Verizon Wireless customers, beware!
For over a week now, cybercriminals have been persistently spamvertising millions of emails impersonating the company, in an attempt to trick current and prospective customers into clicking on the client-side exploits and malware serving links found in the malicious email.
Upon clicking on any of the links, users are exposed to the client-side exploits served by the latest version of the Black Hole Exploit Kit.
More details:
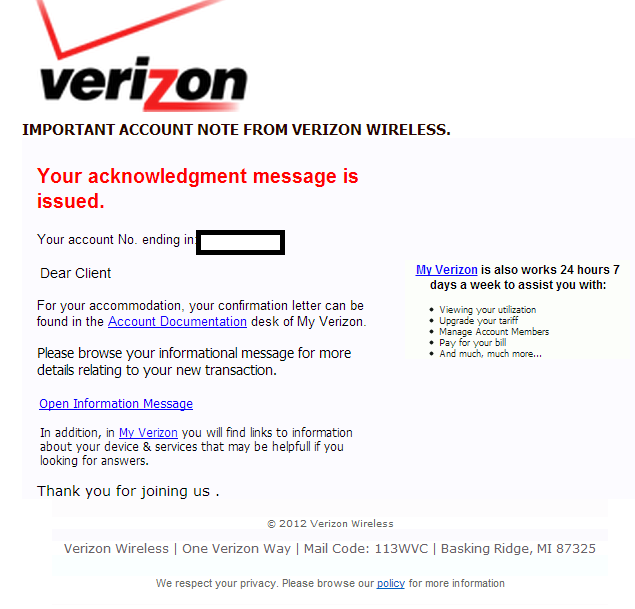
Screenshot of the spamvertised email:
Spamvertised malicious URLs: hxxp://coaseguros.com/components/com_ag_google_analytics2/notifiedvzn.html; hxxp://clinflows.com/components/com_ag_google_analytics2/vznnotifycheck.html
Client-side exploits serving URL: hxxp://strangernaturallanguage.net/detects/notification-status_login.php?mzuilm=073707340a&awi=45&dawn=04083703023407370609&iwnjdt=0a000300040002
Sample client-side exploits served: CVE-2010-0188
Upon successful client-side exploitation, the campaign drops MD5: b8d6532dd17c3c6f91de5cc13266f374 – detected by 26 out of 44 antivirus scanners as Trojan-Spy.Win32.Zbot.fkth
Once executed, the sample phones back to tuningmurcelagoglamour.ru, tuningfordmustangxtremee.ru – 146.185.220.28, AS58014
Name servers used in the campaign: ns1.2ns.info
The same name server is also offering DNS services to the following malicious domains, part of the campaign’s infrastructure:
100zakazov.ru
1waybet.com
2domains.net
a-dessin.com
aconstance.com
adata.ru
apinosoft.com
arenda24.net
aventadortuningrsport.ru
avstraliya.org
babyliss.net.ru
battlefieldmoon.com
beaddreamin.com
bublik.com
cantcuffus.com
cdaparty.com
centrizone.com
chelny-holod.ru
cmsstore.net
co-ltd.net
creatoric.com
di1.ru
djbm.ru
es-sahafa.com
ext.lv
fe-nix.ru
flashka.info
fleshka.ru
fordmustangtuninglabs.ru
fuck-access.com
garudakr.com
gaypirates.ru
gazinstroy.ru
genumesarider.ru
gis.ru
gloriousbabeporn.com
goslotto.ru
hedonism.ru
it-event.ru
itnote.info
jasminlive.ru
karpenkov.ru
lavka-chudes.ru
legendarno.biz
leonid.info
lithoart.net
lodka.tv
lyubov.net
macd.ru
migalki.info
milkyart.pp.ua
morbo.ru
myfilmix.ru
navtat.ru
ngksint.com
nnm.cc
nunta-ta.com
o001oo.ru
orgfin.ru
positime.ru
prisnilos.su
promstok.ru
qsba.com.ua
qtel.ru
rainbowlizard.net
rock.od.ua
rospromportal.ru
rpfm.ru
ru116.ru
rukazan.ru
salespb.ru
sellbrand.net
sextyumen.ru
shamaili.ru
shtin.com
sizov.biz
skripov.com
skyis.me
skynetcompany.ru
smscent.com
spypdf.com
stockmap.ru
synapticwave.com
tanque.biz
tropeonline.com
villaside.com
vipstudent.org
vivatvictoria.ru
warezzz.info
wn-travel.com
xmages.net
The last time we intercepted a Verizon Wireless themed malicious campaign was in March 2012. We expect to see more campaigns impersonating this company, thanks to the cybercriminal’s proven tactic of rotating the impersonated brands.
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.