By Dancho Danchev
We have recently spotted a new underground market ad, featuring a new commercially available malware bot+rootkit based on the ZeuS crimeware’s leaked source code. According to its author, the modular nature of the bot, allows him to keep coming up with new plugins, resulting in systematic “innovation” and the introduction of new features.
What’s the long-term potential of this malware bot with rootkit functionality? Does it have the capacity to challenge the market leading malware bot families? What are some of the features that differentiate it from the rest of competing bots currently in the wild? What’s the price of the bot, and what are the prices for the separate plugins available for purchase? Let’s find out.
More details:
According to the bot’s author, all the command and control communications between the malware infected host and the C&C infrastructure are digitally signed (2048 bits), ensuring that only the botnet’s original owner, the one possessing the private key, can control the aggregated botnet. What’s particularly interesting about the bot is that it also includes a Domain Generation Algorithm (DGA), next to a rootkit functionality described in the following (translated from Russian) way:
The bot has a powerful rootkit functionality. The rootkit is presented as a driver, which is the process of protecting your data and if they change / remove the actual binary. It allows you to hide files on the disk, the branches in the registry, inject dll in a separate process and in all, provides a gateway through which the user applications can get a list of processes currently loaded kernel modules, terminate any process, to hide the list of dll modules loaded process.
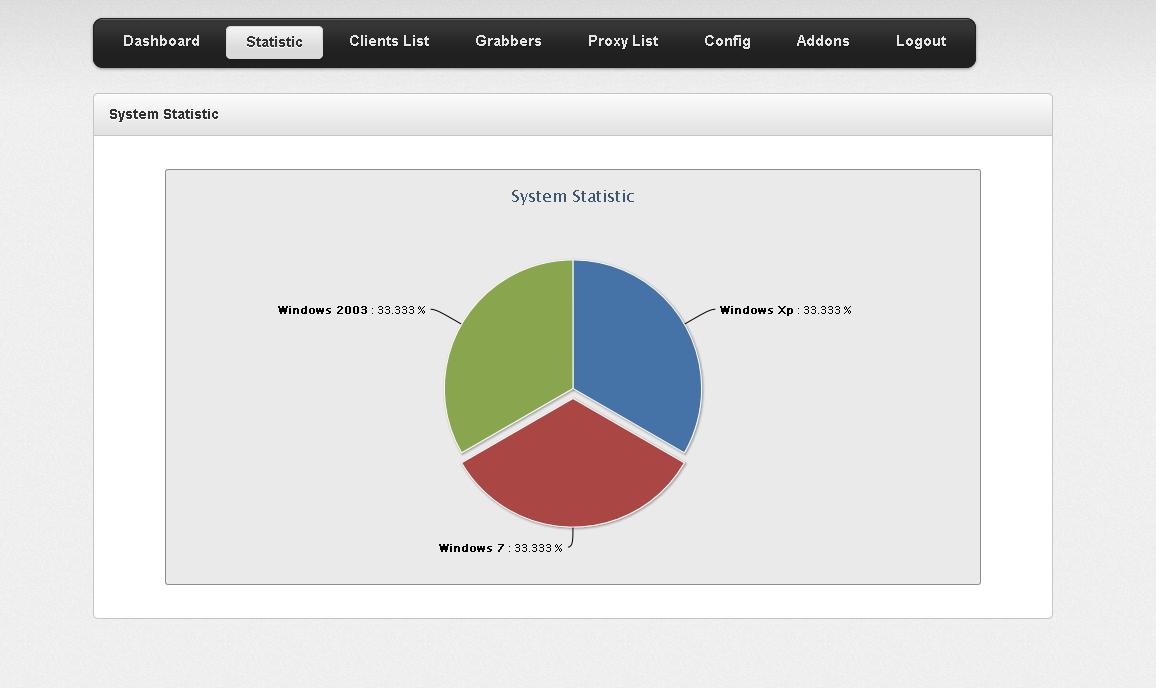
The malware bot also offers the ability for a cybercriminal to issue specific commands, like dropping a third-party piece of malicious code or using geolocation to only affect particular countries, regions, or cities. It also allows the cybercriminal to set intervals for C&C communication which can reduce the load on the C&C infrastructure and make detecting the malicious communication more difficult. According to the bot’s author, the rootkit functionality that he offers remains undetected by all the major antivirus vendors on the market. The bot supports Windows 2003/XP/Windows 7, but is not supporting x64 bit systems due to the way the rootkit works.
