Cybercriminals are currently spamvertising millions of emails impersonating U.S Airways, in an attempt to trick users into clicking on the malicious links found in the legitimately looking emails. Let’s dissect the malicious campaign, and expose its dynamics.
More details:
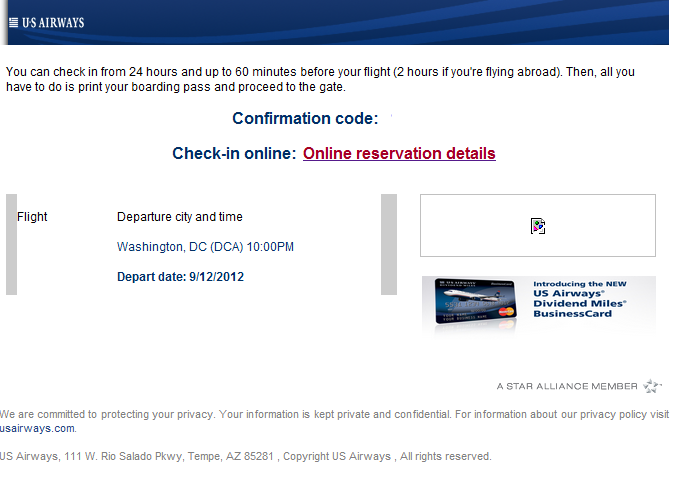
Sample screenshot of the spamvertised US Airways themed email:
Spamvertised compromised URL: hxxp://raintree.on.ca/depdetails.html
Sample client-side exploits serving URL: hxxp://blue-lotusgrove.net/main.php?page=559e008e5ed98bf7 – 203.91.113.6 (AS24559); Email: verdadress@consultant.com
Sample client-side exploits served: CVE-2010-1885
Responding to the same IP 203.91.113.6 (AS24559), are also the following malicious domains:
seneesamj.com
centennialfield.net
dushare.net
afgreenwich.net
bode-sales.net
cat-mails.net
nitor-solutions.net
gsigallery.net
atfood.ru
indyware.ru
citgbgmgrn.com
Detection rate for a sample Java script redirection: MD5: 5c5a3c6e91c1c948c735e90009886e37 – detected by 3 out of 42 antivirus scanners as Mal/Iframe-W
Upon successful client-side exploitation, the campaign drops MD5: 9069210d0758b34d8ef8679f712b48aa on the infected hosts, detected by 6 out of 42 antivirus scanners as Trojan.Winlock.6049; W32/Cridex.R
Upon execution, the sample phones back to 199.71.213.194:8080/mx/5/B/in/ (AS40676).
More MD5’s are known to have phoned back to the same IP, for instance:
MD5: 34cb2d621d61df32ae3ccf1e69007b8e
MD5: f621be555dc94a8a370940c92317d575
MD5: fd985d376b66af6e27a62ef91d7b0ce8
These MD5s also phone back to related command control servers part of the malicious campaign, such as:
173.224.208.60:8080
188.40.0.138:8080
192.220.87.172:8080
199.71.213.194:8080
200.108.18.158:8080
203.113.98.131:8080
203.172.140.202:8080
206.223.154.130:8080
219.255.134.110:8080
59.90.221.6:8080
66.242.19.36:8080
72.167.253.106:8080
72.18.203.140:8080
82.165.147.190:8080
83.238.208.55:8080
85.25.147.73:8080
The last time we intercepted the same HTML template being used in the wild, was in April 2012. Back then, we found an identical campaign structure between the US Airways themed campaign and the “Spamvertised Verizon-themed ‘Your Bill Is Now Available’ emails lead to ZeuS crimeware” ; “Spamvertised LinkedIn notifications serving client-side exploits and malware“ campaigns, leading us to the conclusion that it’s the same cybercriminal/gang of cybercriminals launching these attacks.
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.