Cybercriminals are constantly experimenting with new ways to take money from their victims. Their tactics evolve quickly to maximize returns and minimize risk. The emergence of cryptocurrency has opened up new opportunities to do just that. To better understand today’s threat landscape, it’s worth exploring the origins of cryptocurrencies and the progress cybercriminals have made in using it to advance their own interests.
The FBI screen lock
Source: @DavidSGingras on Twitter
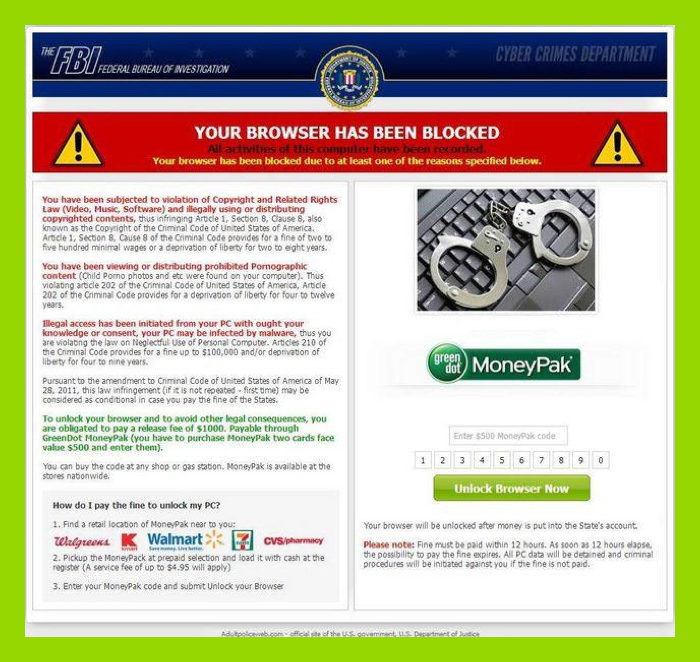
Many readers may remember the infamous FBI lock malware that would pop up and prevent users from using their computer at startup. The malware presented the (false) claim that the victim had downloaded copyrighted material illegally or had watched pornography.
This was a common and successful scam that made millions globally by localizing the “official” police entity in order to legitimize the threat. The money it made was transferred via Ukash and MoneyPak, which were essentially gift cards available at local convenience stores that could be loaded with specified amounts of cash. Victims would enter the pin on the back of the card to pay the criminals.
This method of collecting money wasn’t without risks for criminals, however. If enough victims reported the scam to law enforcement, they would try to find and identify those responsible (attention criminals obviously tried to avoid).
Bitcoin and Silk Road
While the Ukash and MoneyPack scams were still alive and well, another popular and anonymous black market called Silk Road was experimenting with Bitcoin as a payment system.
