In a series of blog posts, we’ve been highlighting the ease, automation, and sophistication of today’s customer-ized managed spam ‘solutions’, setting up the foundations for a successful fraudulent or purely malicious spam campaign, like the ones we intercept and protect against on a daily basis.
From bulletproof spam-friendly SMTP servers, to segmented harvested databases for any given country internationally, managed spamming appliances, to segmented databases of APT-friendly (advanced persistent threat) emails belonging to the U.S government/military, for years, the cybercriminals operating these managed services have been directly contributing to the epidemic dissemination of fraudulent/malicious emails internationally.
We’ve recently spotted a Russian one-stop-shop for spammers offering virtually everything a spammer can ‘vertically integrate’ into, in an attempt to occupy a bigger share of this underground market segment. Let’s take a peek at the service and discuss its unique value proposition (UVP).
More details:
Sample screenshots of the services of the ‘vertically-integrated’ Russian one-stop-spamming-shop:
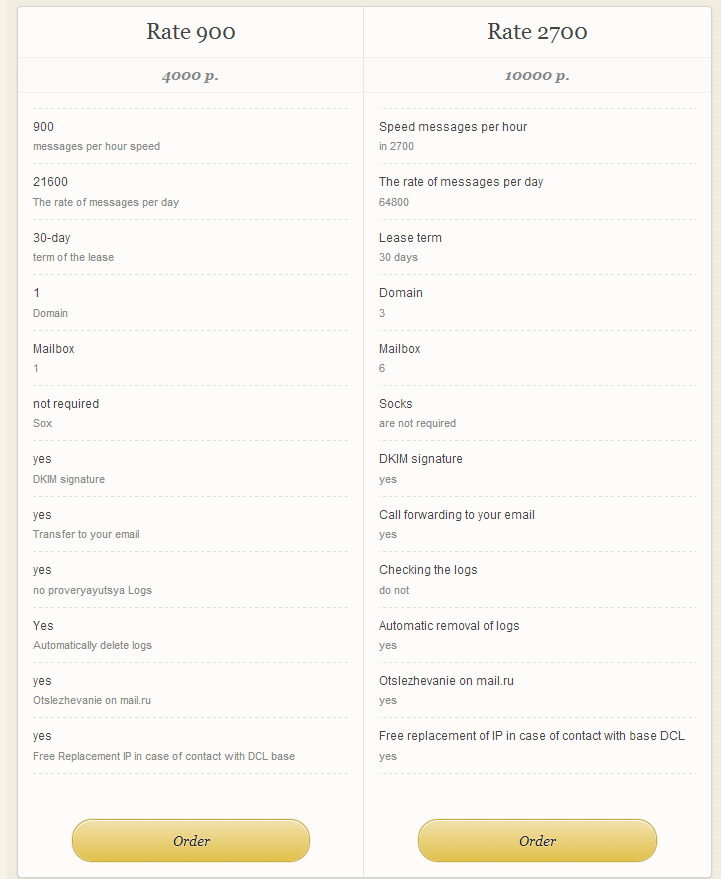
Next to pointing out the exact number of spam message the server is capable of sending on per hour/per day basis, the service explicitly states that Socks4/5 enabled malware-infected hosts are not necessary for it to work, indicating that it’s relying on bulletproof hosting infrastructure. Moreover, the DKIM (DomainKeys Identified Mail) enabled servers will be constantly monitored, and if they ever get RBL-ed (Real-time Blackhole List), a new clean server IP will be offered to the customer free of charge.
Potential spammers are also prohibited from spamming phishing emails, adult content and drugs (prescription only drugs appear to be allowed though).