What about the currently available plugins and their prices? For the time being, the bot is compatible with the following plugins available as separate modules, which can be purchased individually. Naturally, the communication between the C&C infrastructure and the plugins is encrypted as well.
- DDoS module – price $350 – the number of tasks/goals is unlimited, and so is the number of threads, the interval between sending packets, and the actual packet size. For the time being the module supports HTTP (GET), UDP and ICMP type of flooding techniques, plus it allows the cybercriminal using it to change these settings on the fly.
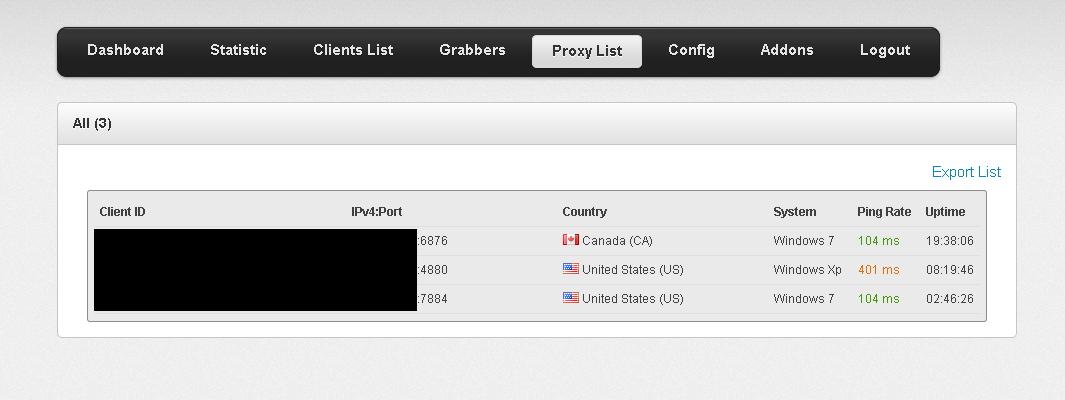
- Socks 4/5 module – price $120 – the plugin allows the cybercriminal behind the botnet, to easily convert the malware-infected hosts into anonymization proxies, a rather common module found within a lot of competing malware bots. The author of the bot also allows his customers to either specify the port of the Socks server, or the bot will choose one by random.
- HOSTS File Modifier module – price $50 – the plugin does what its title says. It’s worth emphasizing on the fact that in 2013, cybercriminals still attempt to exploit this noisy vector and abuse it for achieving their fraudulent objectives.
- Back Connect Hosts module – price $380 – yet another standard plugin available in competing malware bots, allowing the cybercriminals to connect and abuse hosts behind a NAT.
