
by Dan Para | Jun 11, 2013 | Threat Lab
It seems simple enough, I want to install Adobe Flash Player so I search for “flash player download and click on the first result, right?
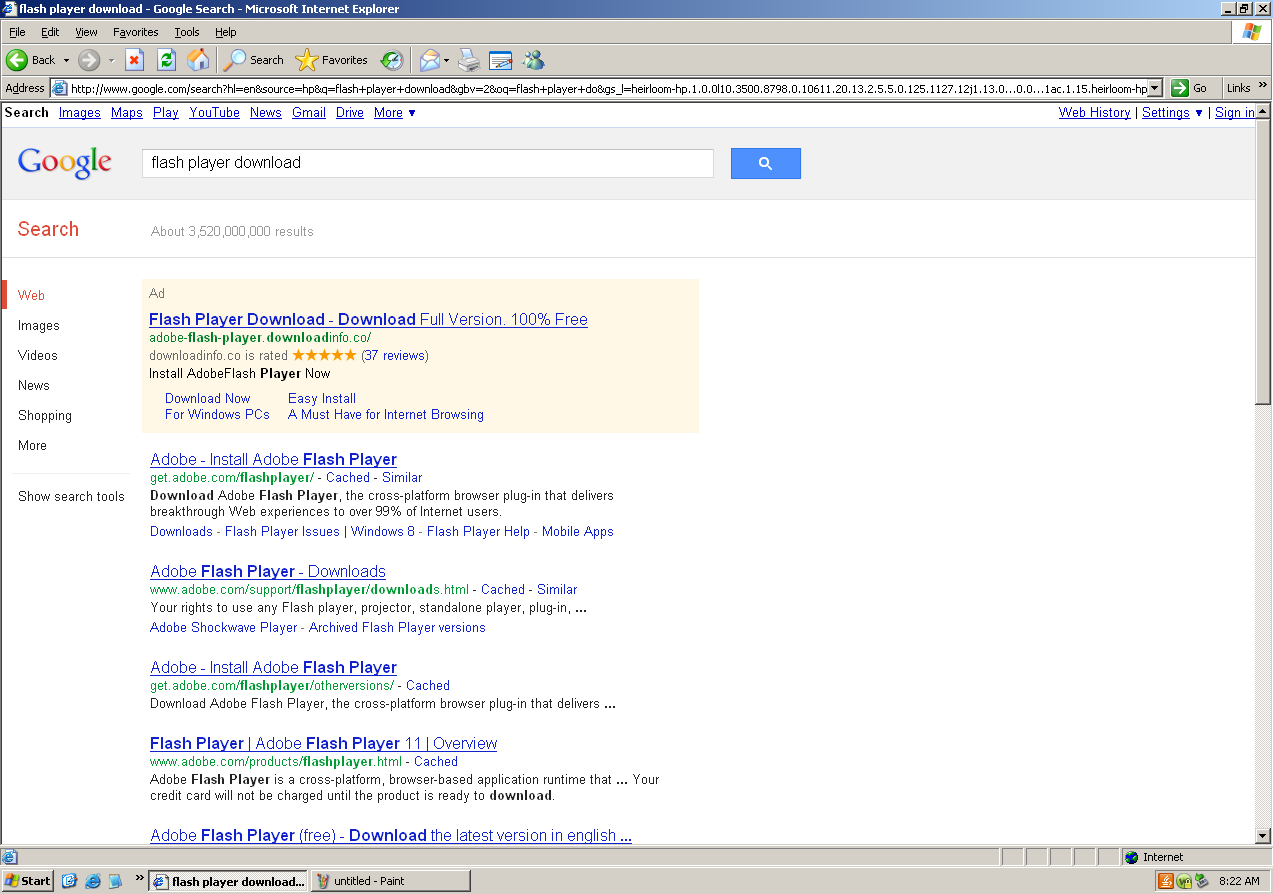
Ignoring the second link which doesn’t have a five star rating and 37 reviews, I’m brought to a page called downloadinfo.com.
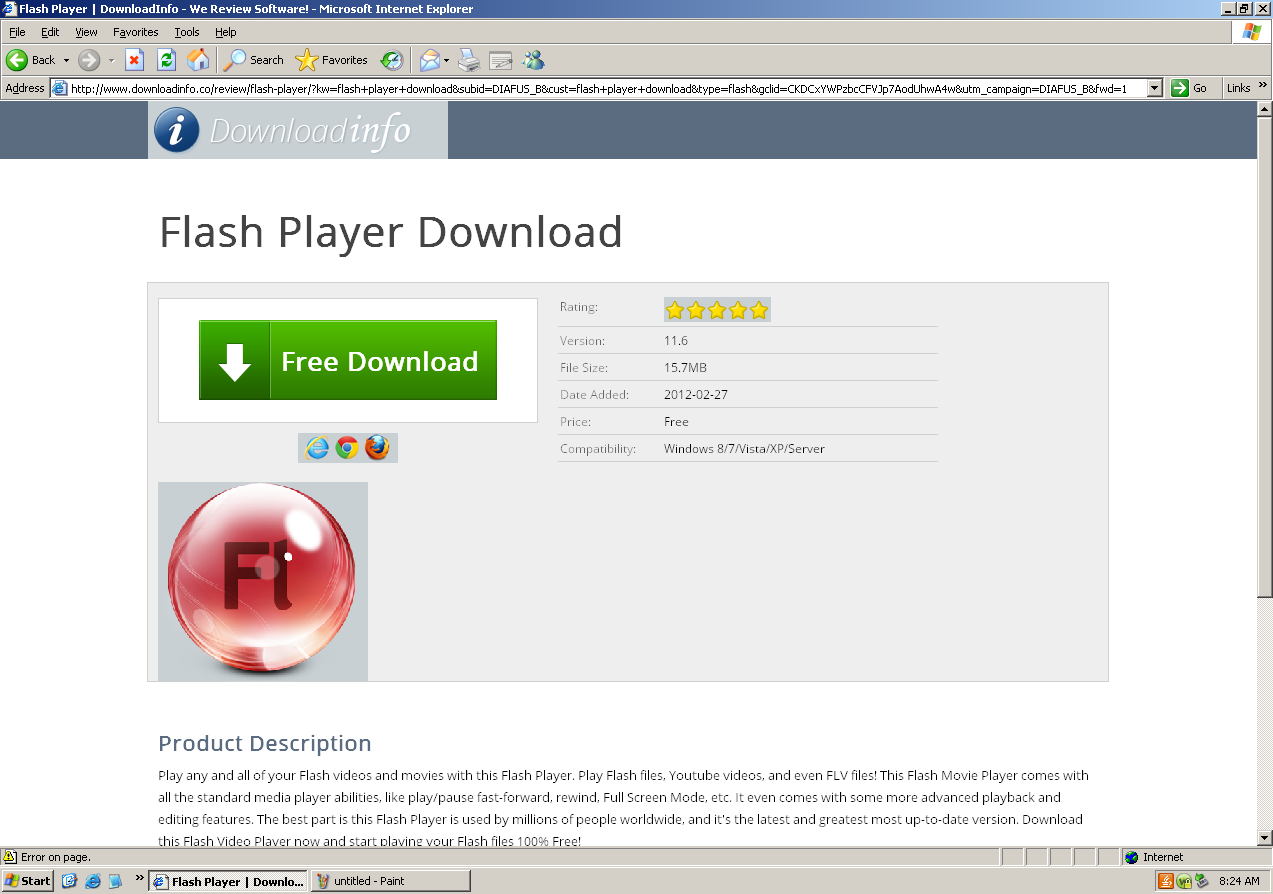
I click the download button, click through the download dialog box and run dialog box, come to the Optimum Download screen for my Free Flash Player. Click.
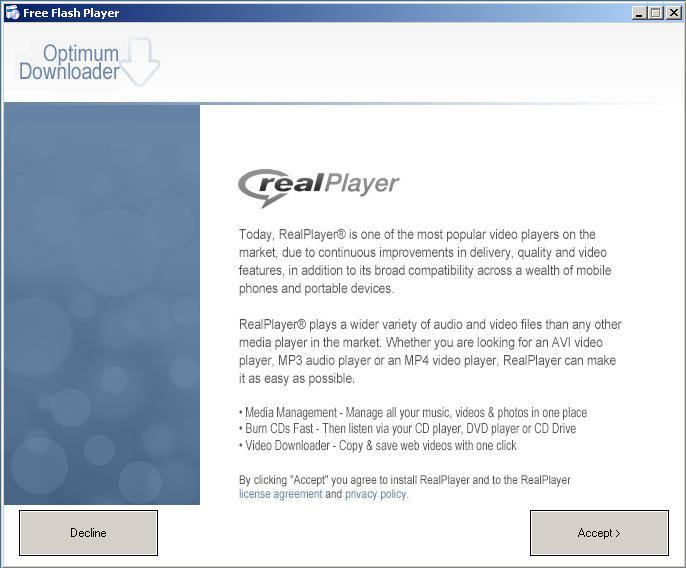
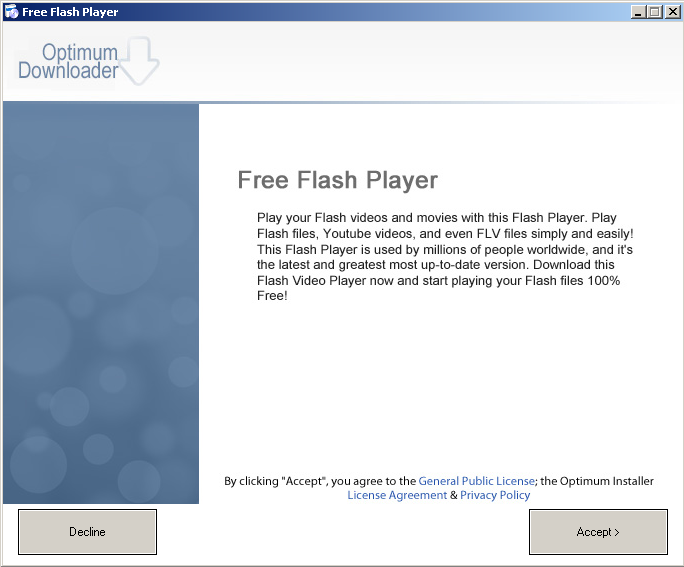 Let’s see what this installs. First up is RealPlayer. Click.
