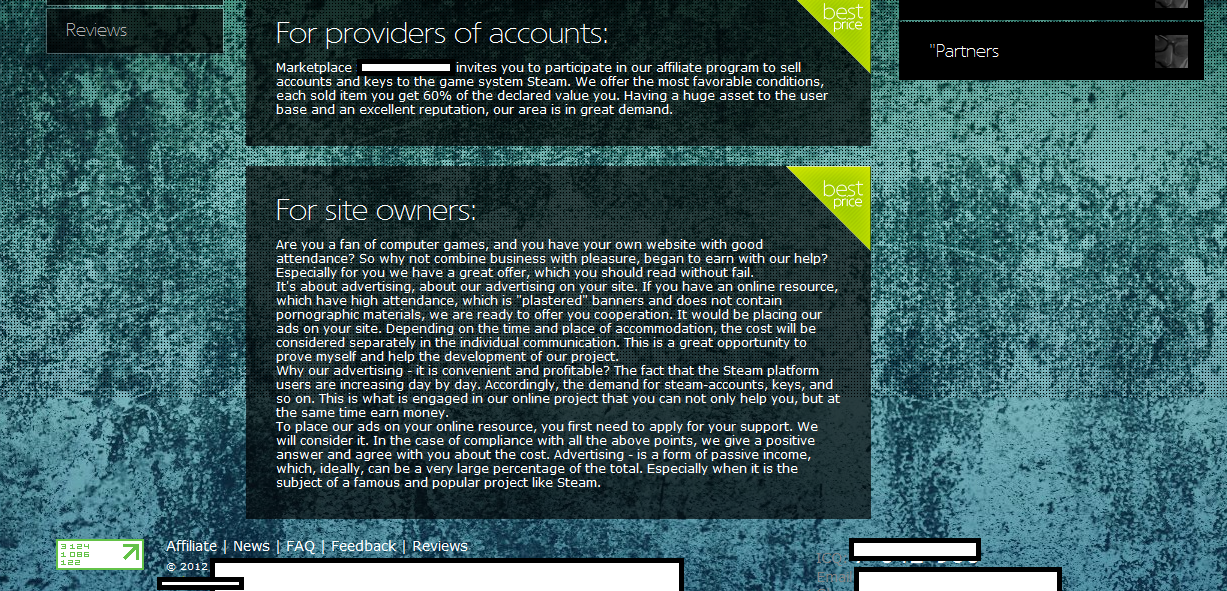
The service offers access to Standard accounts, Elite Steam IDs, activation keys, and most interestingly, the opportunity to resell access to these fraudulently obtained assets, through an affiliate network. Let’s take a peek at its inventory of fraudulently obtained assets.
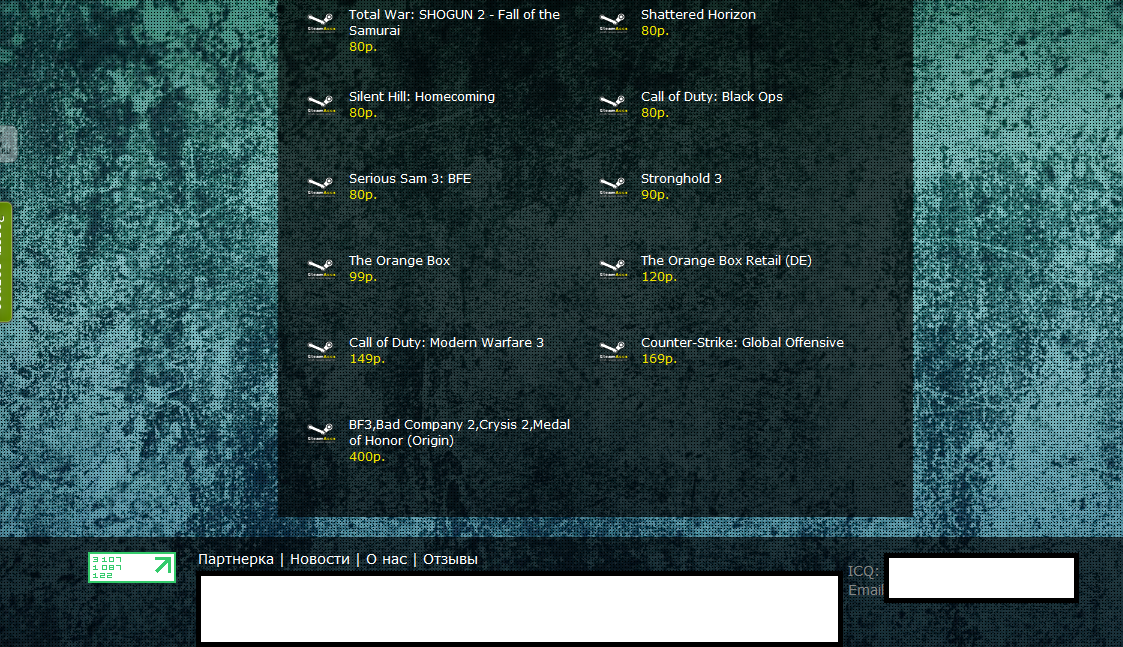
Second screenshot of the Russian service selling access to compromised Steam accounts:
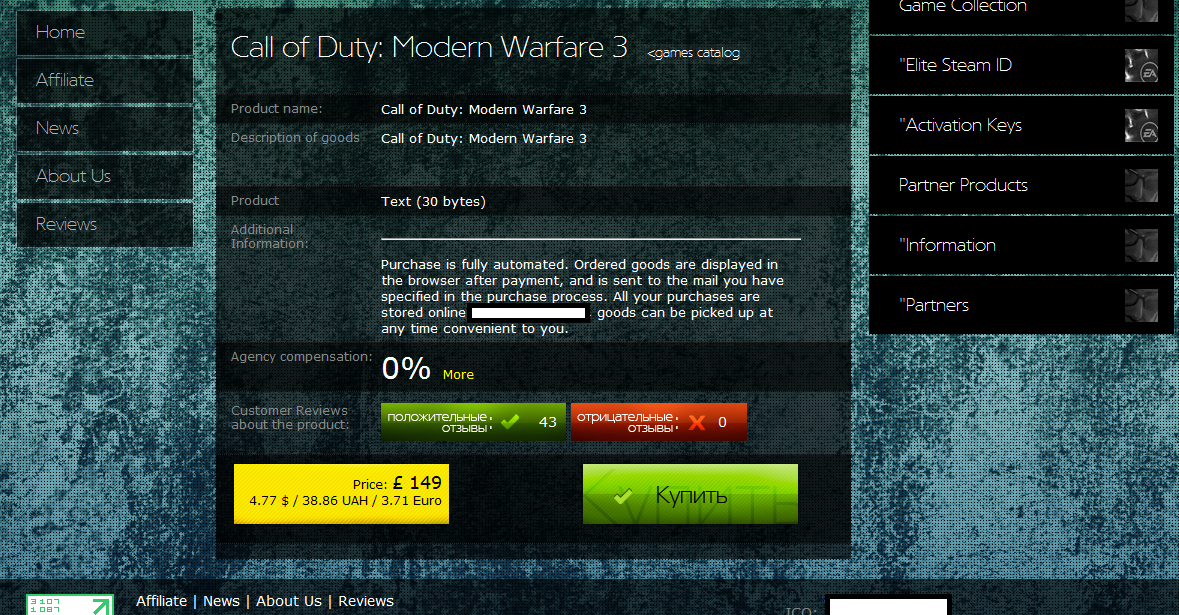
Third screenshot of the Russian service selling access to compromised Steam accounts:
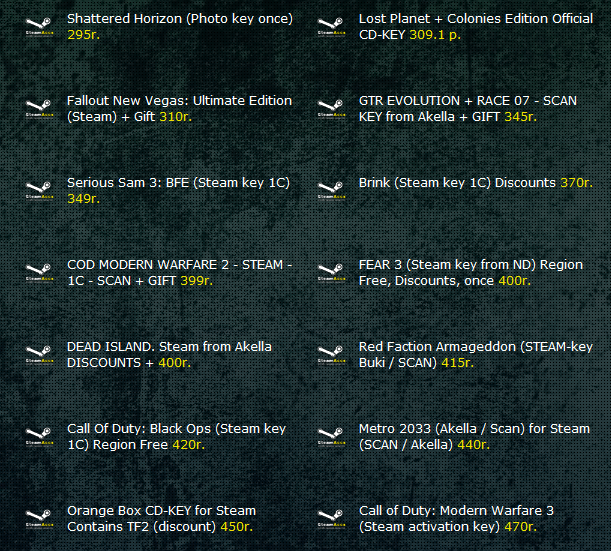
Fourth screenshot of the Russian service selling access to compromised Steam accounts:
Fifth screenshot of the Russian service selling access to compromised Steam accounts:
Sixth screenshot of the Russian service selling access to compromised Steam accounts:
Seventh screenshot of the Russian service selling access to compromised Steam accounts:
This service is a great example of a concept called “malicious economies of scale”. Thanks to the purchase automation of fraudulently obtained assets, next to a fully working affiliate network, the cybercriminals behind the service demonstrate a decent understanding of the monetization tactics applied by fellow cybercriminals.
We’ll continue monitoring the development of the service.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.