Next to the ubiquitous for the cybercrime ecosystem, traffic acquisition tactics such as, blackhat SEO (search engine optimization), malvertising, embedded/injected redirectors/doorways on legitimate Web sites, establishing purely malicious infrastructure, and social engineering driven spam campaigns, cybercriminals are also masters of utilizing social media for the purpose of attracting traffic to their fraudulent/malicious campaigns. From the efficient abuse of Craigslist, the systematic generation of rogue/bogus/fake Instagram, YouTube, and email accounts, the process of automatic account generation continues to take place, driving a cybercriminal’s fraudulent business model, naturally, setting up the foundations for upcoming malicious campaigns that could materialize at any point in time.
In this post, I’ll discuss a commercially available automatic account registration tool that’s successfully targeting Tumblr, emphasize on its core features, and discuss tactics through which its users could abuse access to these automatically registered accounts.
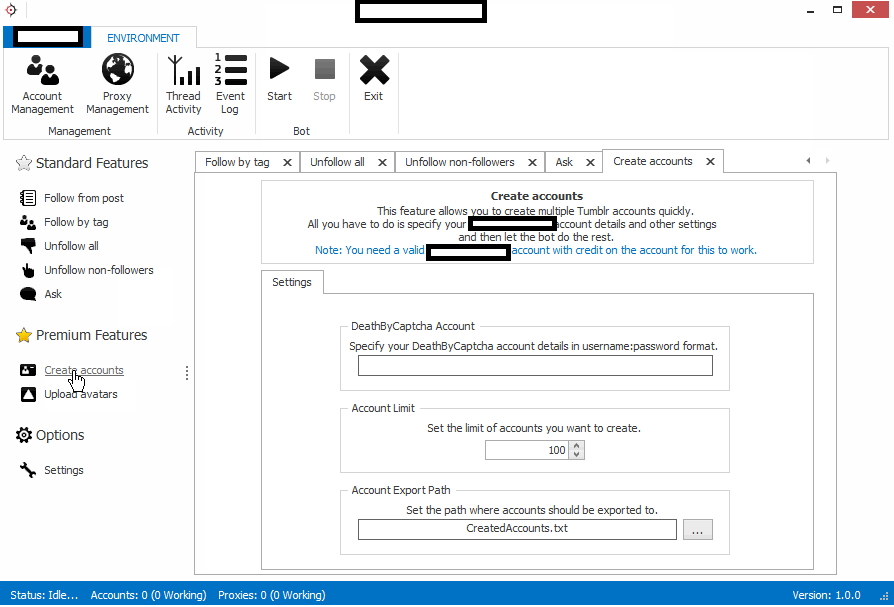
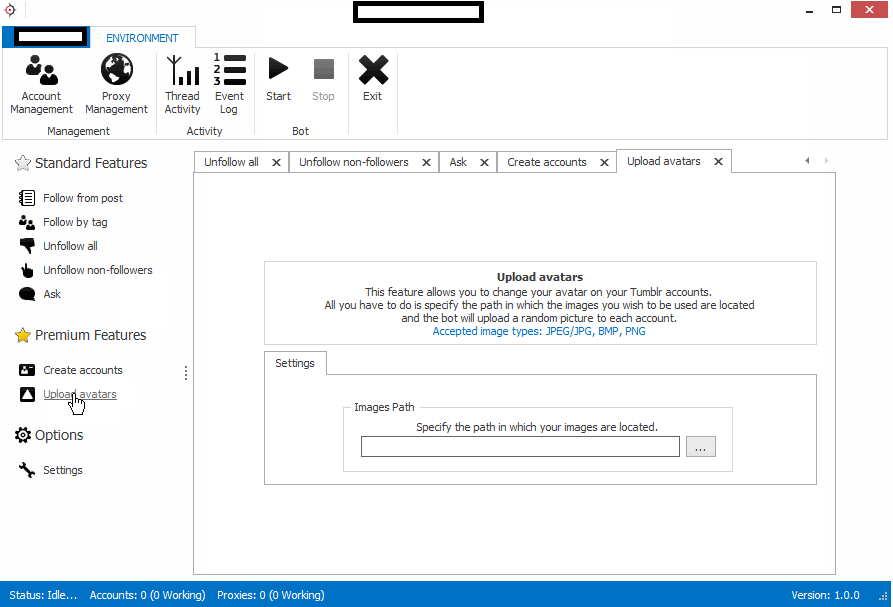
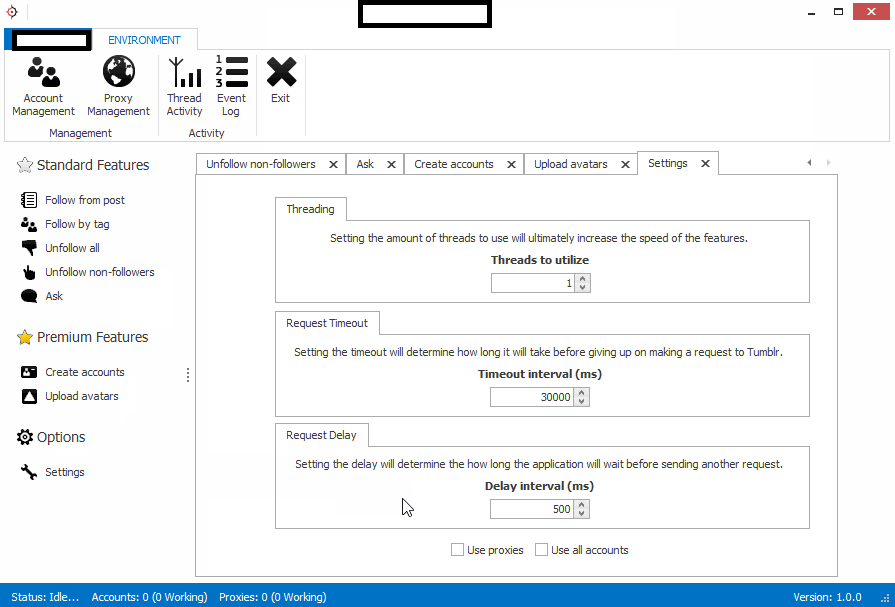
Sample screenshots of the commercial license-based tool in action:
Next to its multi-threaded nature, the tool basically possesses every feature an automatic account registration tool has these days. Features like support for proxies (Socks4/Socks5 enabled malware infected hosts), and built-in API based support for one of the major CAPTCHA-solving as a service type of cybercrime-friendly propositions, are poised to ensure the success of any campaign aiming to abuse Tumblr for automatic account registration purposes. How would cybercriminals potentially abuse this access? They will either start monetizing the inventory of automatically registered accounts to those who’d abuse it in a purely malicious way, or launch a campaign on their own, while monetizing the traffic through an affiliate network. The most recent example of such type of abuse was mentioned in a blog post at the Internet Storm Center (ISC), where the cybercriminals were relying on Tumblr redirects for the purpose of exposing users to malware and Facebook phishing pages. The campaign is just the tip of the iceberg in an extensive ecosystem built by cybercriminals for social engineering purposes.
We’ll continue discussing emerging developments taking place within this market segment for automatic account registration tools and will report as soon as new developments take place.