On their way to acquire the latest and coolest Android game or application, end users with outdated situational awareness on the latest threats facing them often not only undermine the confidentiality and integrity of their devices, but also, can unknowingly expose critical business data to the cybercriminals who managed to infect their devices.
How are cybercriminals achieving this in times when Google is automatically scanning all submissions to the Google Play store, and is also verifying the applications to prevent the abuse of potential installations from untrusted third-party stores/application download locations?
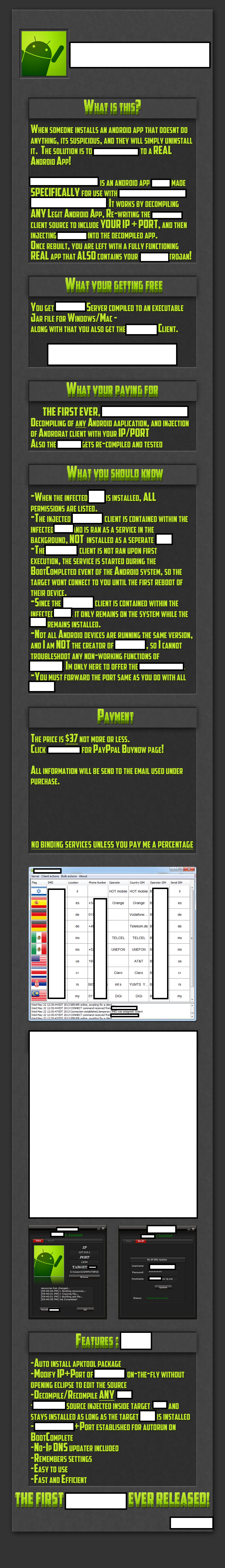
Easier than you to think, especially with the recent commercial availability of a DIY Android application decompiler/injector developed to work exclusively with a publicly obtainable Android-based trojan horse.
More details:
Sample screenshot of the actual advertisement:
What this commercially available tool basically does is automatically inject a pre-configured Android trojan client into (supposedly) any Android application. The trojan will only become active following a reboot of the device, in an attempt by its author not to trigger any kind of suspicion on the infected user’s end. The price for this tool is $37.
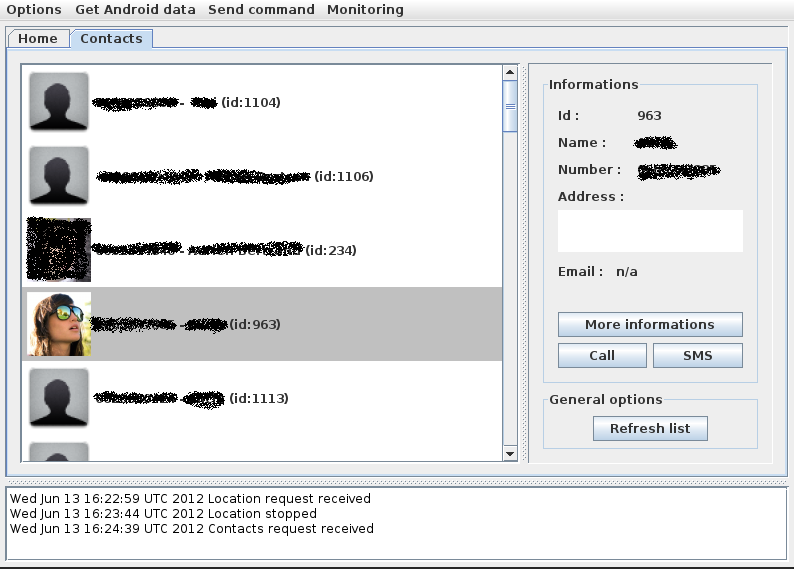
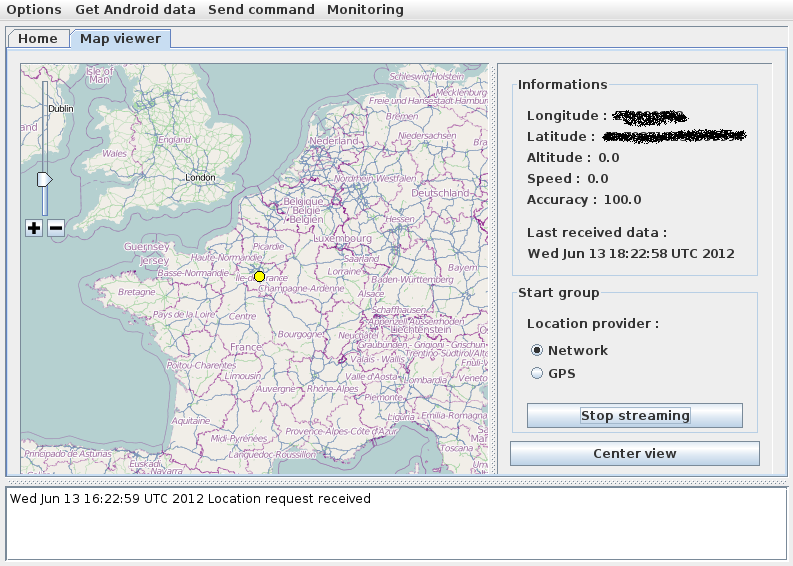
Sample screenshots of the DIY Android Trojan recommended as a default choice to use with this decompiler/injector:
The Android based trojan appears to have been coded by a group of four students for a university project.
The trojan can be activated either through a SMS or a phone call. It has the following features:
- the capacity to steal an affected user’s entire address book including all the relevant contact information
- get the incoming/outgoing calls history
- get all the messages (SMS/MMS)
- network/GPS based location tracking
- real-time monitoring of incoming calls or messages
- the ability to make a phone call/send messages with the user’s his Caller ID
- activate the device’s microphone
- initiate outgoing video streams
- visit any given URL
- forced vibration of the device
However, despite the cheap price and ease of use of these malicious tools, the fact that the ‘phone-back’ location of the server is hard-coded and cannot be rotated/changed on-the-fly in combination with the default choice of no-ip.org (thankfully) lead to a centralized C&C infrastructure, making it fairy easy to monitor/take down one of these Android botnets. What’s so special about no-ip.org, and how does it differentiate itself from the rest of the dynamic DNS providers? It’s the fact that it continues to occupy the top positions of the charts, highlighting the most widely abused dynamic DNS service providers.
What about distribution/infection vectors? There are multiple Android malware distribution scenarios worth emphasizing on, in terms of their eventual use by the cybercriminals who purchase the tool profiled in this post.
For instance, they can buy access to compromised Web servers — or directly compromise them through DIY Google Dorks tools — and instead of monetizing the traffic by serving client-side exploits, they can filter and redirect all the mobile device traffic to a fraudulent/malicious Android application. We’ve already seen and profiled a similar situation, that was affecting a popular Bulgarian Web site for watches, earlier this year. Think that no one would download a low-profile Android application from Google Play, distributed by a largely unknown developer? Think again. Cybercriminals are already looking to buy access to verified Google Play accounts, whose reputation could prove crucial when distributing malware to the users who trust/recommend a particular developer.
Want to know more about the threats targeting your mobile device? Go through the ‘Malicious Mobile Apps’ infographic‘.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.









I’ve been hacked since 2012 and I cannot get anyone to help me!! Who can I contact.
I’m from South Africa
Angela
Angela,
Please reach out to our Customer Support Team at your convenience:
https://www.webroot.com/us/en/support/contact
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Warm Regards,
Josh P.
Social Media Coordinator