The perceived decline in the use of blackhat SEO (search engine optimization) tactics for delivering malicious/fraudulent content over the last couple of years, does not necessarily mean that cybercriminals have somehow abandoned the concept of abusing the world’s most popular search engines. The fact is, this tactic remains effective at reaching users who, on the majority of occasions, trust that that the search result links are malware/exploit free. Unfortunately, that’s not the case. Cybercriminals continue introducing new tactics helping fraudulent adversaries to quickly build up and aggregate millions of legitimate visitors, to be later on exposed to online scams or directly converted to malware-infected hosts. This is achieved through cybercrime-friendly underground market traffic exchange networks offering positive ROI (Return on Investment) in the process.
In this post, I’ll take a peek inside a blackhat SEO/cybercrime-friendly doorways management script, discuss its core features, and the ways cybercriminals are currently abusing its ability to populate major search engines with hundreds of millions of search queries relevant bogus Web pages, most commonly hosted on compromised Web servers in an attempt by the cybercriminals behind the campaign to take advantage of the compromised Web site’s high page rank.
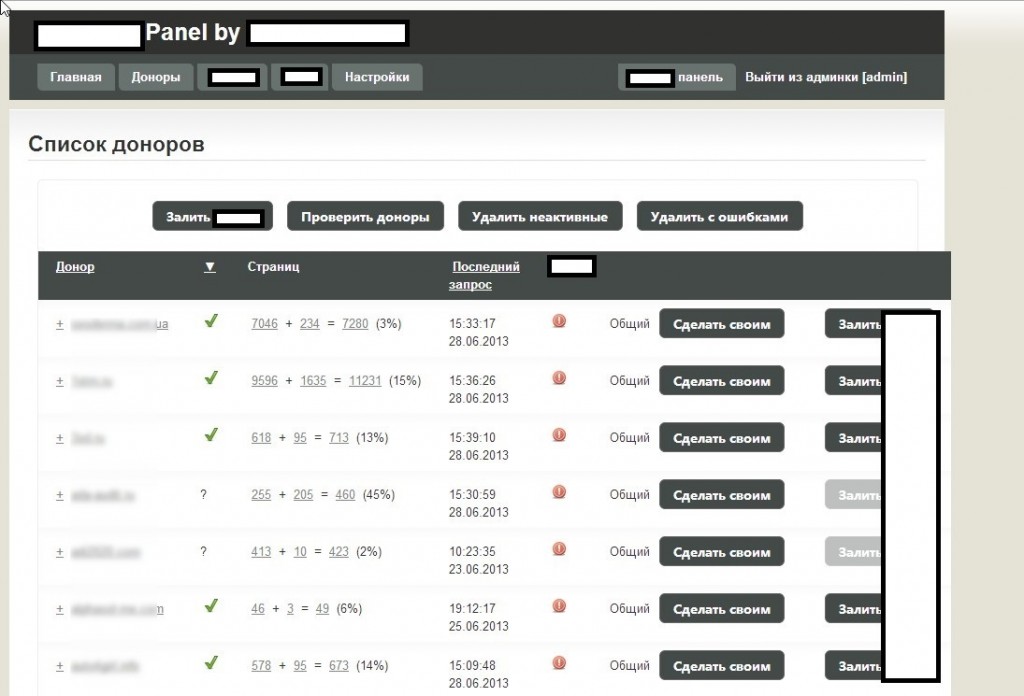
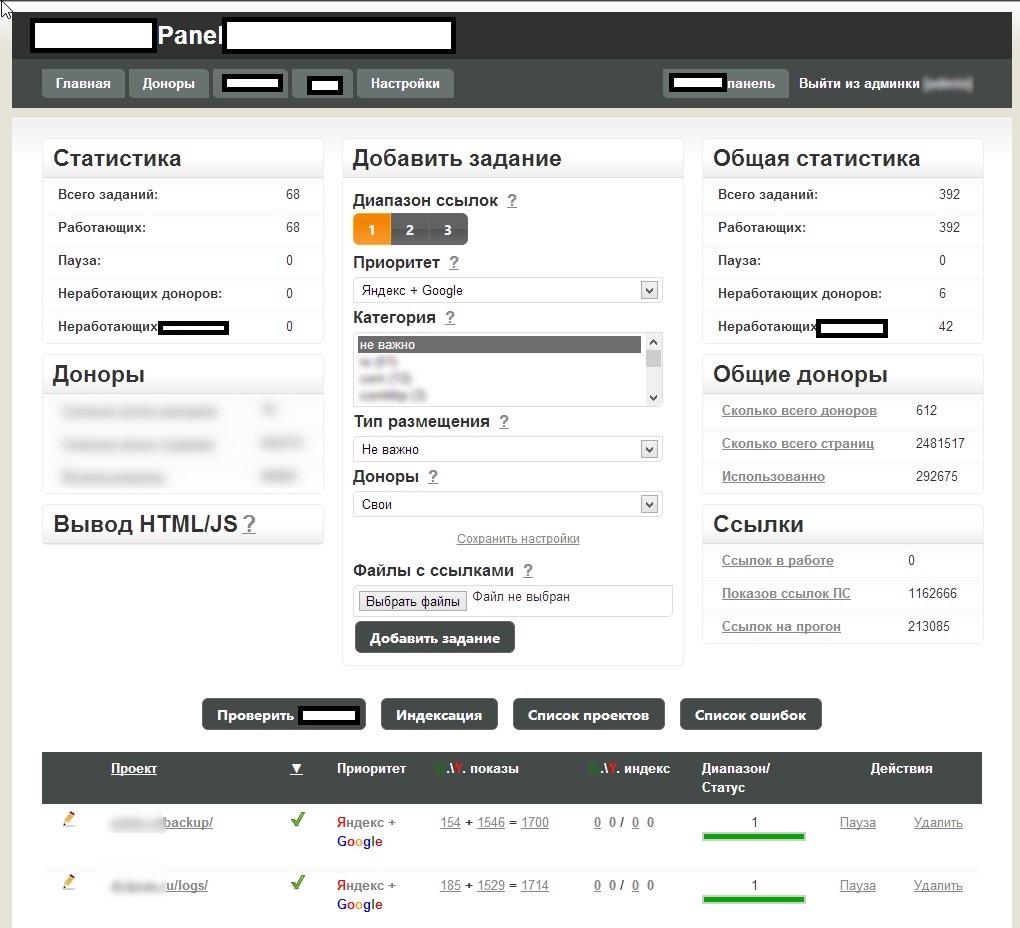
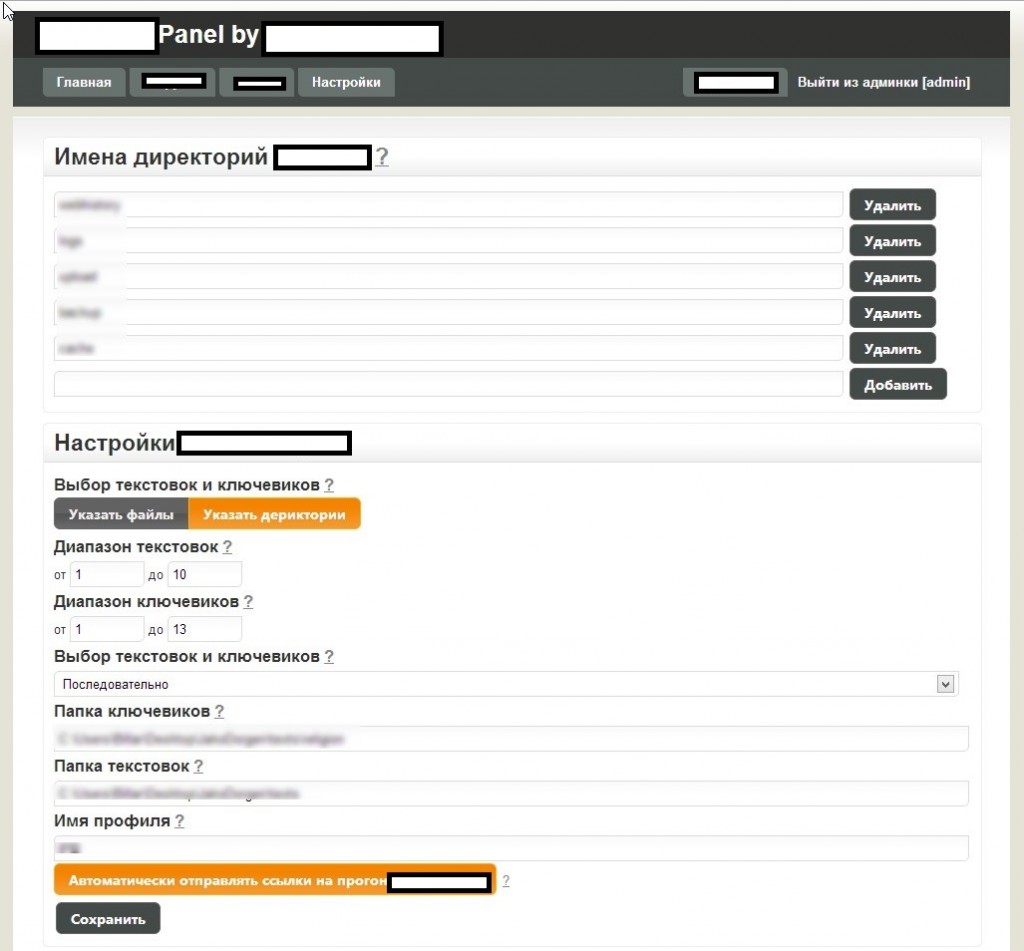
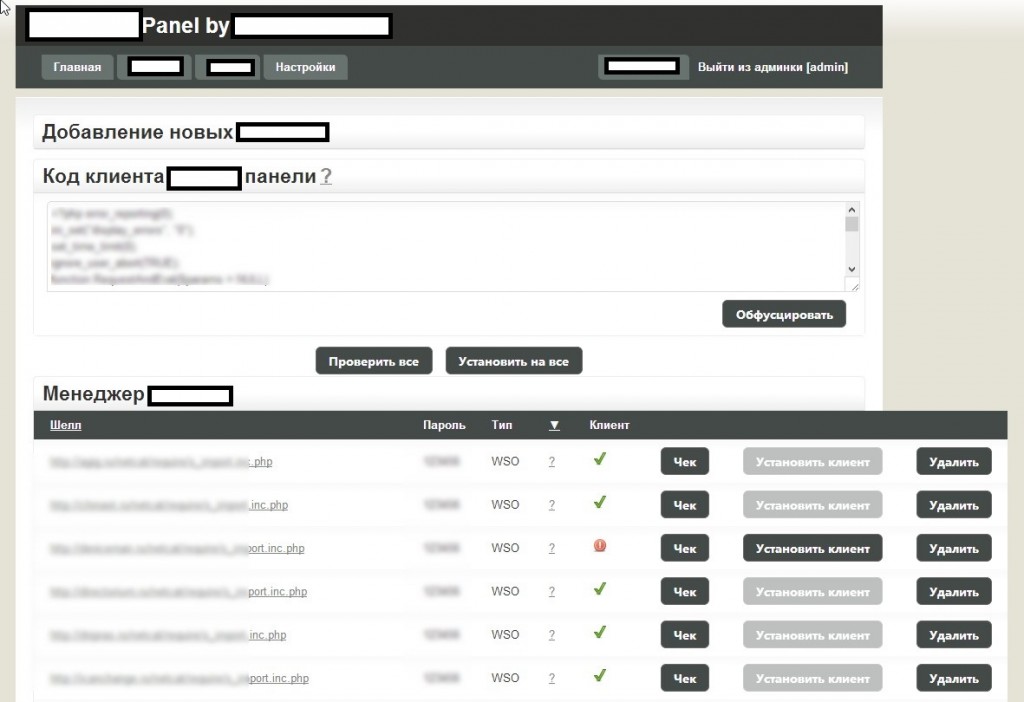
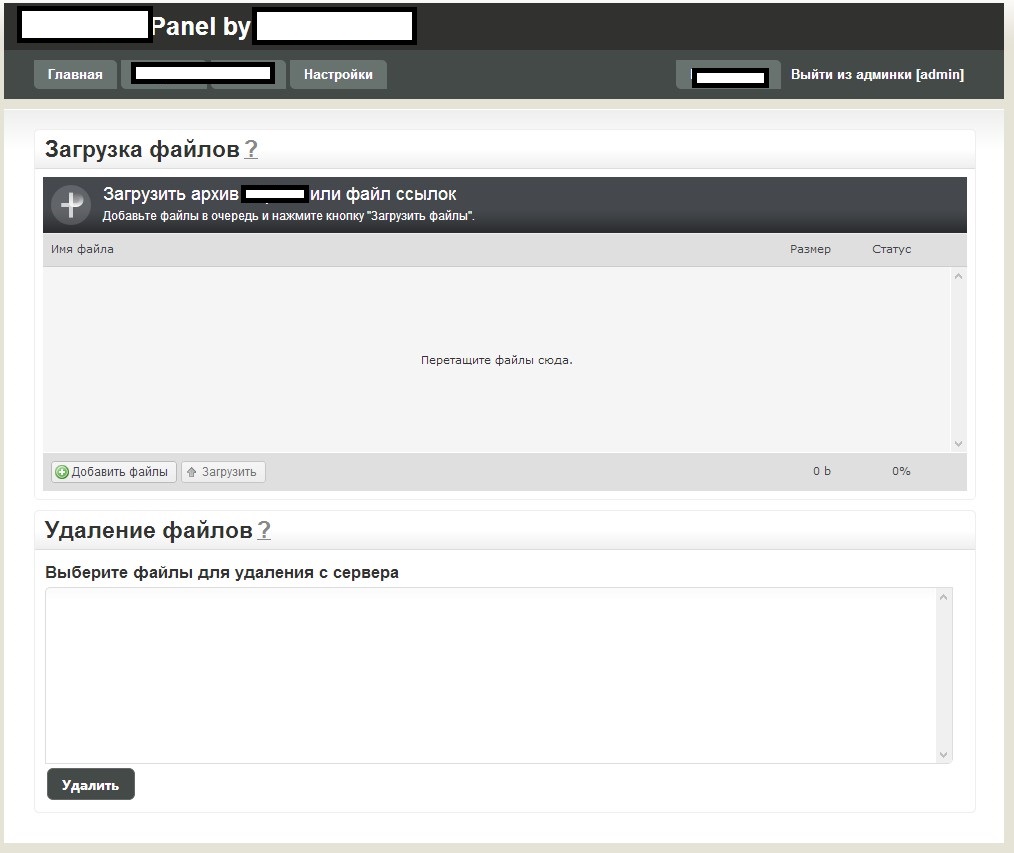
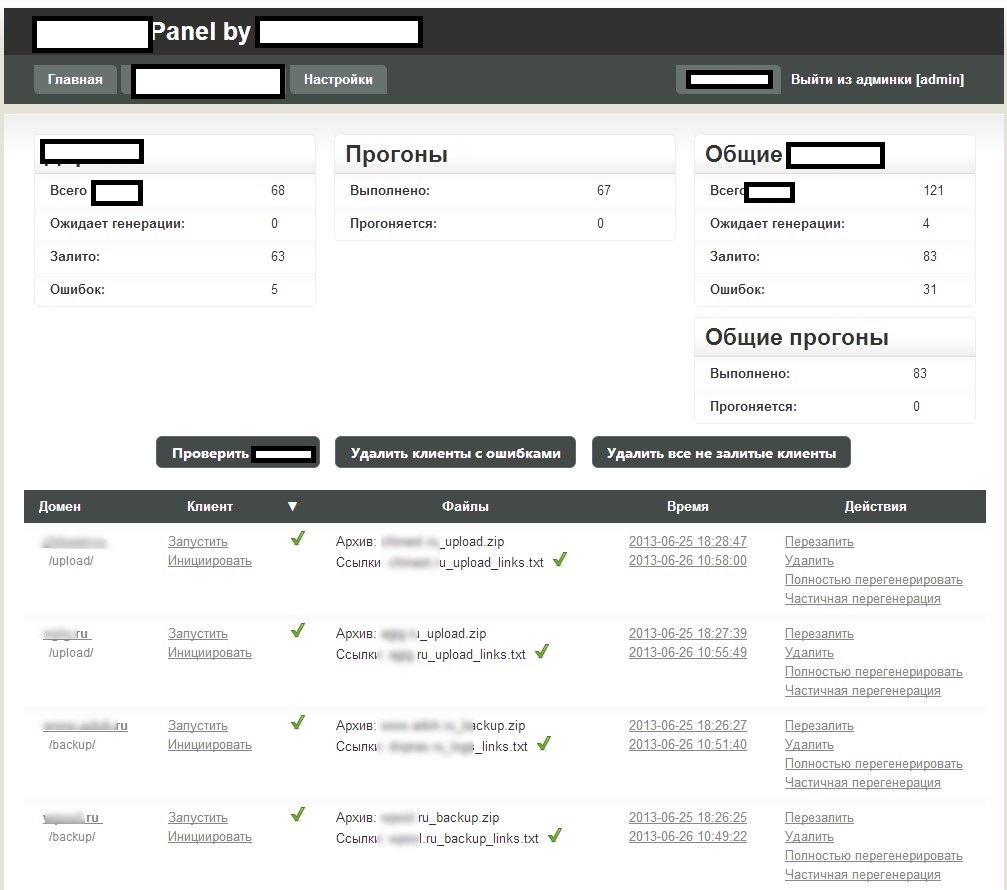
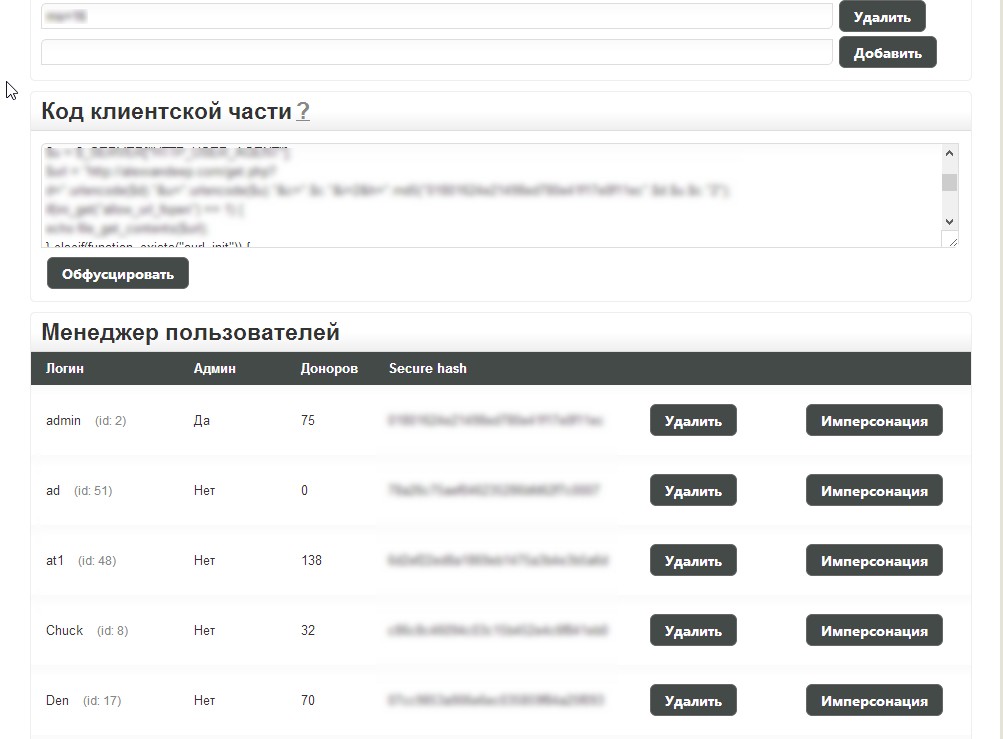
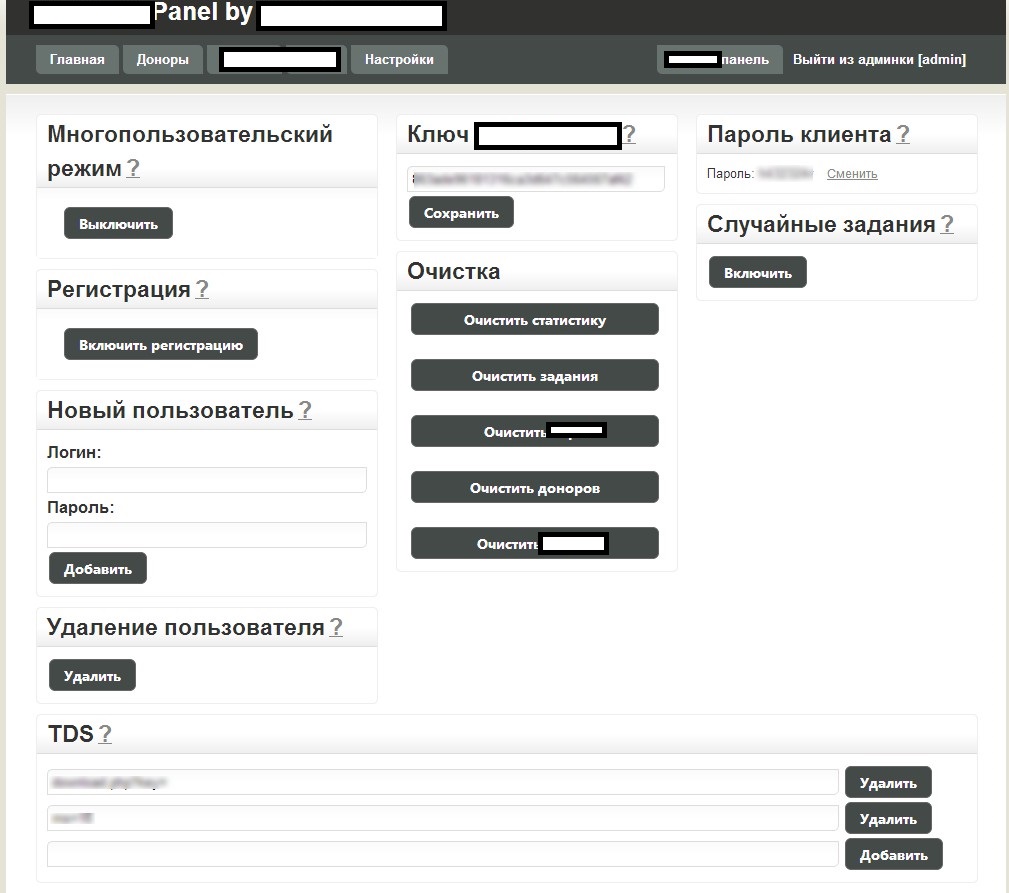
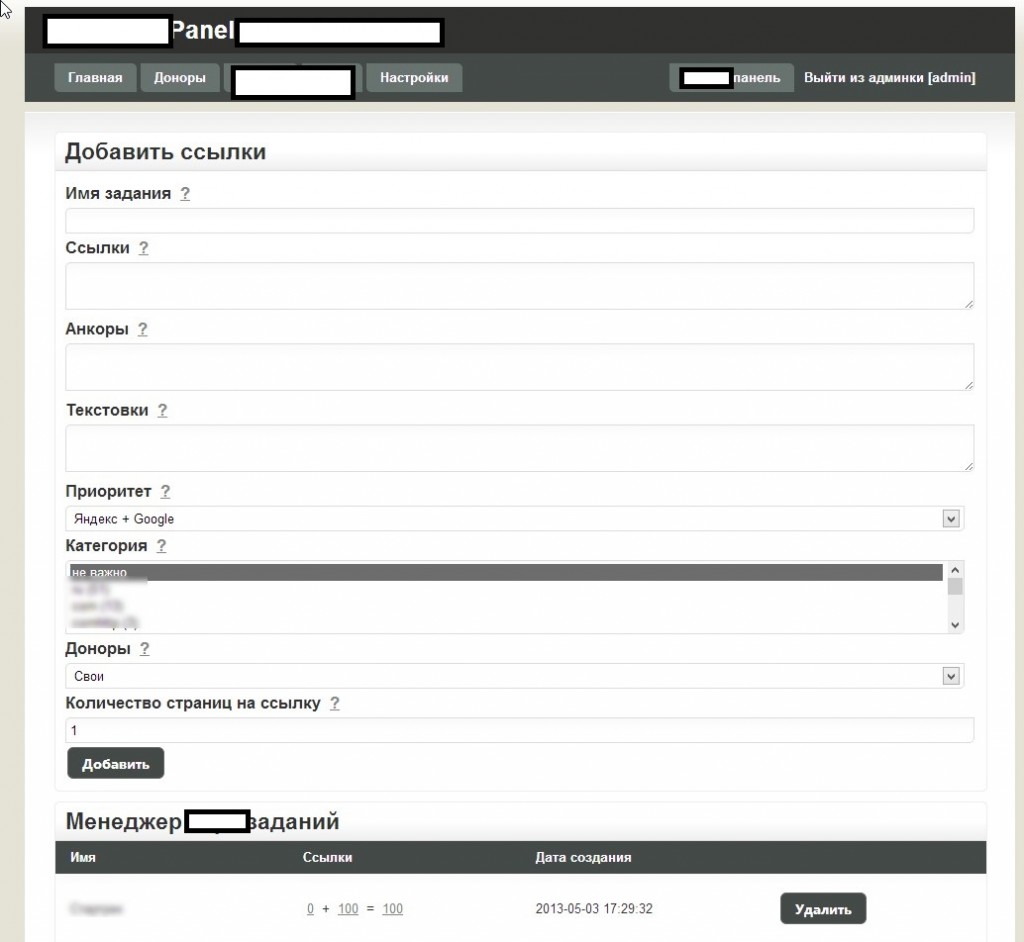
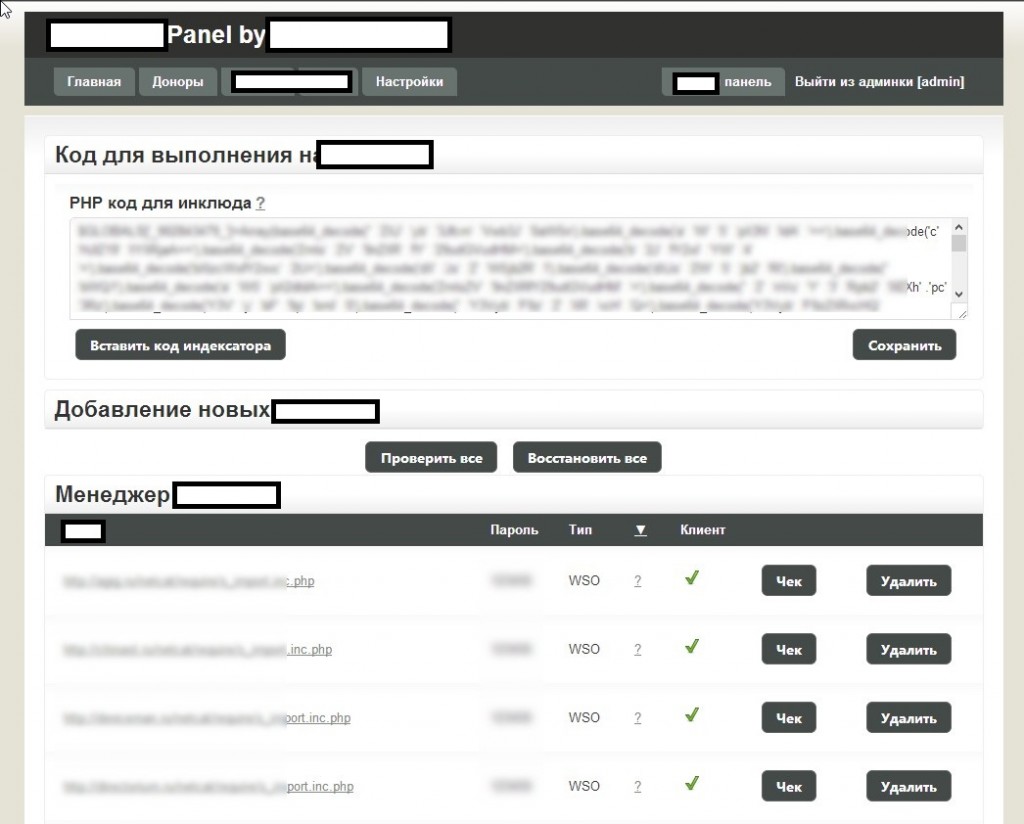
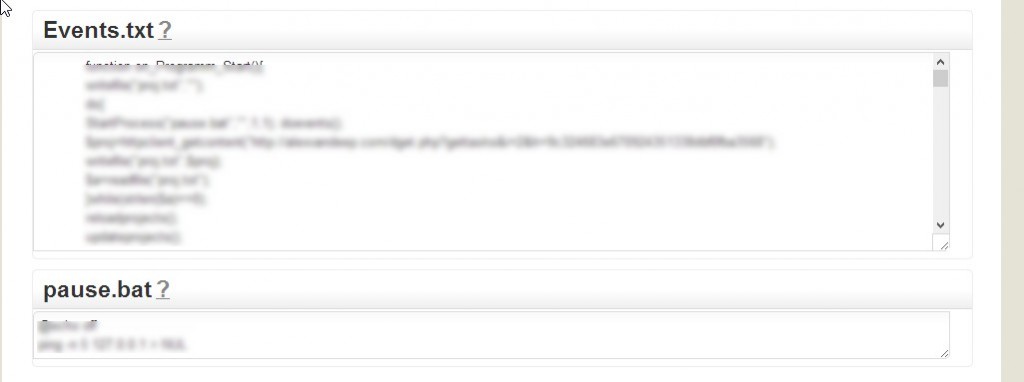
