These are the places your digital tracks can be dug up. With a little sleuthing.
Experts have warned for years of the risks of using public computers such as those found in libraries, hotels, and airline lounges.
Many warnings focused on the potential for hackers to plant keystroke loggers, or intercept data as it flows across the internet. Indeed, in 2014, the National Cybersecurity and Communications Integration Center of the U.S. Secret Service issued an advisory for “owners, managers, and stakeholders in the hospitality industry” concerning data breaches. The text of the advisory claimed, “The attacks were not sophisticated, requiring little technical skill, and did not involve the exploit of vulnerabilities in browsers, operating systems or other software.” A 2014 announcement may seem to be an outdated reference, except that the recent Marriott data breach of over 300 million records was attributed to an attack in…wait for it…2014.)
But spyware and keyloggers aren’t the most common threat to the users of business center and other public computers. Forgetfulness, operating systems, applications, and temporary files are high up on the list. For several years I have searched public computers, mostly at hotels, to see what kinds of information people have left behind. It’s been an interesting passion project, to say the least.
Uncovering a Very Public Digital Paper Trail
The first places I look are the documents, downloads, desktop, and pictures folders. The pictures folder typically yields the least interesting information, usually pictures of groups of drunken people, group gatherings at restaurants, weddings, or cats.


The desktop, document, and occasionally downloads folders are where most documents are inadvertently left behind. Some interesting samples I’ve discovered include a spreadsheet of faculty merit raises at a university in Texas, including the names of professors, their departments, their current salaries, and their projected raises. Another was the assignment of a chief officer to a ship belonging to one of the largest shipping companies in the world. It included the officer’s name, address, phone number, vessel name, date of assignment, and contact information.
I have come across corporate audits and strategic business plans. Recently, I discovered a document called “closing arguments” created by a district attorney. When possible, I contact the owners of the information to help them understand the risks of using public computers for sensitive work. I rarely hear back, however the DA did thank and assure me the document was a training example.
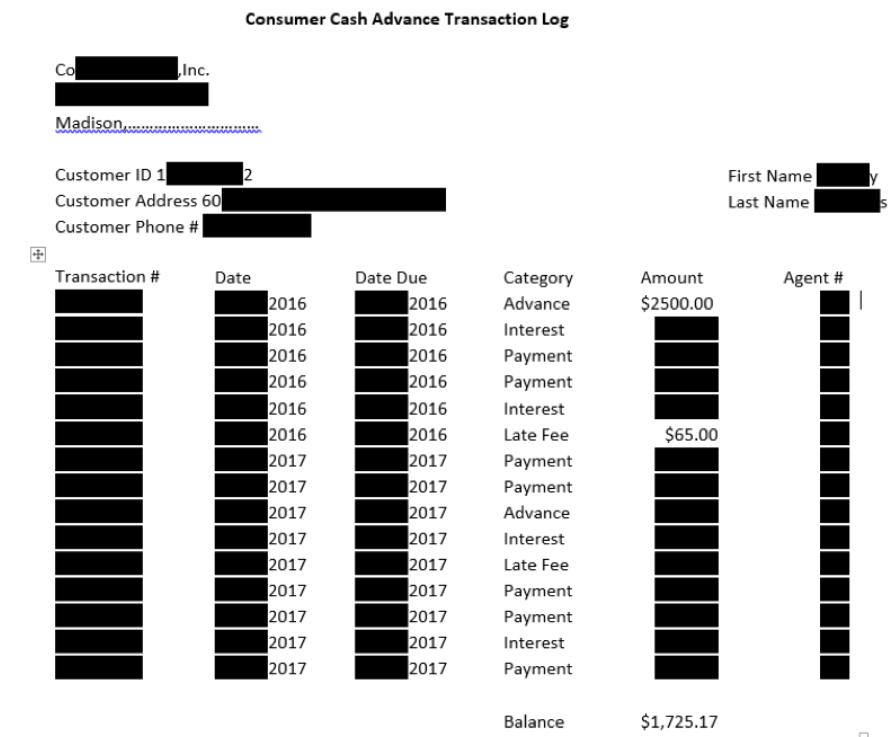
The biggest menace, however, has been the temporary files folders, which include auto-saved documents and spreadsheets, as well as attachments. It is in the Temporary Internet Files folder that I have uncovered complete emails, and even a webpage including a bank statement detailing a large balance, the account holder’s name, sources of income, and the names and addresses of places he had done business. Of all of the temporary files I have discovered, documents belonging to businesses’ employees have been the most unsettling.
If you must, take precautions
There is some good news concerning the safety of public computers. Due to technology changes, I no longer find the contents of emails in the Temporary Internet Files folder. But we’re far from out of the woods. I have found my inbox cached, including pictures within emails and even a PDF that had not yet opened.
Deleting temporary internet files is a good habit, but there are multiple locations that temporary files are stored. Documents edited on public computers remain of particular concern. Due to auto-save features, it’s possible to open a document on a thumb drive and leave auto-saved documents behind on the computer. Now in normal operating circumstances and with current operating systems and Office applications, this is not likely to happen. But errors like OS and application crashes will leave these copies behind. Microsoft Word and Excel will even proactively offer these auto-saved documents to the next user of these applications
Other than finding and deleting information left behind, my use of public computers is limited to reading online articles, checking the weather, and performing internet searches. What personal information you are willing to leave behind on a public computer depends on your risk tolerance. But it’s important to note that accessing corporate data on public computers could result in an inadvertent violation of company policies involving confidential data.
Although I still find public computers running Windows XP, there is a growing shift in the hospitality industry to use Kiosk applications. These provide limited functionality combined with locked-down security configurations. Access to the start menu is not possible and functionality is limited to desktop applications. Printing of boarding passes is a common allowed application. Reading web email is sometimes allowed, though I don’t recommend it because it requires entering a password. The risk of password compromise may be low, but the value of practicing quality security habits leads me to advise against it. If you must, consider changing your email password the next time you log onto a private computer.
If you happen to be using a public computer without a Kiosk interface, would you be so kind as to copy this blog, paste it into a Word document, and save it on the public computer to help inform the next user? They may end up paying it forward.