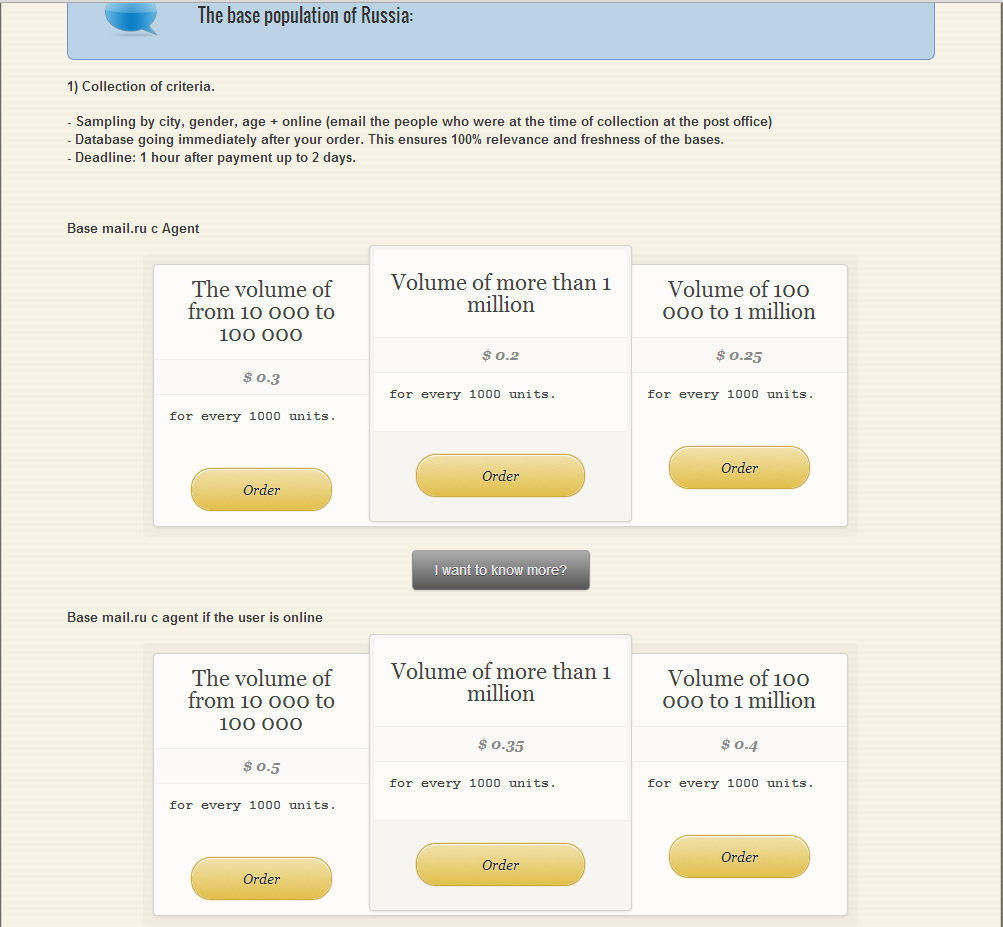
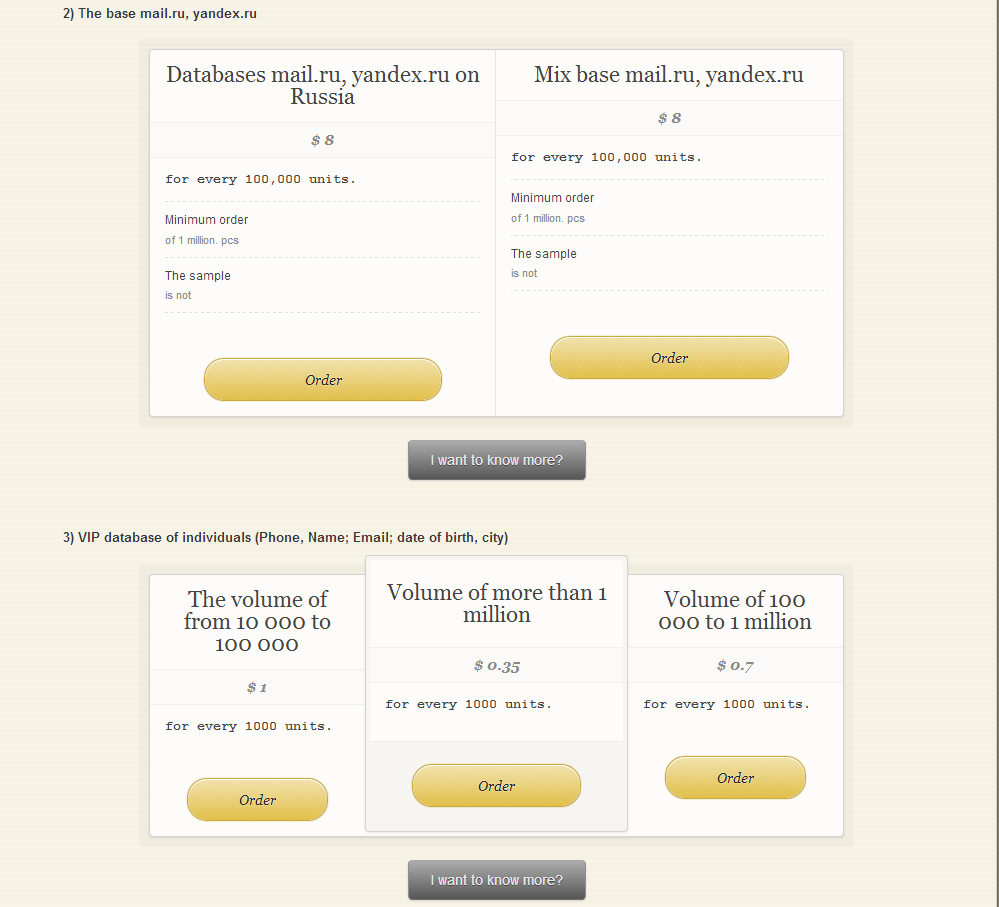
The service is ‘naturally’ offering segmented harvested email databases, in this case, emails belonging to Russian citizens.
