Recently in the news the FBI filed a status report updating on the court-authorized measures to neutralize GameOver Zeus and Cryptolocker. While the report states that “all or nearly all” of the active computers infected with GameOver Zeus have been liberated from the criminals’ control, they also stated that Cryptolocker is “effectively non-functional and unable to encrypt newly infected computers.” Their reasoning for this is that Cryptolocker has been neutralized by the disruption and cannot communicate with the command and control servers to receive instructions or send RSA keys after encryption. Read more here
While seizing the majority of the GameOver Zeus Botnets from the suspected “mastermind” Evgeniy Bogachev was a big impact to the number of computers infected with GameOver Zeus – about a 31 percent decrease, it’s a very bold claim to state that Cryptolocker has been “neutralized”. The reason why this claim should be scrutinized is because it is only the samples dropped on victims computers that communicated to those specific servers seized that are no longer a threat. All samples currently being deployed by different botnets that communicate to different command and control servers are unaffected by this siege – the majority of encrypting ransomware. Although Evgeniy Bogachev and his group had control of a major chunk of zeus botnets and command and control servers that deployed cryptolocker, it was certainly not all or even the majority of zeus botnets in existence. Most malware authors spread their samples through botnets that they either accumulated themselves (Evgeniy), or just rent time on a botnet from someone like Evgeniy (most common). So now that Evgeniy’s servers are seized, malware authors are just going to rent from some of the many other botnets out there that are still for lease.
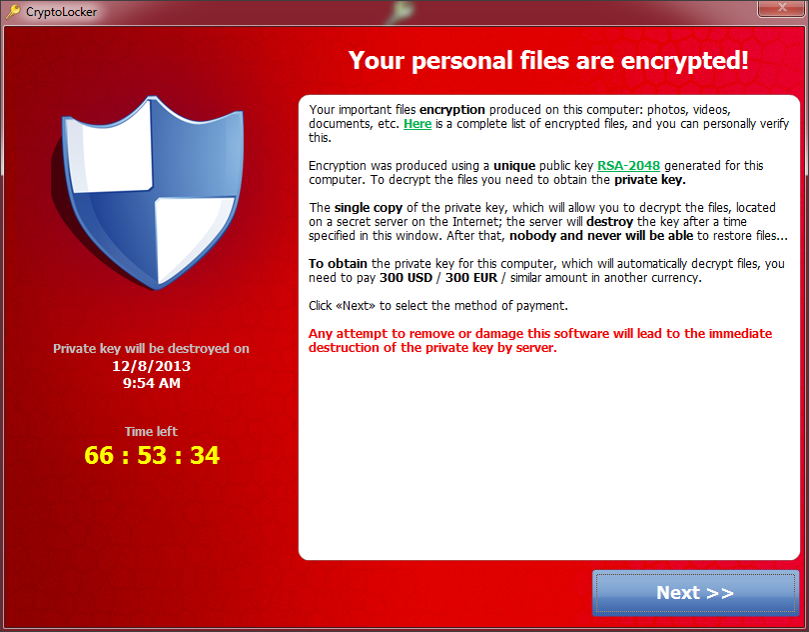
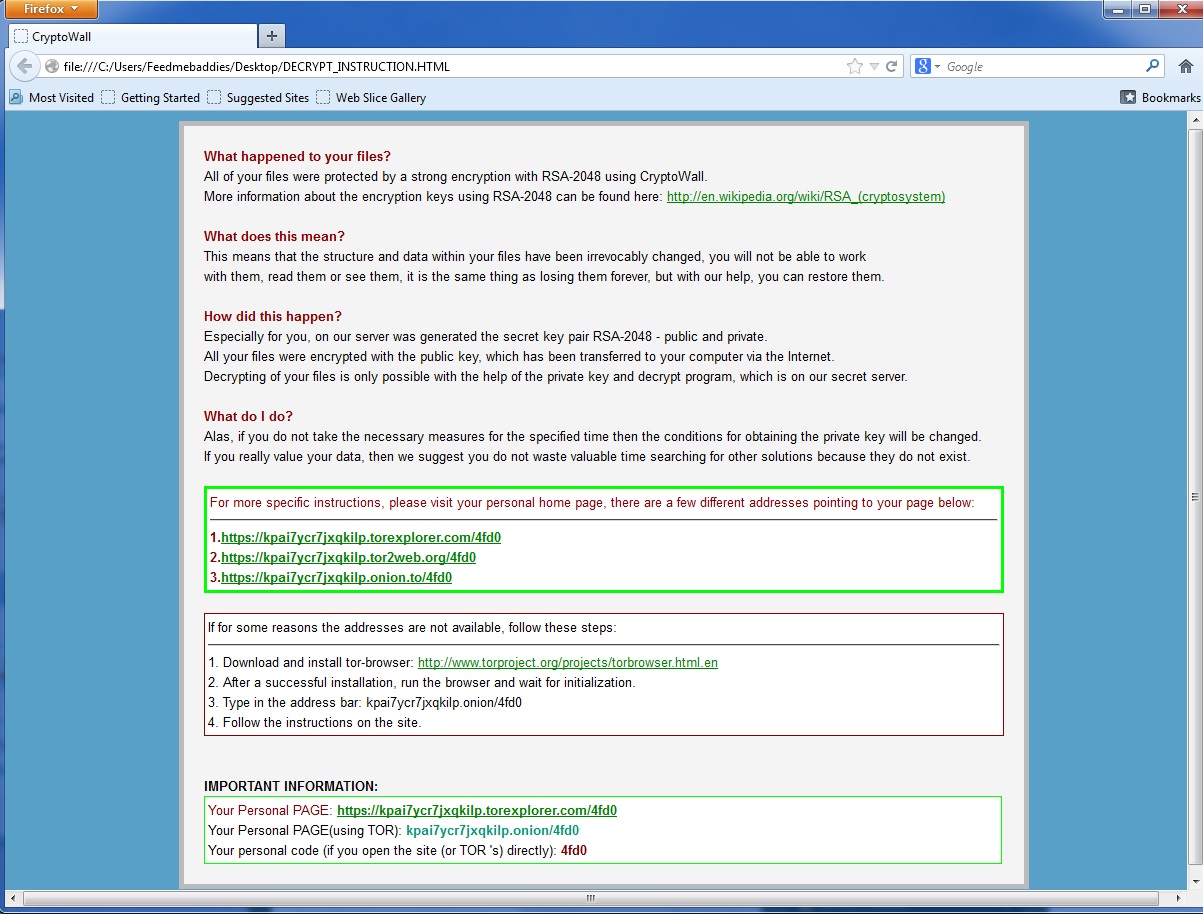
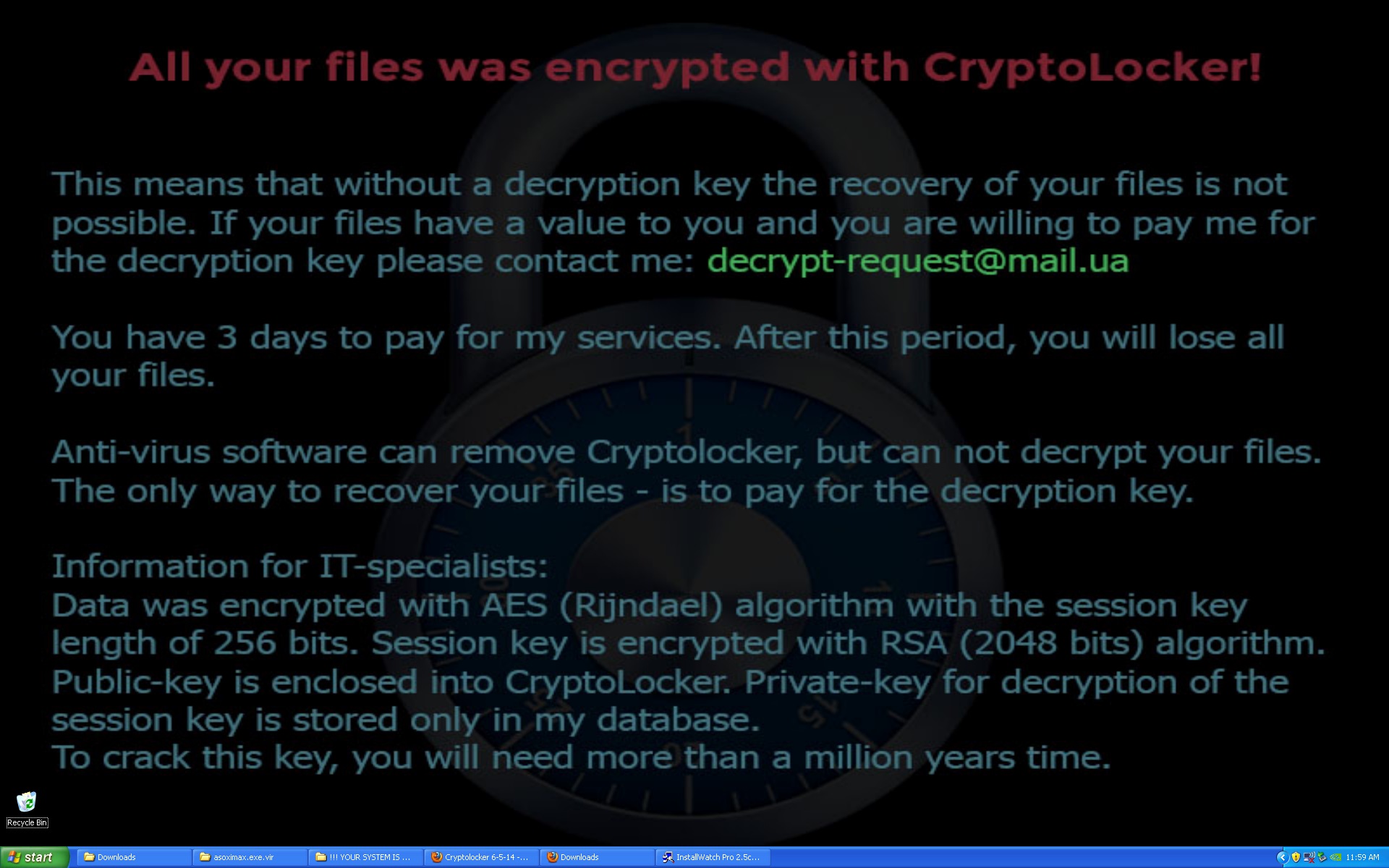
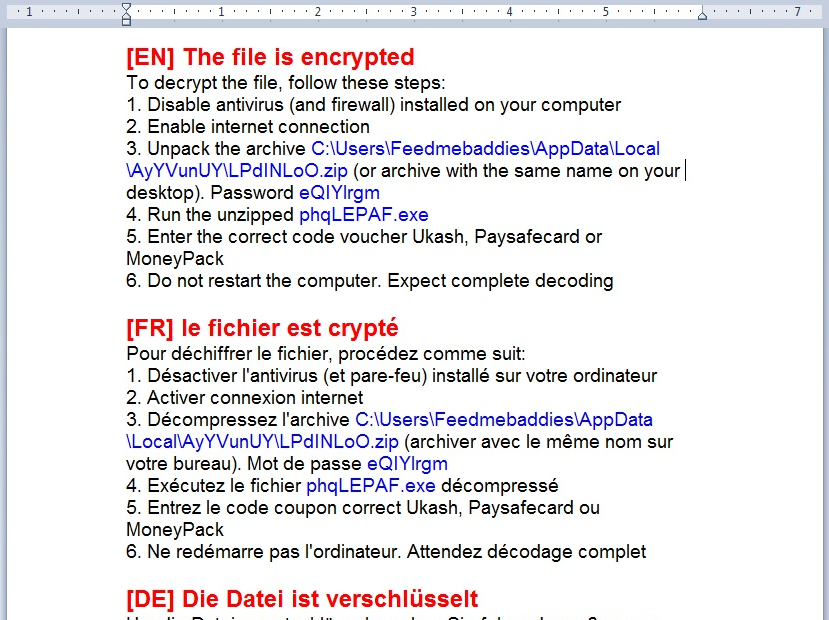