Let’s see what this installs. First up is RealPlayer. Click.
 Next up is some program called Solid Savings. Click.
Next up is some program called Solid Savings. Click.
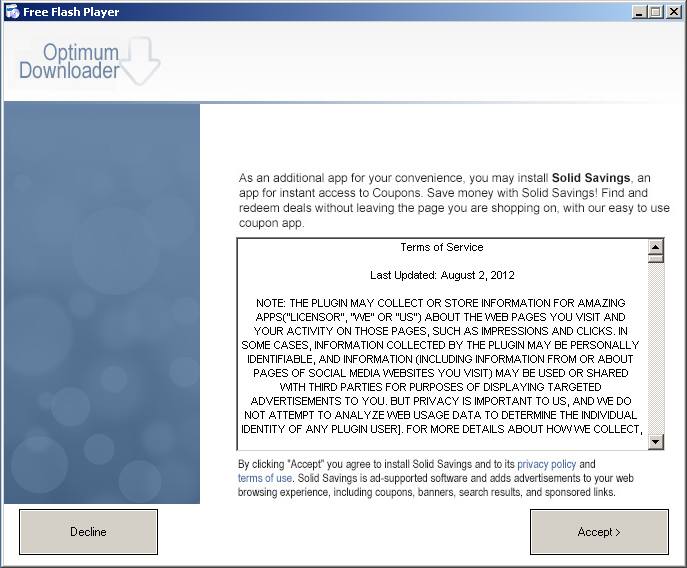
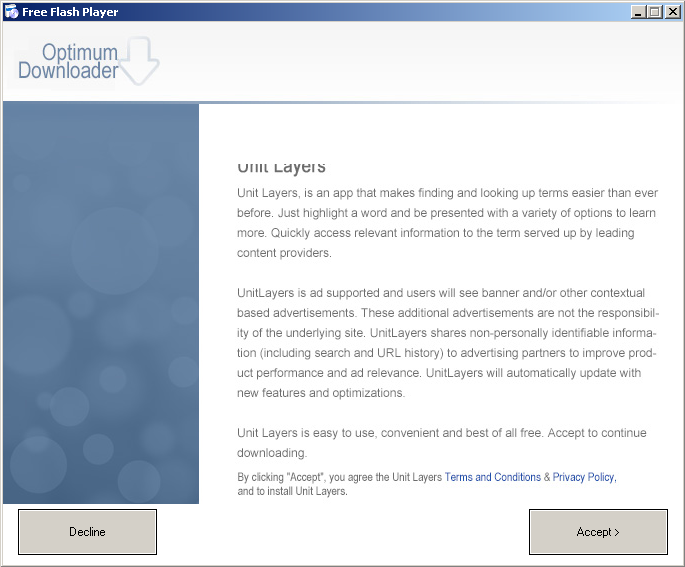
Then something called Unit Layers. Click.
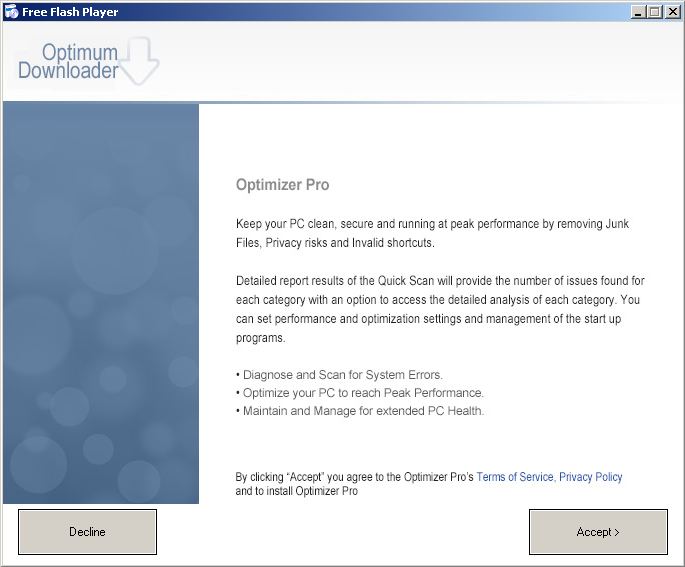
That seems like a lot of software to install in order to get my Adobe Flash Player, but we’re not done yet, here’s something called Optimizer Pro. Click.
Okay, now we’re finally installing…
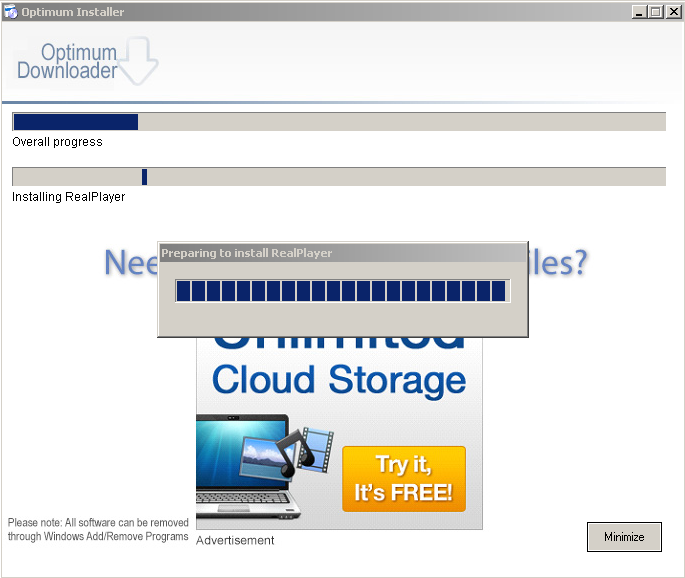
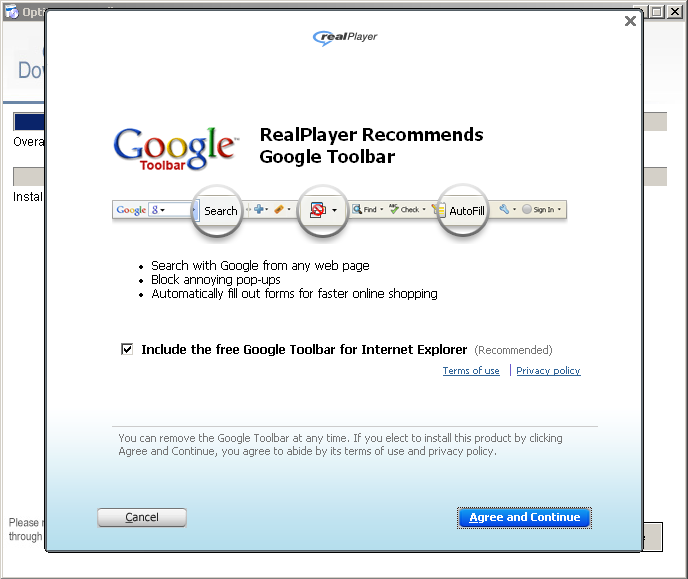
Now RealPlayer, which was bundled with Flash Player wants to install the Google Toolbar? A bundle within a bundle? Okay… Click.
I should have my Flash Player any moment now… Wait a minute. VLC media player? Where’s the Adobe Flash Player I started out downloading?
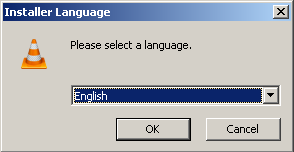
Okay, VLC media player will play flash files, but I really expected to be getting Adobe Flash Player (Seriously, while I was doing this I was hoping this was one of the “download managers” that actually downloads and installs the actual Adobe Flash Player along with all of this other software. I was surprised and disappointed to get VLC media player instead.) The link I had clicked on initially displayed it’s URL as adobe-flash-player.downloadinfo.co/ and included the text “Install AdobeFlash Player Now” so you would think that link would get you Adobe Flash Player, but no, it was just a misleading ad that appeared as the top result on the search page that led to a “download manager” which bundled a bunch of additional software along with VLC media player, which can be downloaded for free. The downloadinfo.com website even had fine print stating that “This software may be available free elsewhere” which was hyperlinked to the download page for VLC media player!