Sample screenshots of the administration panel for the blackhat SEO/cybercrime-friendly multi-user doorways management platform:
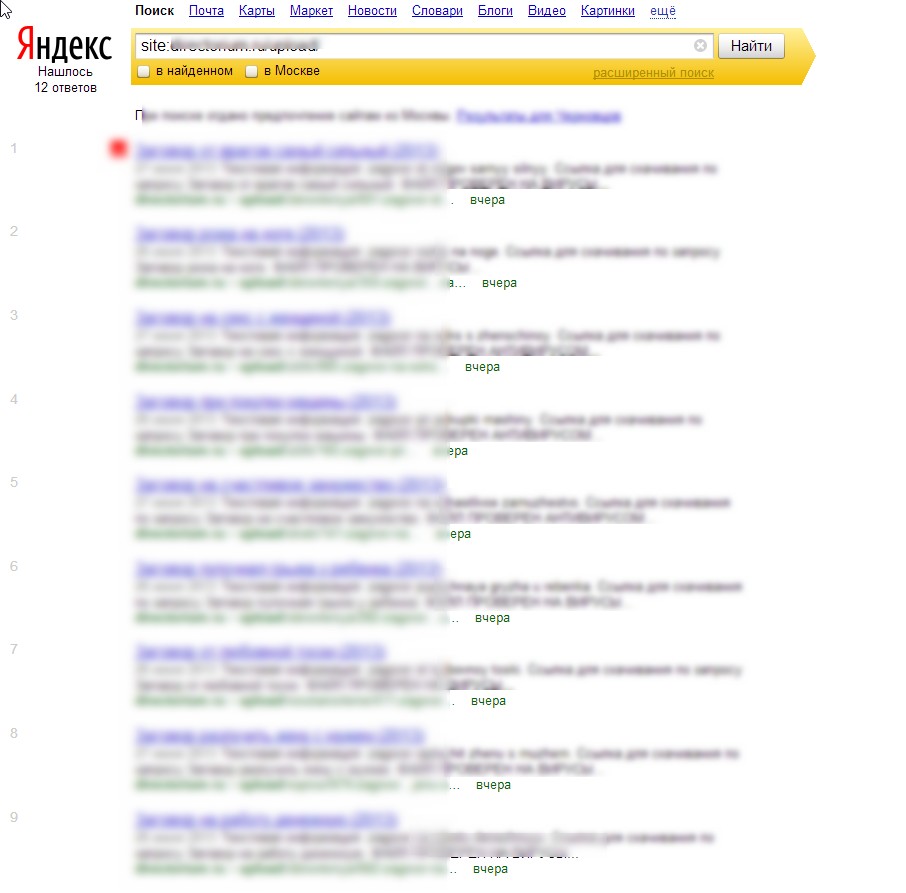
Basically, what this platform enables cybercriminals to do is to have their fraudulent/malicious/rogue content indexed by Yandex and Google in a near real-time fashion — as you can see in the last screenshot, it only took 24 hours to have one of the rogue doorways indexed by Yandex. How is this accomplished? The cybercriminals behind this service have created an ecosystem designed to generate rogue content, and mal-links pointing back to it, with the actual content and links hosted on compromised Web shells, usually hidden on Web servers with high page ranks.
Next to the advanced customization evident throughout the entire administration panel, the tool is also blackhat-SEO-cybercrime-friendly compatible, as it has been designed to be integrated with other tools. Moreover, the multi-user nature of the platform, allows cybercrime/blackhat SEO groups to work simultaneously while maintaining the necessary degree of QA, ensuring the success of their campaigns. And with the market for (compromised) Web shells proliferating, based on the increasing number of supply+demands underground market type of propositions appearing on, both, public/dark Web, it shouldn’t be surprising that cybercriminals would continue possessing access to tens of millions of unique visitors, which they can convert into virtually anything given that the right incentives have been offered through a cybercrime-friendly affiliate network.
We’ll continue highlighting the existence of these platforms, with the idea to emphasize on on just how easy it is to populate the world’s most popular search engines with fraudulent/malicious/rogue content.