When it comes to drive-by attacks, CryptXXX is king. In fact, out of all the exploit kits dropping payloads on victims, 80% result in CryptXXX. The creators attacked vulnerabilities in Flash Player, Java and Silver Light through using the Angler exploit kit, with malvertising helping boost their success. The malware authors were able to generate $3 Million per month almost exclusively from ransomware.
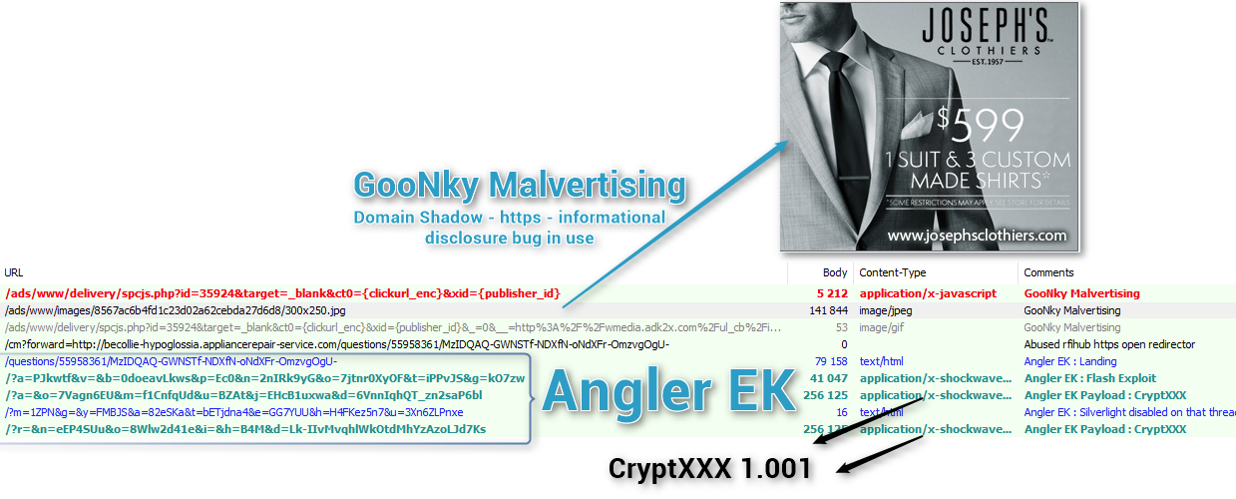
But how exactly does malingering work? In a nutshell, cyber criminals submit booby trapped advertisements to ad networks for a real-time bidding process. Malicious ads then rotate in with normal ads on legitimate, highly reputable sites. Users then visit these site and click on an infected ad. An invisible iframe injection then redirects the user to the exploit landing page, where a payload is then dropped. Here’s an example:
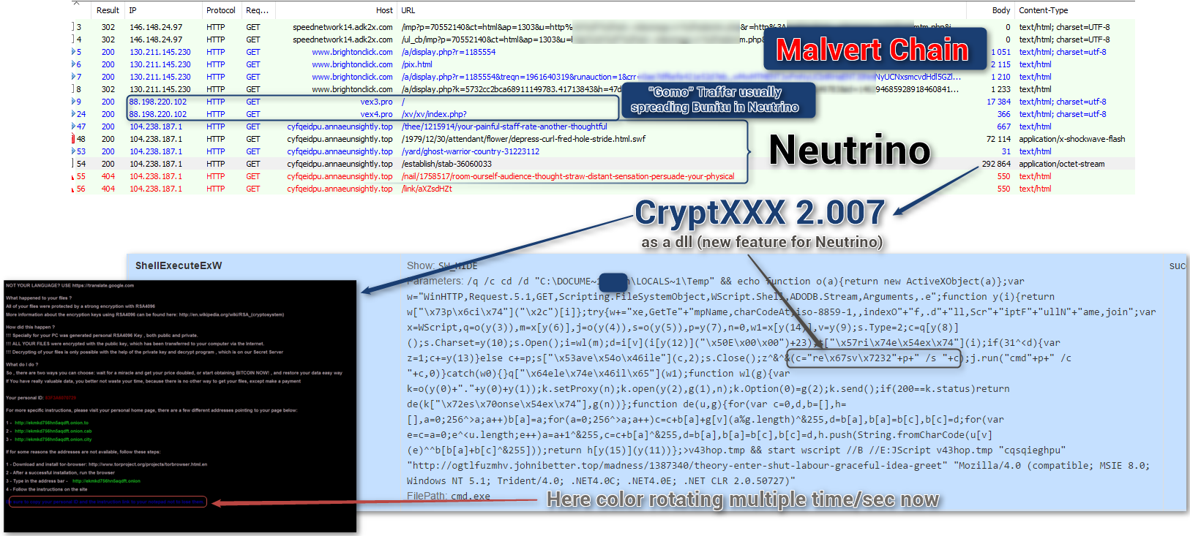
Since Angler was shut down earlier last month, CryptXXX was presumed to also die with it. However, it’s taken new life with the Neutrino exploit kit, and can now exploit out of plugins like WordPress. Here’s how this looks:
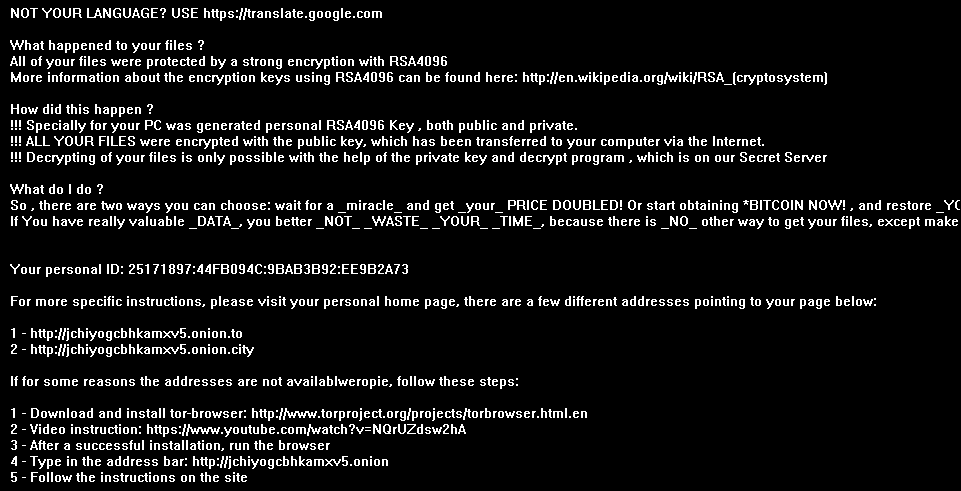
Once a user is unlucky enough to click an infected ad, a ransomware payload is dropped and they become the victim. Here are the instructions that are presented to victims. Pictured below, they are presented the form of a desktop background:
Once a user’s files are encrypted, the steps are the same as most ransomware – install a layered tor browser, then pay the ransom using bitcoins. This variant specifically only asks for 1.2 bitcoins ($800), which is the most ‘mild’ demand of recent ransomware variants, but the amount will double after 5 days if the ransom isn’t paid. It is worth noting that other sites have offered free decryptors for this malware, but they seldom last longer than a few days before the malware authors change it up yet again.
Webroot will catch this specific variant in real time before any encryption takes place. We’re always on the lookout for new and updated ransomware threats, but just in case of new zero-day variants, remember that with encrypting ransomware, the best protection is going to be a good backup solution. This can be either through the cloud or offline external storage. Keeping it up to date is key so as not to lose productivity. Webroot has backup features built into our consumer product that allow you to have directories constantly synced to the cloud. If you were to get infected by a zero-day variant of encrypting ransomware, you can just restore your files back as we save a snapshot history for each of your files up to ten previous copies. Please see our community post on best practices for securing your environment against encrypting ransomware.
MD5 analyzed
75EF6891AE7214AD17679CB88DC3B795
7BB58C27B807D0DE43DE40178CA30154
05825F3C10CE814CE5ED4AE8A74E91A2







thanks guardians at the gates!!!!!!!