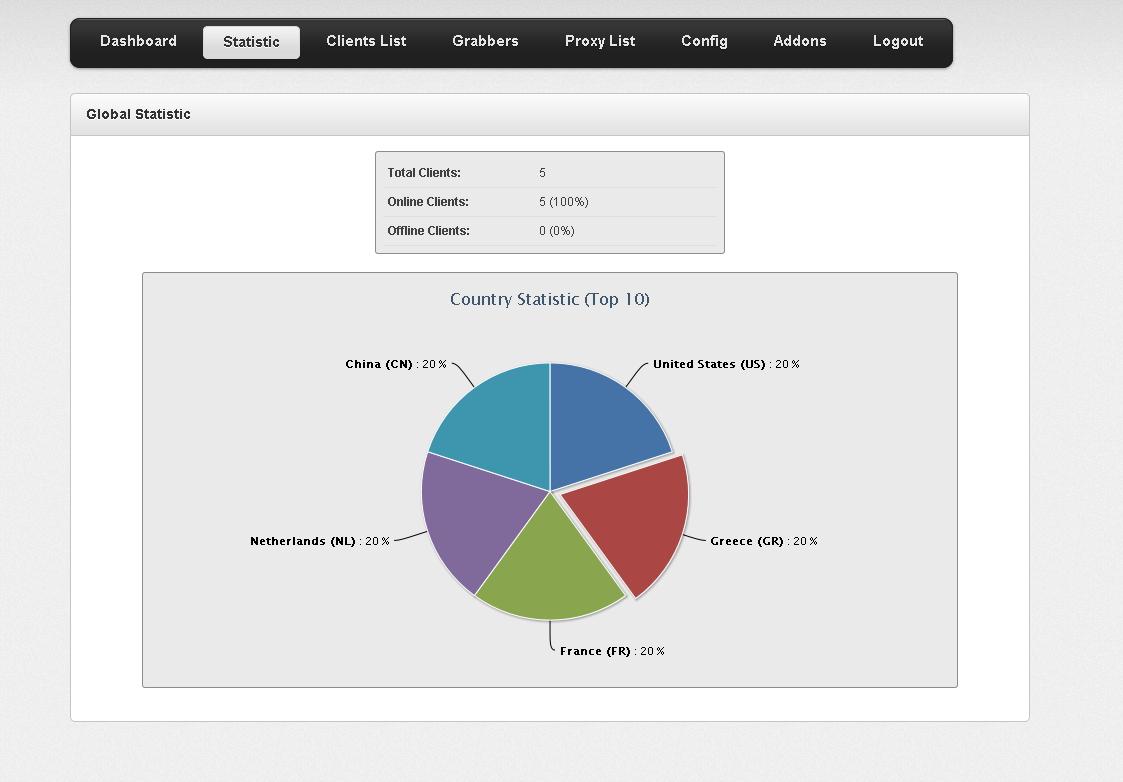
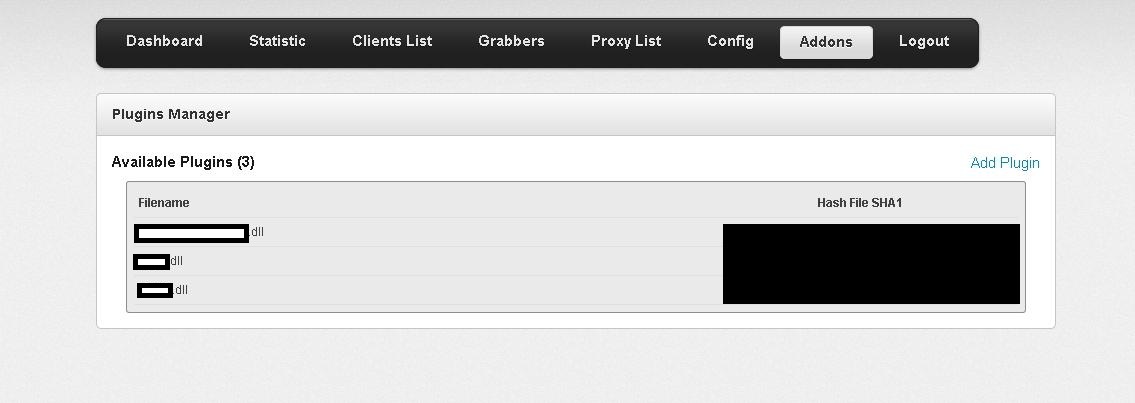
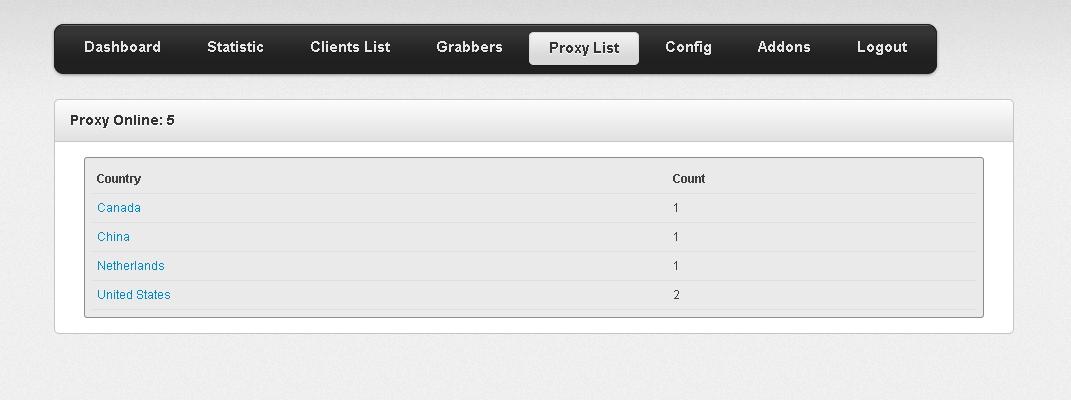
Sample screenshot of the ZeuS source code based rootkit:
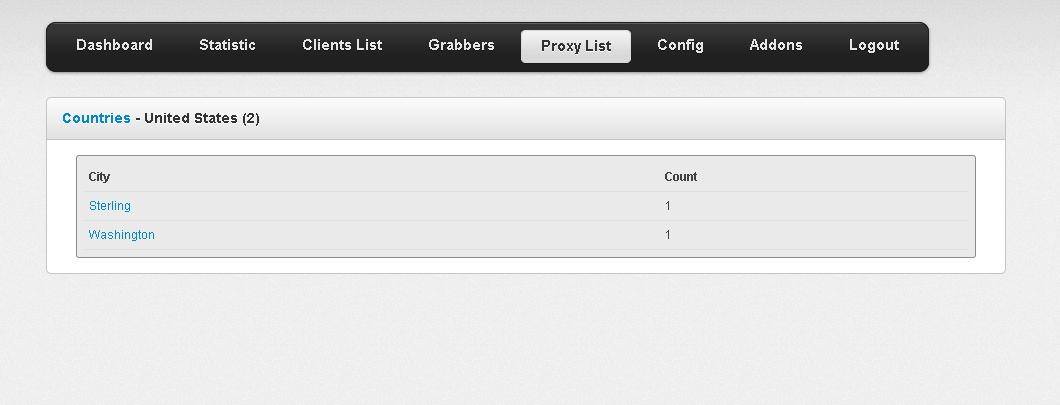
Second screenshot of the ZeuS source code based rootkit:
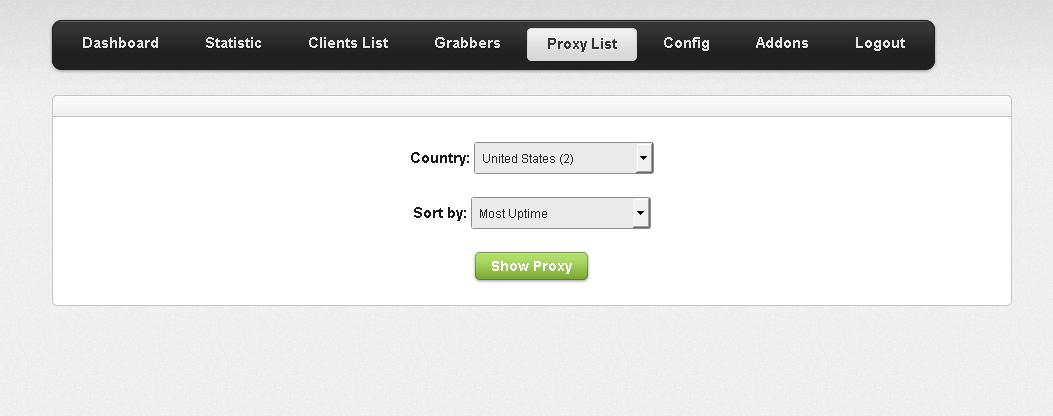
Third screenshot of the ZeuS source code based rootkit:
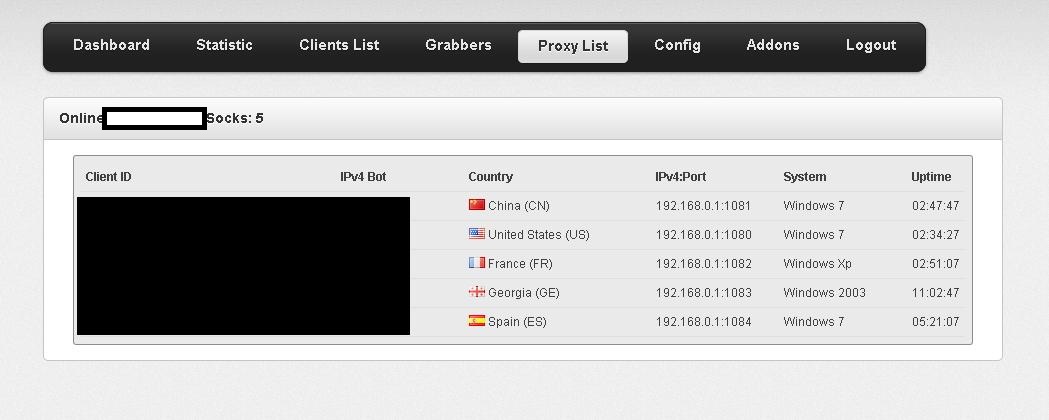
Fourth screenshot of the ZeuS source code based rootkit:
Fifth screenshot of the ZeuS source code based rootkit:
Sixth screenshot of the ZeuS source code based rootkit:
Seventh screenshot of the ZeuS source code based rootkit:
Eight screenshot of the ZeuS source code based rootkit:
Ninth screenshot of the ZeuS source code based rootkit:
The bot’s control panel is written in PHP using MySQL, and all the interactions with the admin panel are encrypted. Once executed, the rootkit is