By Cameron Palan and Nathan Collier
Recently, we discovered a new malicious Android application called Android.MouaBot. This malicious software is a bot contained within another basic app; in this case, a Chinese calculator application. Behind the scenes, it automatically sends an SMS message to an auto-reply number which replies back to the phone with a set of commands/keywords. This message is then parsed and the various plugins within the malicious packages are run or enabled.
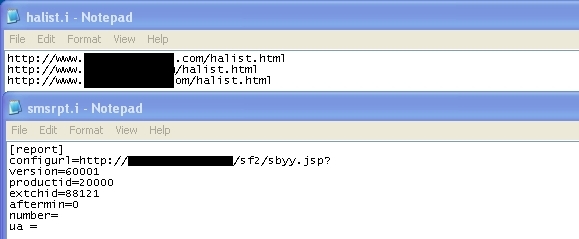
To find out how to contact the auto-reply numbers, there are two files within the app listing a few URLs which, when visited, display a single line referring the app to another IP address. These IPs are then used to send configuration information down to the app.
Once the app has the information it needs, it will text an auto-reply SMS number to receive commands on how or what to execute. When it receives a text, it will first check to see if it is from the auto-reply number, and then check the message for keywords. Regardless of the message’s origin, it will be logged as well.
As this is all occurring, the application suppresses the automatic SMS messages so the user does not see them. The bot’s behavior when receiving SMS can actually be seen in the logs as well:
The various plugins or functions of the bot appear to range from changing APN settings to preventing the phone from being locked. It’s possible other functionality could be added or downloaded by the bot in addition to the main functionality.
Malware like this is just another reason why you should have Webroot SecureAnywhere installed on your mobile device.