Over the last couple of years, the industry’s and the media’s attention has been shifting from mass widespread malware campaigns to targeted attacks most commonly targeting human rights organizations, governments and the military, also known as advanced persistent threats (APTs).
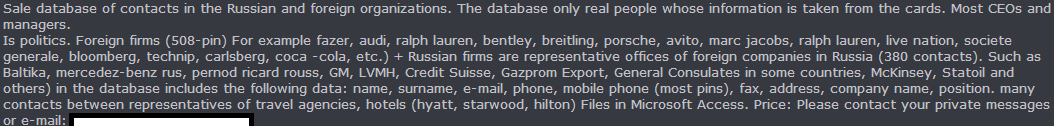
In this post, I’ll profile a recently spotted underground market advertisement, which basically offers a Microsoft Access file of data belonging to executives within major companies such as Audi, Ralph Lauren, Bentley, Breitling, Porsche, Avito, Marc Jacobs, Ralph Lauren, Live Nation, Societe Generale, Bloomberg, Technip, Carlsberg, Coca-Cola, etc., obtained primarily through valid business cards.
More details:
Sample screenshot of the underground market advertisement:
The inventory consists of 508 contacts of foreign companies based in Russia, and 380 contacts belonging to other companies such as Baltika, Mercedez-Benz Russia, Pernod Ricard Rouss, GM, LVMH, Credit Suisse, Gazprom Export.
In terms of Quality Assurance (QA) from the perspective of the potential cybercriminal, there are several types of data sets – the compromised database with valid data, the harvested+fraudulent opt-in type of data, and apparently, the scanned data, in this this case from real business cards.
Taking into consideration the fact that these campaigns spread primarily over email, are very well researched, and that basic marketing principles for increasing click-through rates are taken into consideration, in the past, we’ve discussed several popular methods cybercriminals use in order to automatically obtain valid and versatile sets of personal information, to be later on used in social engineering driven campaigns.
We predict that, now that market segmentation is an every day reality, localization will be the next practice which will cause a widespread effect internationally, due to the fact the actual malicious/fraudulent messages would have been authored by native speakers.
Our advice? Don’t just hand out your business card to anybody, or it may easily end up on the underground marketplace.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.