only available in the memory of the infected host, and no “physical” copy of it can be found on the affected host. The ZeuS source code based rootkit also encrypts the actual reports, so that even in case someone gains access to the C&C, the feature will prevent them from seeing the generated reports.
What about the price of the bot? $1,300 without the modules, or $1,500 for the modified ZeuS bot with rootkit functionality. It’s also worth emphasizing on the fact that the modified ZeuS bot is only sold with the rootkit. When a customer purchases this malicious underground market release, he gets a user’s manual including screenshots of how to use it, a video demonstration of the installation process, info on how to create digital signatures in order to control and secure the botnet, and finally a program for creating the actual signatures.
The author is trying to “play by the book” and is forwarding the responsibility for the logical fraudulent abuse of this release to the actual buyer, as the License Agreement explicitly says that the tool is meant to be used for testing the security of their own systems. How can you buy this underground market release? Interestingly enough, its author is only available for a chat on Sundays from 10:00 A.M, Moscow time. From Russia with “love”, that’s for sure.
We’ll continue monitoring the development of this rootkit+malware bot, and post updates as soon as new developments emerge.
To find more about Dancho Danchev, follow him on Twitter.







Nice post!
But I didn’t quite get the description of pricing: “$1,300 without the modules, or $1,500 for the modified ZeuS bot with rootkit functionality.”
What is it you get for $1300 if not the bot+rootkit? I’m assuming the $1500 is not an “all plugins” bundle (for just $200 extra instead of $900)?