CrytpoMix has been gaining some traction over the past few months, so it’s a good idea that we provide a rundown of this variant in the ransomware family.
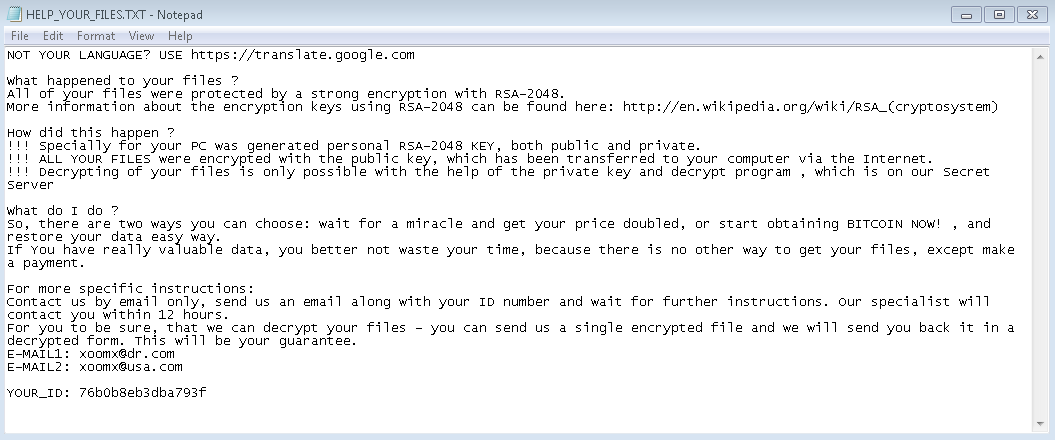
This is ‘barebones ransomware’, so victims aren’t presented with a GUI or a desktop background change. All that is presented is a text file and webpage showing the same text.
This is one of the FEW ransomware variant that doesn’t have some payment portal in the darknet. There is no need to download any tor browser, as they don’t provide any onion links.
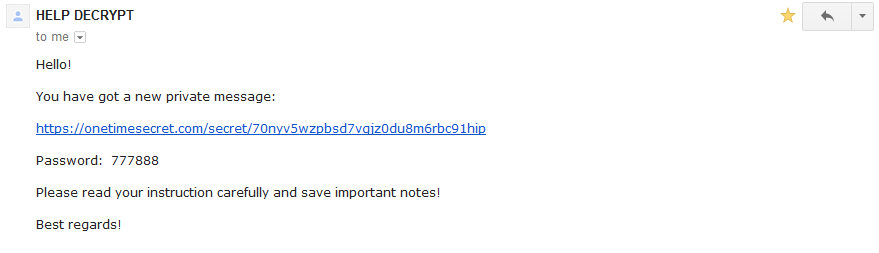
With this variant, victims literally have to email and wait around 12 hours for a response and those responses are encrypted and password protected (to protect the bitcoin wallet address the cybercriminals want payment to be made to).
Example response:
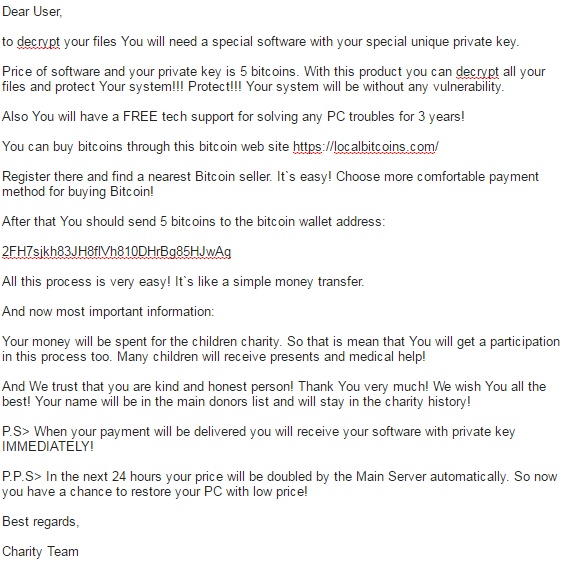
While CryptoMix isn’t fancy, it’s price sure is. 5 BTC (Bitcoin) is an insane amount of money (>$3000), and it wasn’t a few months ago that ransom increases to $700 were all the rage. Also, these criminals even claim that you’ll receive free tech support and all your ransom money goes to a child charity. Please do not be fooled.
Registry Entries added
» HKLM\Software\Microsoft\Cryptography\Defaults\Provider\Microsoft Enhanced RSA and AES Cryptographic Provider
» HKLM\Software\Microsoft\Cryptography\DESHashSessionKeyBackward
» HKCU\Software\Microsoft\Windows\CurrentVersion\Run\Adobe Reader UpdateSoftWare
» HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce\*Adobe Reader Update32
» HKCU\Software\Microsoft\Windows\CurrentVersion\Run\AdobeFlashPlayerSoftWare
» HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce\*AdobeFlashPlayers32
» HKCU\Software\Adobe Reader LicensionSoftWare\AdobeFirstVersionSoftWare
» HKCU\Software\Adobe Reader LicensionSoftWare\AdobeLicensionSoftWare
MD5 hashes analyzed :
b778bda5b97228c6e362c9c4ae004a19
a0fed8de59e6f6ce77da7788faef5489
Webroot will catch this specific ransomware in real time before any encryption takes place. We’re always on the lookout for more types of threats, but just in case of new zero-day variants, remember that with encrypting ransomware, the best protection is going to be a good backup solution. This can be either through the cloud or offline external storage. Keeping it up to date is key so as not to lose productivity. Webroot has backup features built into our consumer product that allow you to have directories constantly synced to the cloud. If you were to get infected by a zero-day variant of encrypting ransomware, you can just restore your files back as we save a snapshot history for each of your files (up to ten previous copies). Please see our community post on best practices for securing your environment against encrypting ransomware.







DO NOT PAY FOR THIS!!!
we were infected and they asked for 10 bitcoins, after some negotiations the price was lowered to 6 bitcoins. they provided 1 decrypted file to prove concept. we paid 6 bitcoins and they asked for another .6 as the c&c server will not provide the key due to late payment. after promptly paying another .6 bitcoins (about $4800 in total) there has been no communication from them! its been 2 weeks and nothing.
WHATEVER YOU DO, DO NOT TRUST THEM, THEY WILL NOT DECRYPT YOUR FILES!!!!