Cybercriminals continue to maliciously ‘innovate’, further confirming the TTP (tactics, techniques and procedure) observations we made in our Cybercrime Trends – 2013 assessment back in December, 2013, namely, that the diverse cybercrime ecosystem is poised for exponential growth. Standardizing the very basics of fraudulent and malicious operations, throughout the years, cybercriminals have successfully achieved a state of ‘malicious economies of scale, type of economically efficient model, successfully contributing to international widespread financial and intellectual property theft. Thanks to basic cybercrime disruption concepts, such as modular DIY (do-it-yourself) commercial and publicly obtainable malware/botnet generating tools. In 2014, both sophisticated and novice cybercriminals have everything they need to reach an efficient state of fraudulent/malicious operation.
We’ve recently spotted a commercially obtainable modular, Tor C&C enabled, Bitcoin mining malware/botnet generating tool. Let’s discuss its features, key differentiation factors and take a peek inside it’s Web-based command and control interface.
More details:
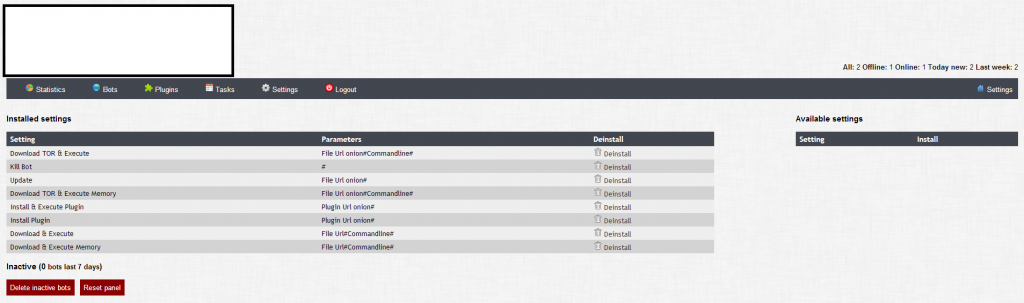
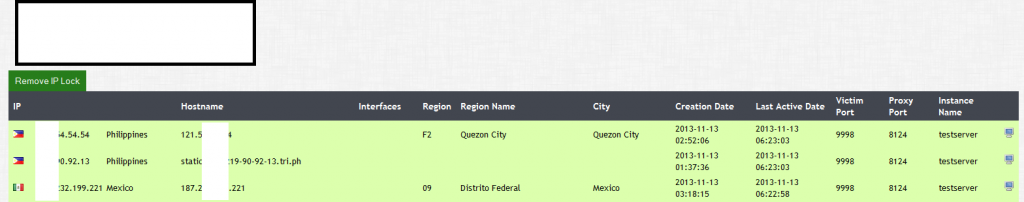
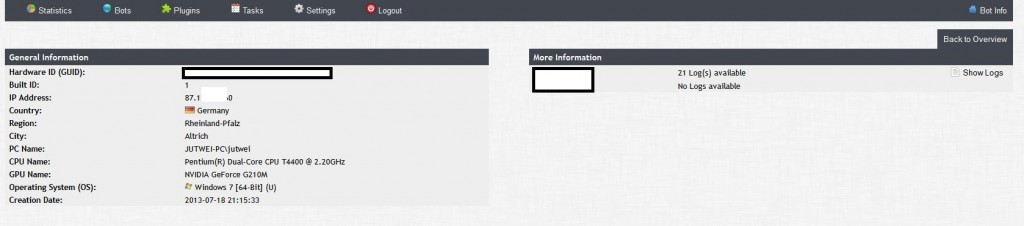
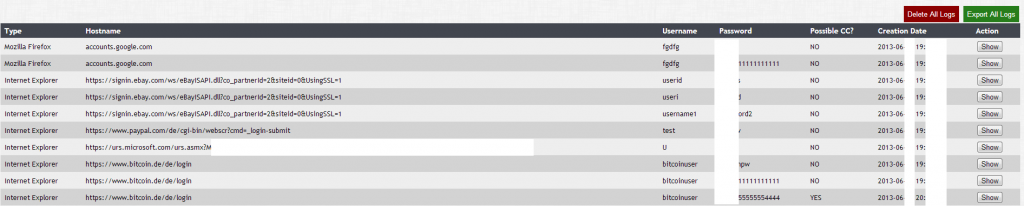
Sample screenshots of the modular, Tor C&C enabled, Bitcoin mining malware/botnet generating tool’s Web based interface:
Priced at $250, and coded in C, the malware/botnet generating tool supports all Windows versions (XP up to 8.1 on x86/x64 hosts), and possesses the cybercrime ecosystem’s standard anti-debugging features. It also encrypts the plugins (modules), with AES-128-CBC. As a related key differentiation feature, it also applies a decent degree of OPSEC (Operational Security) to the bot’s Web-based command and control interface. A few examples are brute-force protection for the admin’s panel and SQL injection protection for the Web based interface. The OPSEC features introduced by the vendor are an indication for decent situational awareness on behalf of the vendor in terms of the industry’s response to large scale botnet infrastructures over the years.
Not surprisingly, the vendor is also Tor-aware in the context of what we believe is a perceived value-added feature in terms of OPSEC. Compared to alternative competing malware/botnet generating tools/platforms within the cybercrime ecosystem, this bot’s command and control domain structure is generated using a Domain Generation Algorithm (DGA) within the Tor network. While Tor can provide additional protection for domain hosting, it also has flaws. Case in point, the Sefnit botnet, which despite its reliance on Tor for C&C communications which gave it a boost in terms of OPSEC/growing infected population, ironically, also introduced a potentially exploitable third-party software, a vulnerable Tor client in this case.
Featured modules/plugins:
– DDoS bot functionality
– Form grabbing features — tested against major Web properties
– Socks5 module
– Passwords stealing module
– (Experimental) task-capable Bitcoin/Litecoin mining feature
Despite its experimental state, the bot’s vendor is also emphasizing on the fact that the prospective cybercriminal can also take advantage of any of the commercially/publicly obtainable stealth Bitcoin mining tools, like the ones we’ve been extensively profiling in a series of blog posts.
We’ll continue monitoring this bot’s development and will post updates as soon as new developments take place.