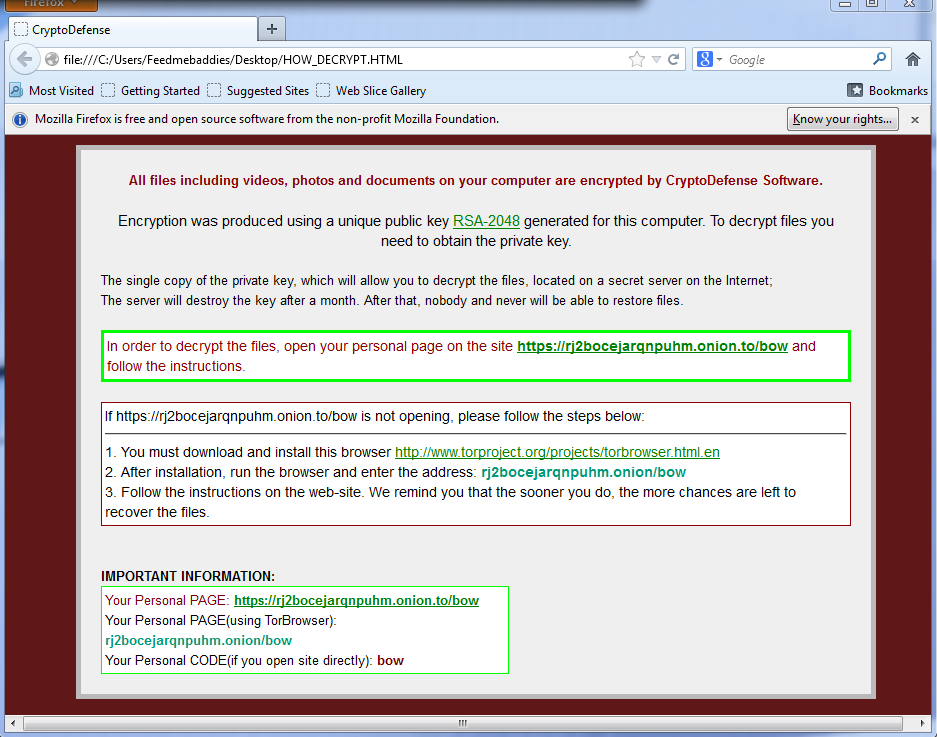
Here are some pictures of samples that we’ve encountered that are still hard at work at infecting users.
All of these work in almost exactly the same way as the infamous traditional cryptolocker we’ve all seen, but they have some improvements. First is that there is no GUI and instead just background changes and texts instructions in every directory that was encrypted. Second is that you no longer pay using a moneypak key in the GUI, but instead you have to install tor or another layered encryption browser to pay them securely and directly. This allows malware authors to skip money mules and increase the percent of profits. The best way to stay protected by attacks like this is to utilize backups to either the cloud or offline external storage. Webroot has backup features built into our product that allow you to have directories constantly synced to the cloud. If you were to get infected by a zero day variant of encrypting ransomware you can just restore your files back as we save a snapshot history for each of your files up to ten previous copies.
So while this is a great win on behalf of the FBI, it’s very bold to claim that cryptolocker is now dead. A better way to put it would be that Evgeniy M. Bogachev’s brand of cryptolocker and anyone who purchased time on his botnet is now useless.








Would be nice if at any time webroot could detect a file being encrypted in real time and prompt the user for permission to continue in effect blocking the malware from delivering its payload. I had a user infected with this on June 3rd. She looked at the warning but she believed her antivirus would protect and didnt feel it was worth letting the IT Dept know! It went out onto our network and started encrypting files on the servers. Thankfully, because I was unable to rely on any sort of anti virus to stop this, I have good backup policies. All files were restored, the infected computer taken off the network, formatted and reinstalled, and life is back to normal!!!