Largely driven by a widespread adoption of growth and efficiency oriented strategies applied by cybercriminals within the entire spectrum of the cybercrime ecosystem, we’ve witnessed the emergence and development of the mobile device market segment over the past few years. Motivated by the fact that more people own a mobile device than a PC, cybercriminals quickly adapted and started innovating in an attempt to capitalize on this ever-growing market segment within their portfolio of fraudulent operations.
In this post I’ll profile a DIY Mail-to-SMS flooder that’s abusing a popular feature offered by international and U.S based mobile carriers – the ability to SMS any number through an email message. The DIY SMS flooder exclusively targets U.S users.
More details:
What’s so special about the DIY Mail-to-SMS flooder that I’m about to profile in this post? Are the cybercriminals behind it innovating on the DIY SMS flooder front, or are they basically adapting to the situation in an attempt to cash in on the process? Let’s find out.
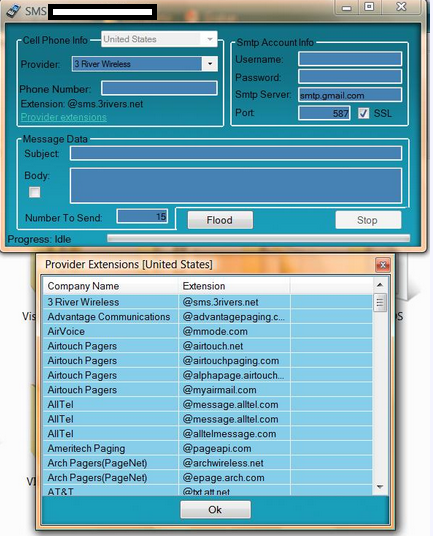
Sample screenshot of the DIY Mail-to-SMS flooder:
The DIY Mail-to-SMS flooder works fairly simply. And that’s the problem. On the majority of occassions, each and every mobile carrier offers the ability to receive an SMS message sent over email. The feature, Mail-to-SMS, is made possible thanks to the SMS gateways managed by mobile carriers. It works as follows – the mobile number of the potential victim is included in a sample email like mobile_number@sms_gateway.mobile_carrier. If the feature is activated for this particular number — and on the majority of occasions it is — then the user will receive the SMS message sent over email.
What the cybercriminals behind this flooder did is collect publicly obtainable information on U.S based mobile carriers, incorporate the details into the program, and allow anyone to launch SMS flooding attacks over SMTP (Simple Mail Transfer Protocol). The nasty feature is currently affecting the majority of U.S based mobile carriers, and with the program already leaked at several cybercrime-friendly online communities, it’s only a matter of time before it gets included into the arsenal of tools of a managed SMS flooding service.
Thankfully, the DIY Mail-to-SMS flooder doesn’t offer automatic rotation of SMTP servers, sender’s email, and randomization of the body of the message. It’s only a matter of time before these features get implemented.
We’ll continue monitoring the development of the tool, as well as the emerging abuse of the mobile device market segment within the cybercrime ecosystem.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.







A great information in this blog. mail to sms is the best way to communicate in now days. I also used to communicate my friends by this platform.