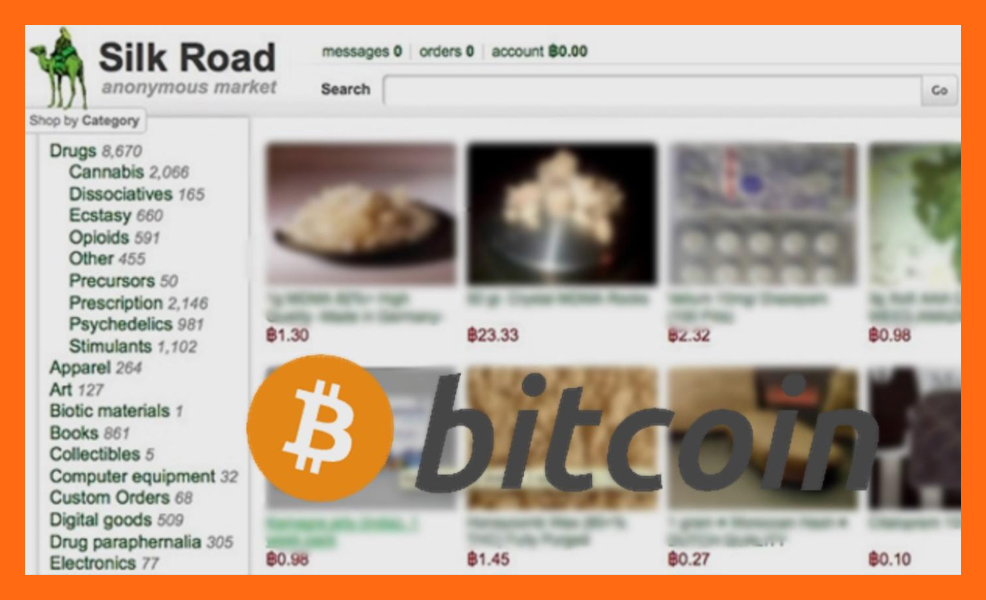
Silk Road was essentially an underground market on the encrypted dark web for goods otherwise illegal or extremely difficult to purchase in most countries. The site’s buyers and sellers remained effectively anonymous to one another and were almost impossible to track. For years this marketplace thrived and proved the efficacy of Bitcoin as a transactional system. Its success came to an abrupt halt in 2013, however, when the FBI seized Silk Road and arrested its founder.

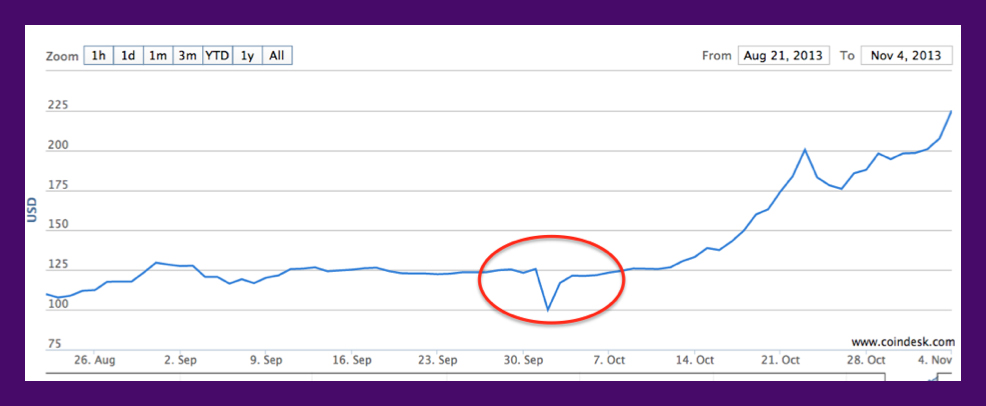
The shutdown initially caused a nosedive in Bitcoin’s market price, but it quickly bounced back to surpass its value even at the height of the Silk Road.
So, what contributed to the shift?
