On a daily basis, largely thanks to the efficiency-centered malicious campaigns circulating in the wild, cybercriminals get access to tens of thousands of accounting credentials across multiple Web properties, and most disturbingly, online payment processing services like PayPal.
We’ve recently spotted a newly launched underground E-shop that’s exclusively selling access to hacked PayPal accounts. How much does it cost to purchase a hacked PayPal account on the underground marketplace these days? What pricing method is the cybercriminal behind the service using, and does the newly launched E-shop share any similarities with the E-shop selling access to hacked PayPal accounts that we profiled in 2012?
Let’s take a peek inside the E-shop.
More details:
Sample login page for the E-shop:
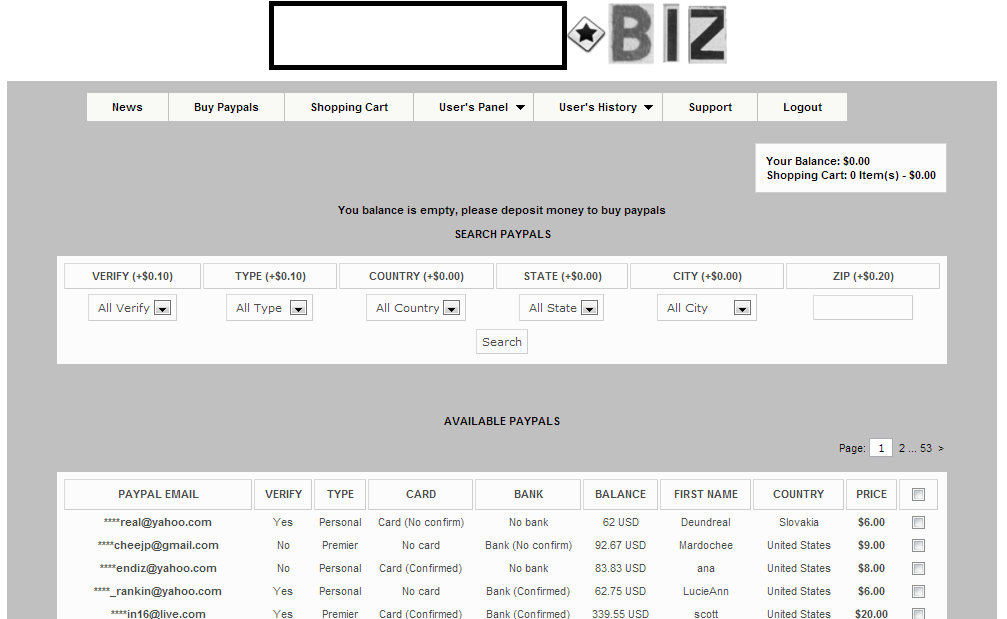
Sample entry page for the E-shop:
As you can see in the attached screenshot, the data is segmented in the following way: Email of the affected victim, verified/not verified account, type of account, Card confirmed or not, Bank confirmed or not, Balance, First name of the victim, the country of origin, and the actual selling price.
Screenshot of the inventory of the E-shop:
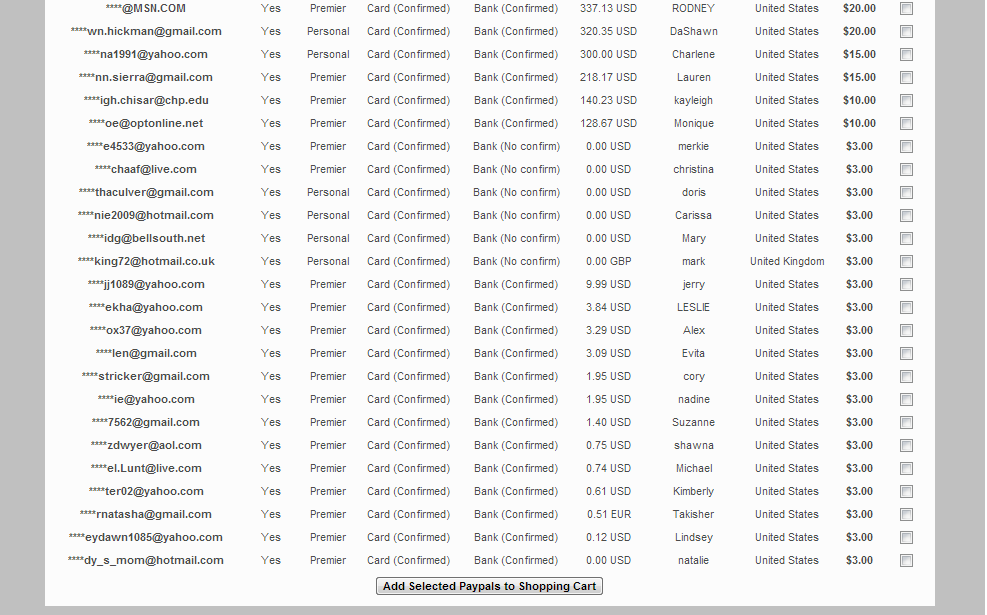
What about the prices? As you can see, accounts with virtually no assets — at least for the time being — are offered for sale at a static $3 per account. The price for accounts with a balance varies between $20-$15. It’s pretty obvious that the cybercriminal behind the E-shop is using perceived value for his pricing scheme, in the same way as another cybercriminal whose operations we profiled in 2012. Back then, he was selling access to a compromised bank account with a balance of $6,000 for $165. What we’ve got here is a decent example of how these inexperienced cybercriminals are looking for ways monetize the fraudulently obtained data as soon as possible, instead of “cashing out” the accounts by themselves, which could lead to possible risks to their OPSEC (Operational Security).
