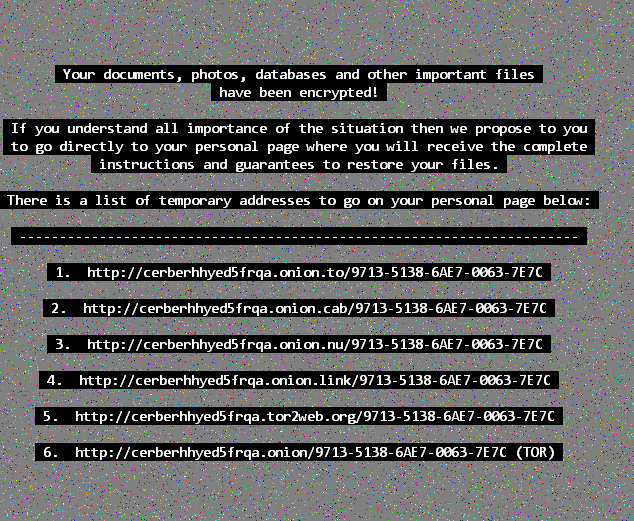
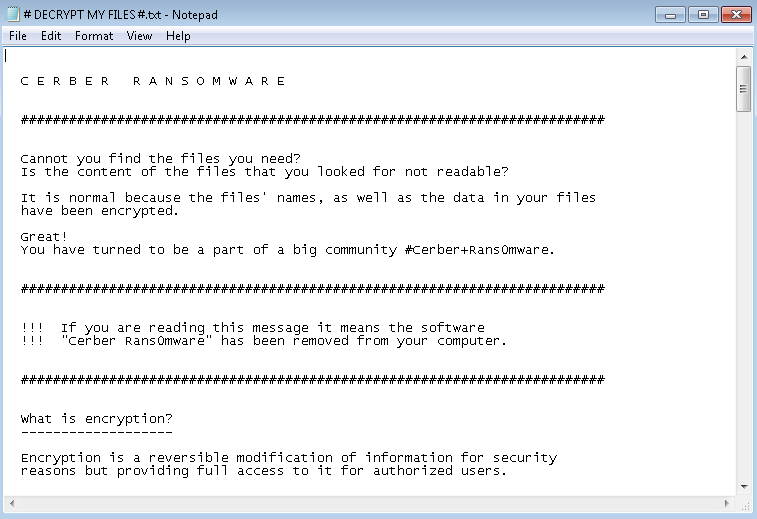
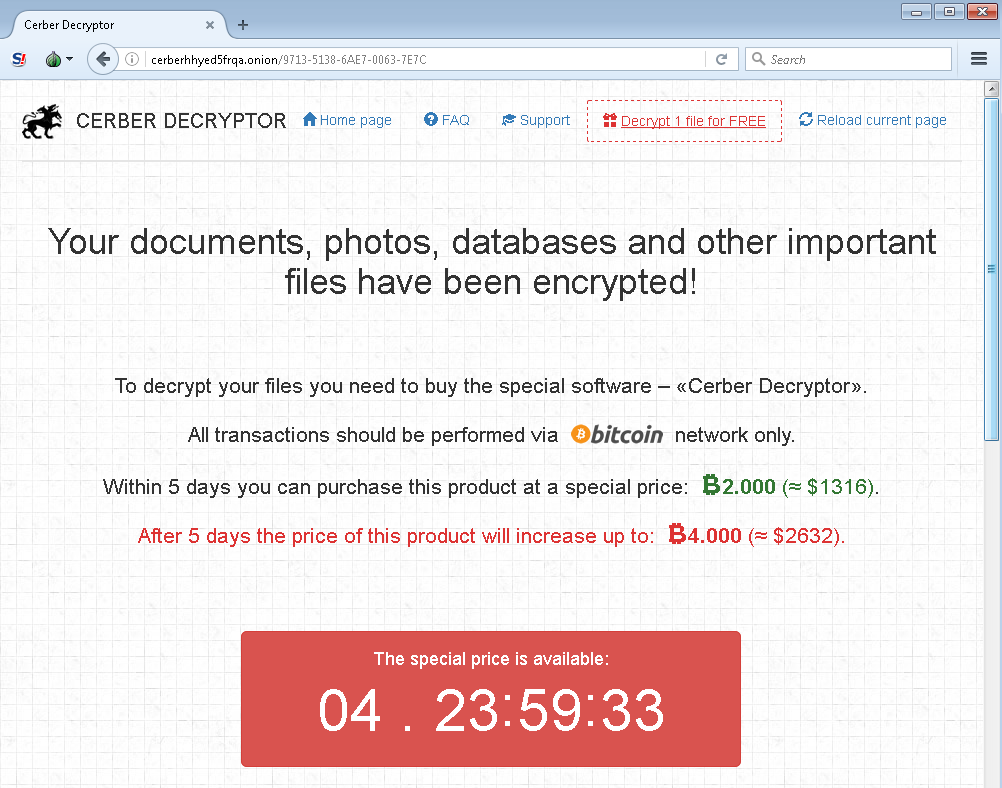
Cerber is yet another newer ransomware that has been gaining some traction over the past couple months, so we’re providing a breakdown of this new variant. First, here is how it looks:
Unlike some other ransomware variants, Cerber is certainly not going for aesthetics. It also lacks any type of GUI. However, it does change your background to an awful pixelated image of static that’s not comfortable to look at, but it achieves its goal of getting the victims’ attention.
The ransom text is quite extensive and attempts to answer as many questions as the victims might have. The end goal is to get the user to follow directions to install a layered tor browser so they can access the dark net and pay the ransom with Bitcoins. This is what the ransom portal looks like:
This Cerber variant specifically wants 2 BTC, which is a huge sum of money (around $1,300) compared to variants seen in the past. As with older types, there is a ‘late fee’ that doubles the ransom if it isn’t paid in the original time frame. It appears that this trend of charging more money is new and is continuing to catch on. Also included with Cerber are “freebies”, which means that you get one free decrypt of a file. This was introduced by coinvault in 2014 to great success, so now almost all ransomware types include it.
Webroot will catch this specific variant in real time before any encryption takes place. We’re always on the lookout for new threats, but just in case of new zero-day variants, remember that with encrypting ransomware, the best protection is going to be a good backup solution. This can be either through the cloud or offline external storage. Keeping it up to date is key so as not to lose productivity. Webroot has backup features built into our consumer product that allow you to have directories constantly synced to the cloud. If you were to get infected by a zero-day variant of encrypting ransomware, you can just restore your files back as we save a snapshot history for each of your files up to ten previous copies. Please see our community post on best practices for securing your environment against encrypting ransomware.
MD5 Analyzed:
c3cd90c3e406981bece559a43fe64414
383803a90293408e36063809319f5982
065033243f30b1e54241a932c5e706fd