By Dancho Danchev
On the majority of occasions, cybercriminals will take basic OPSEC (Operational Security) precautions when using the Internet, in an attempt to make it harder for law enforcement to keep track of their fraudulent activities. Over the years, these techniques have greatly evolved to include hybrid online anonymity solutions offered exclusively to cybercriminals internationally.
In this post, I’ll profile a cybercrime-friendly service that’s been offering hacked PCs to be converted into “anonymization stepping-stones” since 2004.
More details:
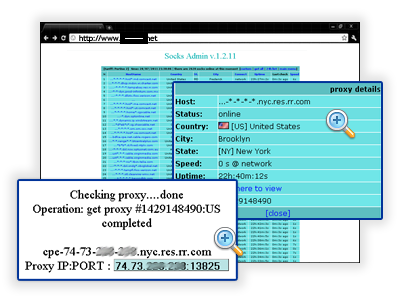
The service offers a self-serving DIY Web interface, allowing potential cybercriminals looking for ways to hide their online activities, to not only gain access to malware-infected hosts internationally, but to “chain” multiple hosts in an attempt to make it even harder to law enforcement to track them down. According to its description, 4000 new “Socks4/5 proxy servers” are added to the service on a daily basis. And in order to make it even easier for cybercriminals to use the service, it features a custom coded Proxy Management Software which greatly assists cybercriminals interacting with the service.
Sample screenshot of the DIY Web interface:
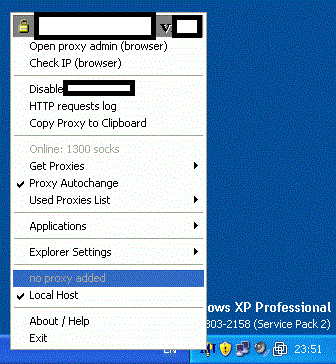
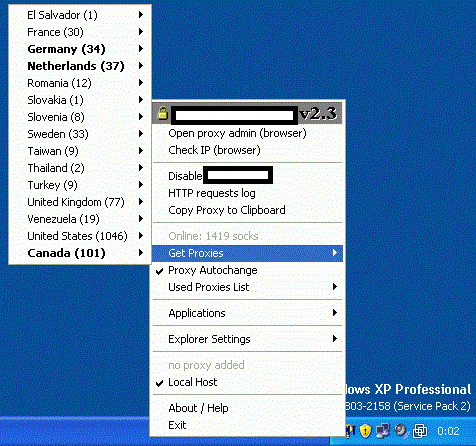
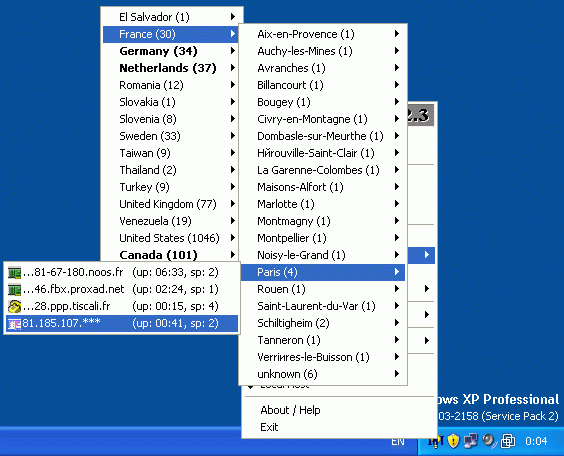
Sample screenshot of the service-branded Proxy Management Software:
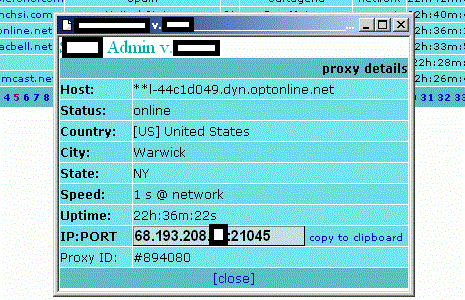
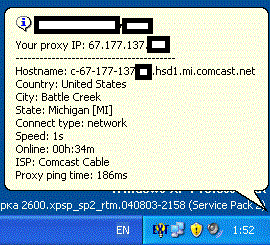
The service allows cybercriminals to easily “autochange” the proxies in use, and automatically rotate them in an attempt to make their activities nearly impossible to trace.
Sample screenshot of a connected Socks 4/5 proxy in action:
Sample statistics of malware-infected hosts internationally, to be used as “anonymization stepping-stones”:
Sample geolocated malware-infected hosts, courtesy of the cybercrime-friendly service:
The prices are as follows:
- 150 proxies per month – $25
- 300 proxies per month – $40
- 600 proxies per month – $50
- 900 proxies per month – $65
- 1500 proxies per month – $95
We’ll continue monitoring the development of this service, and post updates as soon as new developments emerge.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.