So how should you install Adobe Flash Player? Or any other software for that matter? In this case I could have clicked on the second link which would have brought me directly to the download page for Adobe Flash Player (and unchecked the box to opt-out of installing McAfee Security Scan Plus of course.) In general we recommend downloading software directly from the software company’s website whenever possible, otherwise you could end up installing all sorts of additional, potentially unwanted software along with the free software that you wanted to download – or even a completely different program like I just did.

by Blog Staff | Jun 11, 2013 | Threat Lab
Have you sent an eFax recently? Watch out for an ongoing malicious spam campaign that tries to convince you that there’s been an unsuccessful fax transmission. Once socially engineered users execute the malicious attachment found in the fake emails, their PCs automatically join the botnet of the cybercriminals behind the campaign.
More details:
(more…)

by Blog Staff | Jun 10, 2013 | Threat Lab
Opportunistic scammers have just launched a targeted spam campaign impersonating the UN Refugee Agency (UNHCR) in an attempt to trick users into handing over their complete credit card details as they supposedly make a donation to support Syria’s refugees.
Needless to say, this scam is seeking full access to your credit card details through a fraudulent Web site that’s directly collecting the information, has no SSL support, and is featuring a bogus “Verified by Verisign” logo in an attempt to add more legitimacy in the eyes of the prospective victims.
More details:
(more…)