Source: coindesk.com
Enter CryptoLocker
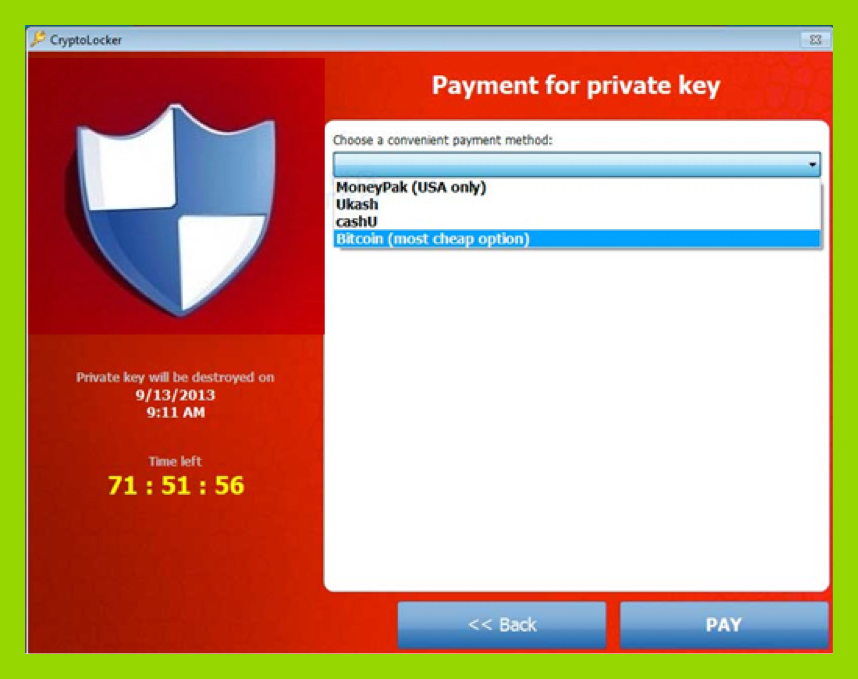
The first variants of Cryptolocker ransomware were seen in late September 2013. In terms of criminal business models, it was an instant success. Soon, many variants were infecting users around the world. Early editions accepted the still widely-used Ukash and MoneyPak as payment, but with a twist. Cryptolocker would provide a discount for Bitcoin payments. The proverbial Rubicon had been crossed in terms of cryptocurrencies receiving preferential treatment from cybercriminals. With ransomware rapidly rising to the top of the threat landscape, Bitcoin saw corresponding growth as fiat currencies were exchanged for it so ransoms could be paid.
Is Bitcoin Anonymous?
Not really. Since all Bitcoin transactions are recorded on a public ledger, they are available for anyone to download and analyze. Each time a victim pays a ransom, they’re given a Bitcoin address to which to send payment. All transactions to and from this address are visible, which, incidentally, is how the success of many ransomware campaigns is measured.
When a criminal wants to cash out Bitcoin, they typically need to use an exchange involving personal identifiable information. So, if a criminal isn’t careful, their victim’s Bitcoin wallet address can be tracked all the way to the criminal’s exchange wallet address. Law enforcement can then subpoena the exchange to identify the criminal. Criminals, however, are often able to keep this situation from unfolding by using tactics that prevent their “cash out” address from being flagged.

For a time, Bitcoin “mixers” offered to clean coins that were widely available on the dark web. Their methods involved algorithms that would split up and send dirty coins of varying amounts to different addresses, then back to another address clean, a process not unlike physical currency laundering. Yet, the process was not foolproof and did not work indefinitely. Once cryptocurrencies had gained significant legitimate adoption, several projects were started to search Bitcoin blockchain transactions for fraudulent activities. Chainalysis is one example.
Ransomware takes multiple cryptocurrencies
In the spring of 2014, a new cryptocurrency arrived. Dubbed Monero, it filled Bitcoin’s shoes, but without a public ledger that could be analyzed. Monero quickly became criminals’ most useful payment system to date. It uses an innovative system of ring signatures and decoys to hide the origin of the transactions, ensuring transactions are untraceable. As soon as criminals receive payment to a Monero wallet address, they’re able to send it to an exchange address and cash out clean, with no need to launder their earnings.

Monero started to see “mainstream” adoption by criminals in late 2016, when certain flavors of ransomware started experimenting with accepting multiple cryptocurrencies as payment, with Bitcoin, Ethereum, Monero, Ripple, and Zcash among the most common.
The Emergence of CryptoJacking
Monero has proven useful for criminals not just because it’s private. It also has a proof-of-work mining system that maintains an ASIC resistance. Most cryptocurrencies use a proof-of-work mining system, but the algorithm used to mine them can be worked by a specific chip (ASIC) designed to hash that algorithm much more efficiently than the average personal computer.
In this sense, Monero has created a niche for itself with a development team that maintains it will continually alter the Monero algorithm to make sure that it stays ASIC-resistant. This means Monero can be mined profitably with consumer-grade CPUs, sparking yet another trend among criminals of generating money from victims without ever delivering malware to their systems. This new threat, called “cryptojacking,” has gained momentum since CoinHive first debuted its mining JavaScript code in September 2017.