Furthermore, the service is also exclusively offering emails belonging to some of Russia’s most popular free email service providers.
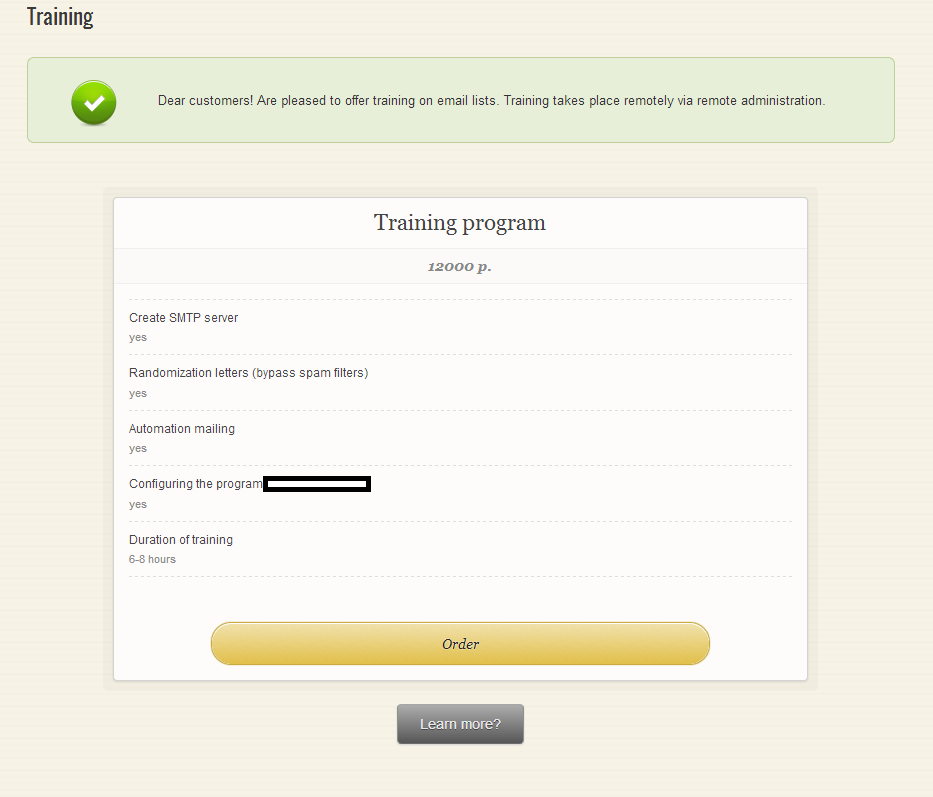
In addition to these segmented databases, the service is also offering practical training lasting between 6 to 8 hours, helping novice spammers understand how to set up their SMTP server, how to bypass spam filters, and how to configure a popular DIY type of spamming application.
In a world dominated by botnets spreading billions of fraudulent/malicious spam emails, certain vendors of managed spam services will do anything to differentiate their unique value proposition (UVP). Including re-introducing a popular spammer’s tactic in 2013, namely bulletproof spam-friendly DKIM-supporting (DomainKeys Identified Mail) SMTP servers. What’s so special about DKIM-enabled SMTP servers, anyway?
Many of our valued blog readers definitely remember a time when DKIM was the future, or at least a logical response by major Internet properties on their way to combat malicious and fraudulent emails impersonating them. However, spammers quickly adapted by exploiting the weakest link in the account registration process — CAPTCHAs — and by doing so, quickly developed a new market segment – Web-based spam sending platforms relying on hundreds of thousands of automatically registered email accounts at some of the most popular free Web based email service providers. These platforms/managed Web-based spam sending services inevitably resulted in an increase in spam coming from legitimate email providers.
The business model utilized by the cybercriminals behind this service relies on the general availability of bulletproof hosting providers that allow — usually through a franchise based model — others to re-brand and re-purpose their offerings in a way that would attract even more customers to these platforms for hosting and disseminating malicious and fraudulent content.
We’ll continue monitoring this ever-green market segment and post updates as soon as we spot another cybercrime-friendly spam service.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.