by Blog Staff | Jun 7, 2013 | Threat Lab
Aiming to capitalize on the multi-billion gaming market, cybercriminals actively data mine their botnets for accounting credentials, not just for popular gaming platforms, but also the actual activation keys for some of the most popular games on the market.
A newly launched e-shop aims to monetize stolen accounting credentials, not just for gaming platforms/popular games such as Origin and Uplay, but also for a variety of online services such as Hulu Plus, Spotify, Skype, Twitter, Instagram, Tumblr and Freelancer. How much does it cost to buy pre-ordered access to Battlefield 4? What about a compromised Netflix or Spotify account? Let’s find out.
More details:
(more…)

by Blog Staff | Jun 6, 2013 | Threat Lab
By Dancho Danchev
Our sensors recently picked up an advertisement using Yieldmanager’s ad network, enticing users into downloading the iLivid PUA (Potentially Unwanted Application) on their PCs. Operated by Bandoo Media Inc., the application installs the privacy invading “Searchqu Toolbar”.
More details:
(more…)

by Blog Staff | Jun 5, 2013 | Threat Lab
By Dancho Danchev
Opportunistic pharmaceutical scammers are currently spamvertising tens of thousands of bogus emails impersonating Facebook’s Notification System in an attempt to trick users into clicking on the links, supposedly coming from a trusted source. Once users click on the links found in the fake emails, they’re exposed to counterfeit pharmaceutical items available for purchase without a prescription.
More details:
(more…)

by Blog Staff | Jun 4, 2013 | Threat Lab
Remember the E-shop offering access to hacked PCs, based on malware ‘executions’ that we profiled last month?
We have recently spotted a newly launched, competing E-shop, once again selling access to hacked PCs worldwide, based on malware ‘executions’. However, this time, there’s no limit to the use of (competing) bot killers, meaning that the botnet master behind the service has a higher probability of achieving market efficiency compared to their “colleague.” Additionally, the botnet master won’t have to manually verify the presence of bot killers and will basically aim to sell access to as many hacked PCs as possible.
More details:
(more…)

by Blog Staff | Jun 3, 2013 | Threat Lab
Utilizing the very best in ‘malicious economies of scale’ concepts, cybercriminals have recently released a privilege-escalating Web-controlled mass iFrame embedding platform that’s not just relying on compromised FTP/SSH accounts, but also automatically gains root access on the affected servers in an attempt to target each and every site hosted there. Similar to the stealth Apache 2 module that we profiled back in November, 2012, this platform raises the stakes even higher, thanks to the automation, intuitive and easy to use interface, and virtually limitless possibilities for monetization of the hijacked traffic.
Let’s take an exclusive look inside the new platform, offer screenshots of the platform in action, discuss its key features, the pricing scheme, and discuss why its release is prone to cause widespread damage internationally, given the obvious adoption that’s beginning to take place.
More details:
(more…)

by Blog Staff | May 31, 2013 | Threat Lab
We have just intercepted yet another spamvertised malware serving campaign, this time impersonating Vodafone U.K, in an attempt to trick the company’s customers into thinking that they’ve received an image. In reality, once users execute the malicious attachments, their PCs automatically join the botnet operated by the cybercriminal.
More details:
(more…)

by Blog Staff | May 30, 2013 | Threat Lab
Largely thanks to the increasing availability of easy to use DIY (do-it-yourself) DDoS bots, we continue to observe an increase in international cybercrime-friendly market propositions for ‘DDoS for hire’ services. And whereas these services can never match the bandwidth capabilities and vendor experience offered by their Russian/Eastern European counterparts, they continue to empower novice Internet users with the ability to launch a DDoS attack against virtually anyone online.
In this post, I’ll profile a recently launched marijuana themed DDoS for hire service and emphasize on how, despite it’s built in pseudo-anti abuse process, the service is prone to be abused by novice cybercriminals looking for cost-effective ways to cause disruption online.
More details: (more…)

 Let’s see what this installs. First up is RealPlayer. Click.
Let’s see what this installs. First up is RealPlayer. Click. Next up is some program called Solid Savings. Click.
Next up is some program called Solid Savings. Click.