The original purpose of crypto-mining scripts, as described by CoinHive, was to monetize site content by enabling visitors’ CPUs to mine Monero for the site’s owners. This isn’t money from thin air, though. Users are still on the hook for CPU usage, which arrives in the form of an electric bill. While it might not be a noticeable amount for one individual, the cryptocurrency mined adds up fast for site owners with a lot of visitors. While CoinHive’s website calls this an ad-free way to generate income, threat actors are clearly abusing the tactic at victims’ expense.
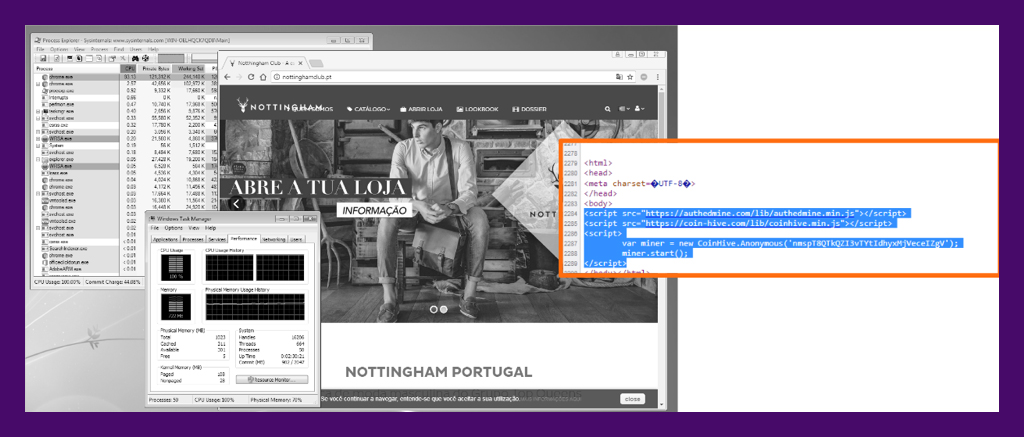
We can see in the image above that visiting this Portuguese clothing website causes the CPU to spike to 100 percent, and the browser process will use as much CPU power as it can. If you’re on a newer computer and not doing much beyond browsing the web, a spike like this may not even be noticeable. But, on a slower computer, just navigating the site would be noticeably sluggish.
Cybercriminals using vulnerable websites to host malware isn’t new, but injecting sites with JavaScript to mine Monero is. CoinHive maintains there is no need block their scripts because of “mandatory” opt-ins. Unfortunately, criminals seem to have found methods to suppress or circumvent the opt-in, as compromised sites we’ve evaluated rarely prompt any terms. Since CoinHive receives a 30 percent cut of all mining profits, they’re likely not too concerned with how their scripts are used. Or abused.
Cryptojacking becomes 2018’s top threat
Cryptojacking via hijacked websites hasn’t even been on the scene for a full year, and already it has surpassed ransomware as the top threat affecting the highest number of devices. After all, ransomware requires criminals to execute a successful phishing, exploit, or RDP campaign to deliver their payload, defeat any installed security, successfully encrypt files, and send the encryption keys to a secure command and control server—without making any mistakes. Then the criminals still have to help them purchase and transfer the Bitcoin before finally decrypting their files. It’s a labor-intensive process that leaves tracks that must be covered up.
For criminals, cryptojacking is night-and-day easier to execute compared to ransomware. A cybercriminal simply injects a few lines of code into a domain they don’t own, then waits for victims to visit that webpage. All cryptocurrency mined goes directly into the criminal’s wallet and, thanks to Monero, is already clean.
That’s why you should expect cryptojacking to be the preferred cyberattack of 2018.
Questions? Drop me a line in the comments below.






