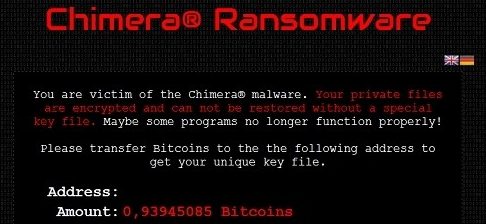
Encrypting ransomware is so popular now that competitors will sabotage one another to get the upper hand. This is refreshing for victims, however, as they reap the benefit of these potential clashes between cybercriminals. ‘Chimera Ransomware’ has just had its keys leaked to the public, which is fantastic news for anyone who has been a victim of this ransomware.
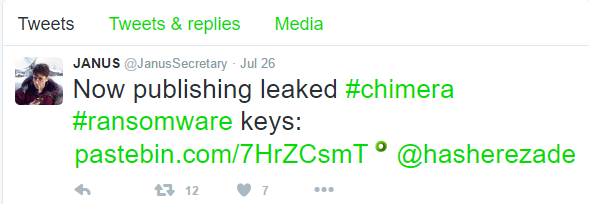
@JanusSecretary (presumed author of Mischa and Petya) was quick to tweet the news:
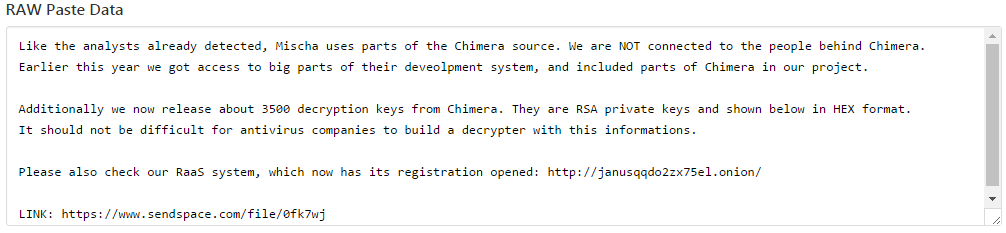
The keys are linked here which is a zip of the text file with over 3,500 keys. Below is a summary of the leak, where it is explained that Mischa used Chimera sourcecode. While the authors of Mischa and Chimera are not affiliated, they did get access to big parts of Chimera’s development system.
This allowed access to the decryption keys that have now been released. With these keys now released, it shouldn’t be too much longer before a decryption tool is created for all the victims of Chimera.
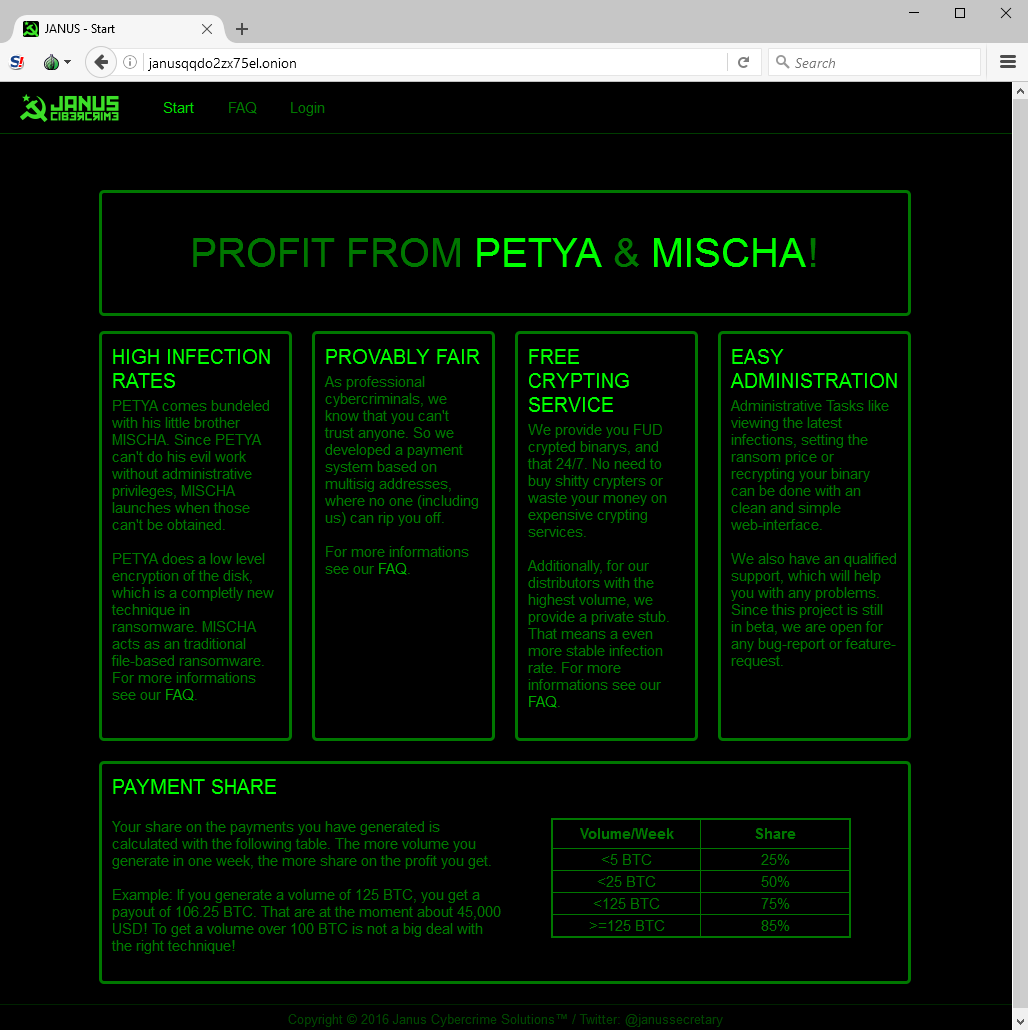
Also included is a shameless plug for his RaaS (Ransomware As A Service) portal, where anyone can create new ransomware payloads.
For any successful ransoms that result in payment, a cut will be taken by Janus based on how successful the ransoms are. For a complete rundown on RaaS variants check our our blogs on Ransom32 and Encryptor RaaS samples.