Although phishing has been around in various forms since the 1980s, our research shows it continues to evolve—and remains a major threat. These days, phishing tactics have gotten so sophisticated, it can be difficult to spot a scam—particularly in the case of hijacked email reply chains. Let’s look at a concrete example.
Imagine you’re a purchaser for a concrete supplier, and you get an email from a regular client about an order. In that email, you can see this client, Michael, has been exchanging messages with your colleague, Jill. The email addresses, corporate logos, and everything about the email chain look 100% legitimate. You’ve even met Michael in person, so you know he’s trustworthy.
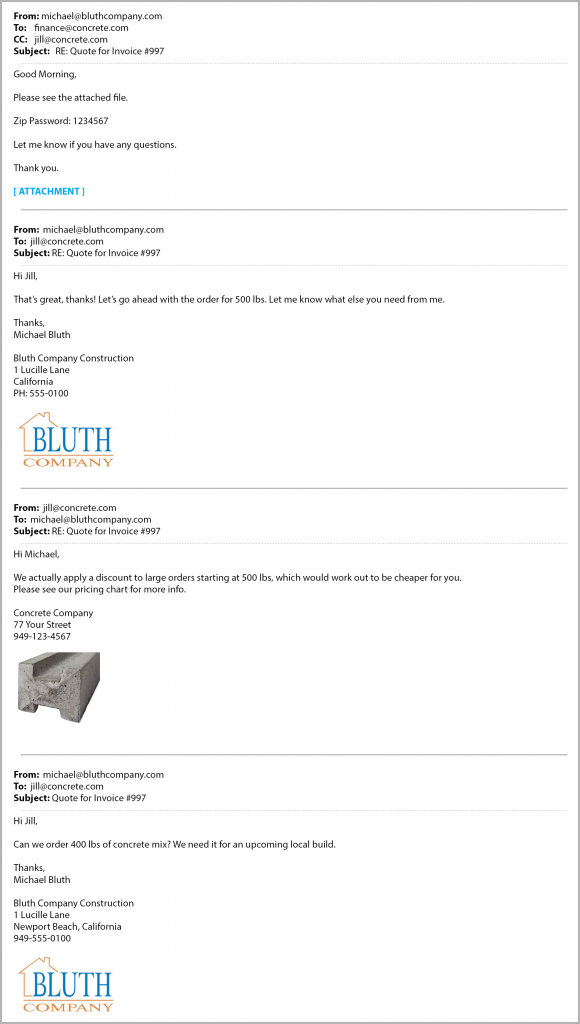
In this case, the conversation details are convincing to you—because they’re real. Someone gained access to your colleague’s email and took over a legitimate conversation about purchases, then forwarded it to you with a malicious payload attached.
A message like this is very likely to get through any email filtering, and you’d probably open it, since it looks like it’s from a trusted sender.
Had you opened the file in this hypothetical scenario, you might have gotten infected with Emotet or another banking Trojan, such as Ursnif / Gozi.
“Phishing attacks increased 36%, with the number of phishing sites growing 220 percent over the course of 2018.” – Webroot Inc. “2019 Webroot Threat Report.” (March 2019)
Ursnif / Gozi Campaigns
The difference between an ordinary phishing attack and a hijacked email chain really comes down to believability. The criminals behind these campaigns take their time breaking into email accounts, watching business conversations, negotiations, and transactions, then launching their attempts at plausible moments when the recipient’s guard is most likely to be down. Most commonly, these attacks have been attributed to Ursnif/Gozi campaigns. Webroot has seen quite a few cases of these hijacked emails with the same style of phishing text and nearly identical payloads. There are numerous reports online as well.
In a malware campaign like this one, it really doesn’t matter whose account the malicious actors have broken into. If you receive an email from your project manager, a sales colleague, the finance department, a particular client, or anyone else that bears the markers of a legitimate, ongoing email conversation, the attack is highly likely to succeed.
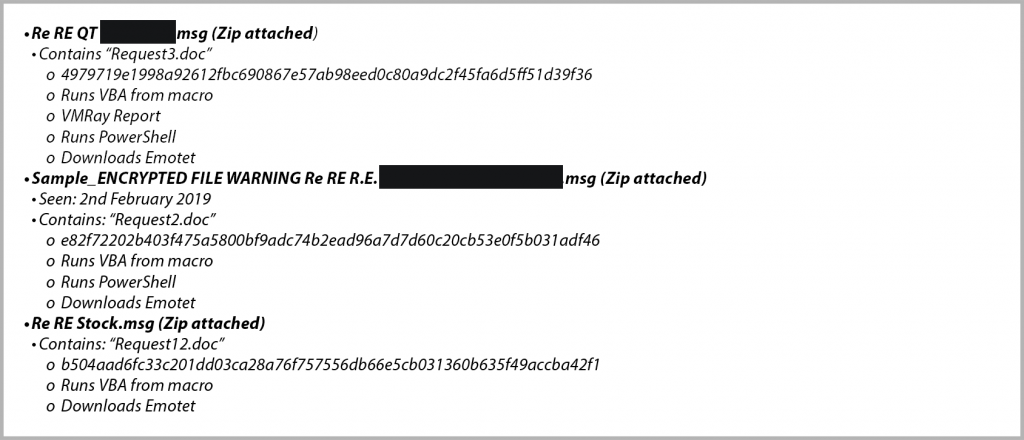
Samples
Seen since last November: all email bodies had a long list of replies, but all had the following message.

This would suggest they are all samples that can be attributed to the same gang. Each had .zip files attached with convincing names related to the business at hand, which contained Microsoft® Word documents with filenames that started with “request”.
What You Can Do
Faced with such plausible attacks, it might seem impossible to stay safe. But there are a few tips that can keep you protected. First, never turn macros on, and never trust a document that asks you to turn macros on, especially if it’s a Microsoft® Office file that wants you to show hidden content. Macros are a very common attack vector.
Second, always make sure to keep your operating system up to date, especially Microsoft Office programs.
Third, you likely already mistrust emails from people you don’t know. Now, it’s time to turn that suspicion onto trusted senders too. Attackers commonly try to spoof email addresses to look like those you’re familiar with, and may even gain control of an email account belonging to a person you know. Always err on the side of caution when it comes to emails asking you to download attachments.
Fourth, it’s important to protect your own email account from being hijacked. Attackers can use techniques like alternate inboxing to send messages from your account without your knowledge. Be sure to secure your account with strong passwords, 2-factor authentication, or use a secure password manager. Encourage friends and colleagues to do the same.Finally, if you’re suspicious of an email, the best way to check its legitimacy is to pick up the phone. If you know the sender personally, ask them about the message in person or via phone. Or, if you receive a message from a company, look up their publicly listed phone number (do not use the number provided in the email) and call them.
How Webroot Protection Can Keep You Safe
- Webroot security for computers, smartphones, and tablets blocks malicious scripts, downloads, and executables. (However, you should still exercise caution and common sense, regardless which internet security solutions you use.)
- For businesses and managed service providers, our portfolio of integrated, next-generation security includes Endpoint Protection, DNS Protection, and Security Awareness Training for end users.
For more information on these types of attacks, you can read the following articles:
- unit42.paloaltonetworks.com/unit42-freemilk-highly-targeted-spear-phishing-campaign/
- www.zixcorp.com/resources/blog/october-2018/new-email-attack-hijacks-a-legitimate-email-thread
- www.avanan.com/resources/phishing-alternate-inbox
- isc.sans.edu/forums/diary/Have+You+Seen+an+Email+Virus+Recently/24634/






