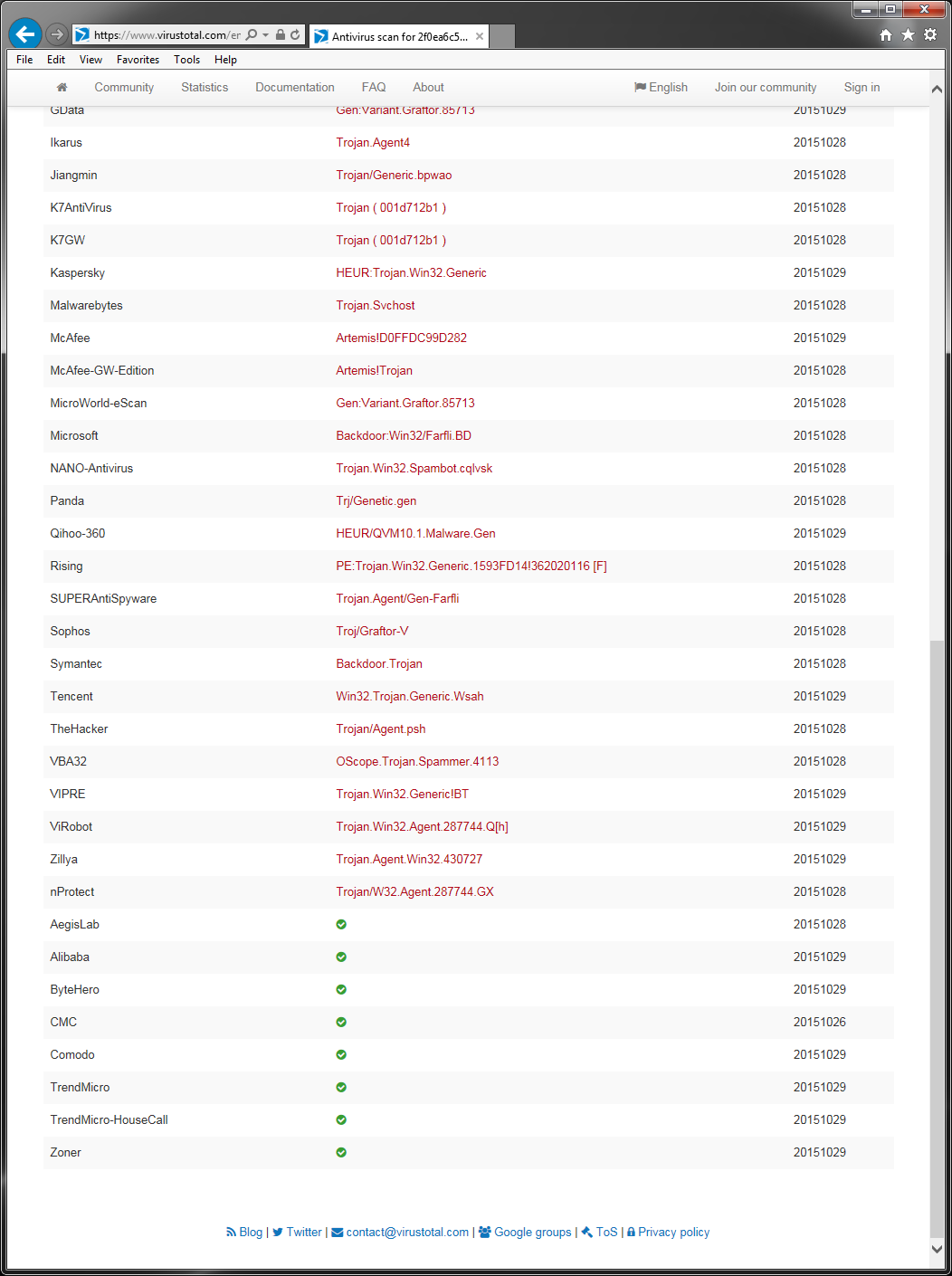
Any time a malware variant hits the news we get numerous requests for information. It is typically quite difficult to provide any information based on names that have been given to threats. A simple way to illustrate this is by using a service such as Virustotal and seeing what name other AV companies use for the same threat. I found a recent article about a new threat that contained a link to a write-up by an AV company including MD5 hashes for the file samples used for the write-up. Below are screen shots of the Virustotal results for one of those files.
The first thing I noticed was that there are numerous names that this is detected as, and they are rather inconsistent. Many of the names used are generic, and there are quite a few heuristic detections included in the results. Another thing I noticed was that the name of the malware from the article and the write-up for this file is nowhere to be found. The AV company whose write-up I got the sample from does detect the file, just not by the name that was in the write-up.
What this shows is that, even though this malware sample was found with a specific name, it is widely detected by generic and heuristic detections. The name that it is detected as becomes rather irrelevant. Identifying new malware and taking it apart to determine how it works and what it does is certainly important, but at the end of the day, simply detecting a file as malicious and removing it is what really matters.