Second screenshot of the inventory of the E-shop:
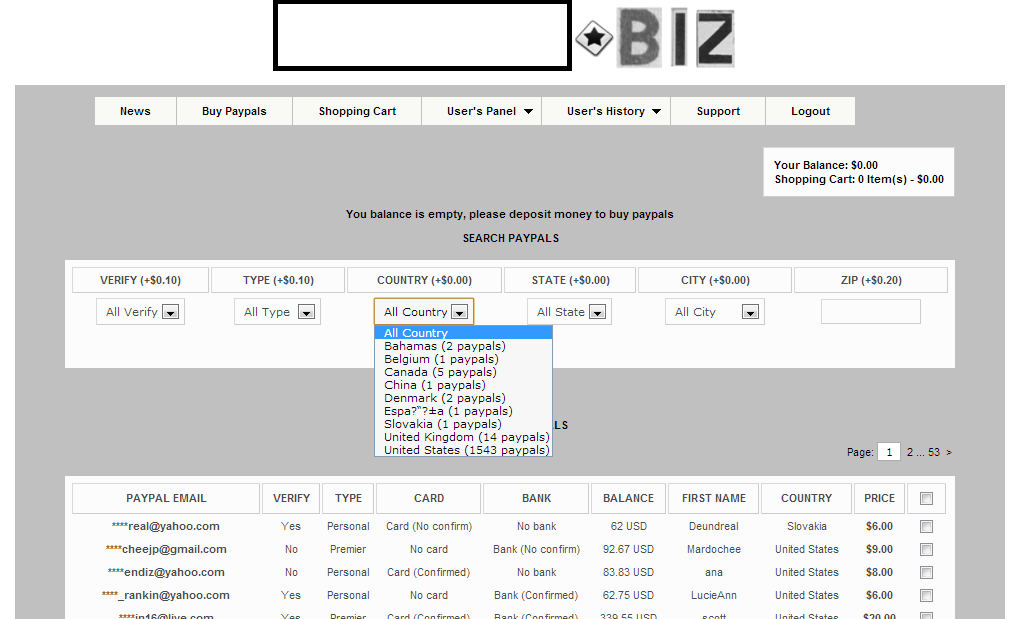
The E-shop is exclusively targeting United States citizens, and currently has an inventory of 1,543 hacked PayPal accounts, followed by another 14 for the United Kingdom.
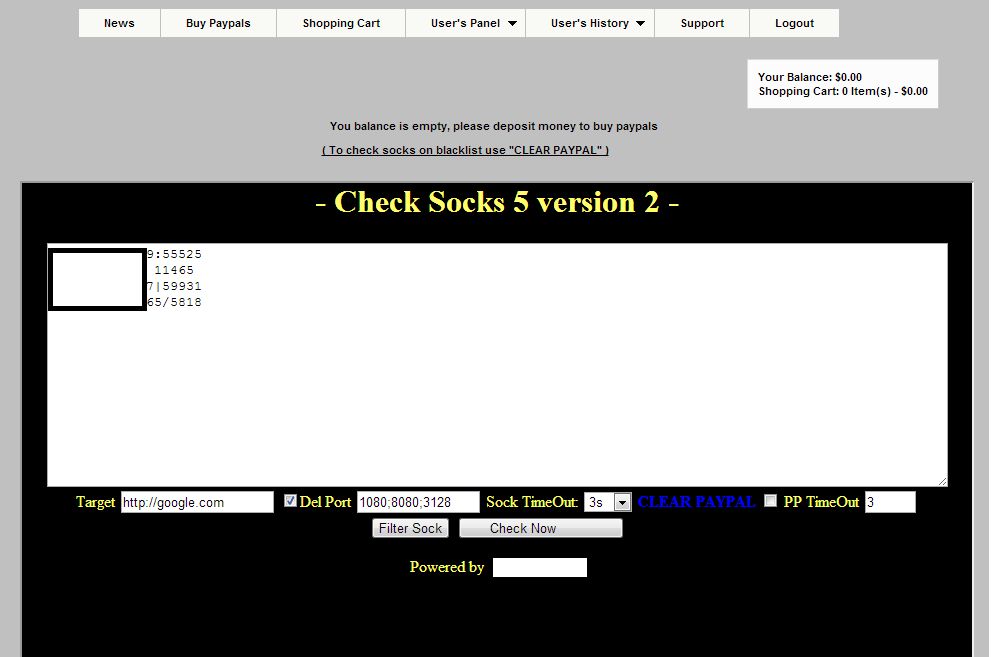
What’s particularly interesting regarding this E-shop is the fact that the cybercriminal behind it tried to come up with a value-added service, in this case a built-in Socks5 proxy checker, to be used when interacting with the hacked PayPal accounts for greater anonymity.
Sample screenshot of the built-in Socks5 proxy server checker:
These are not publicly obtainable Socks5 servers. Instead, they are compromised malware-infected hosts converted into anonymization proxies, allowing the cybercriminals who are about to “cash out” the hacked PayPal accounts to risk-forward the possibility of getting traced back to the IP of an innocent malware-infected victim.
How did the cybercriminal behind the service shape the prices for each hacked PayPal account? Pretty simple. Based on perceived value with asset liquidity in mind. Thanks to his inability/unwillingness to “cash out” the accounts by himself, launching an E-shop to monetize the fraudulently obtained financial data seems a logical development. Unlike the E-shop selling access to hacked PayPal accounts that we profiled in 2012, this one isn’t selling any other type of compromised accounting data, other than PayPal accounts.
We’ll continue monitoring the emergence of these E-shops, and post updates as soon as new developments take place.








Were to buy?!
This is so bad. They steal personal details, hack PayPal accounts then sell them to dark markets.