
by Blog Staff | Feb 13, 2013 | Industry Intel, Threat Lab
Throughout the past year, we observed an increase in the availability of malicious (DIY) tools and services that were once exclusively targeting sophisticated cybercriminals, often operating within invite-only cybercrime-friendly Web communities. This development is a clear indication that the business models behind these tools and services cannot scale, and in order to ensure a sustainable revenue stream, the cybercriminals behind them need to change their tactics – which is exactly what we’re seeing them do.
By starting to advertise these very same malicious (DIY) tools and services on publicly accessible forums, they’re proving that they’re willing to sacrifice a certain degree of OPSEC (Operational Security) for the sake of growing their business model and attracting new customers. Just like the managed SMS flooding as a service concept, which we previously profiled and discussed, there’s yet another tactic in use by cybercriminals who want to assist fellow cybercriminals in their fraudulent “cash-out schemes’ – and it’s called ‘phone ring flooding as a service’.
In this post, I’ll profile a popular, publicly advertised service, which according to its Web site, has been in operation for 3 years and has had over a thousand customers.
More details:
(more…)

by Blog Staff | Feb 12, 2013 | Industry Intel, Threat Lab
Thanks to the success of multiple botnet aggregating malicious campaigns launched in the wild, cybercriminals are launching malware-infected-hosts — also known as loads — as a service type of underground market propositions, in an attempt to monetize the botnet’s infected population by selling “partitioned” access to it.
How much does it cost to buy a thousand US-based malware infected hosts? What about hosts based in the European Union? Let’s find out. In this post, I’ll profile a newly launched underground service offering access to thousands of malware-infected hosts to virtually anyone who’s willing to pay the price.
More details:
(more…)

by Blog Staff | Feb 7, 2013 | Industry Intel, Threat Lab
Need a good reason not to connect to the public Web with your phone? Wonder where all that SMS spam is coming from? Keep reading.
Mobile phone spammers have recently released a new version of a well known phone number harvesting tool, whose main objective is to crawl the public Web and index mobile phone numbers, which will later be used for various malicious and fraudulent purposes.
More details:
(more…)

by Blog Staff | Feb 6, 2013 | Industry Intel, Threat Lab
What are cybercrime-facilitating programmers up to when they’re not busy fulfilling custom orders? Releasing DIY (do-it-yourself) user-friendly tools allowing anyone an easy entry into the world of cybercrime, and securing their revenue streams thanks to the active advertisements of these tools across closed cybercrime-friendly Web communities.
In this post, I’ll profile a recently advertised DIY HTTP-based botnet tool, that allows virtually anyone to operate their own botnet.
More details:
(more…)

by Blog Staff | Feb 5, 2013 | Industry Intel, Threat Lab
by Armando Orozco
 Recently, two applications designed with malicious intent were discovered within the Google Play application store. The apps were built with a façade of being utility cleaners designed to help optimize Android-powered phones, but in reality, both apps had code built in designed to copy private files, including photos, and submit them to remote servers.
Recently, two applications designed with malicious intent were discovered within the Google Play application store. The apps were built with a façade of being utility cleaners designed to help optimize Android-powered phones, but in reality, both apps had code built in designed to copy private files, including photos, and submit them to remote servers.
The applications, named SuperClean and DroidClean, did not stop there. Researchers also found that the malware was able to AutoRun on Windows PC devices when the phones were paired, and infect the main computer. The malware was designed to record audio through the computer’s microphone.
AutoRun has often been used as a method of infection, and Microsoft has since sent a security fix out to Windows XP/Vista/7 in order to disable the exploitable element. In some cases, however, the feature might have been re-enabled by the user for convenience or never changed through a backlog of updates.
An application such as this has not been seen in the past, and is showing the creative methods through which malware coders are attempting to break through a computer’s security. With the Android device acting as a Trojan horse for the infection, malicious code has the potential of bypassing established security parameters that typically keep endpoint users safe within their network.
While Webroot has classified the malicious apps, which have been removed from Google Play’s market, it goes to show that protective steps are necessary on all levels of devices to avoid an infection. Below, we will highlight the steps you can take to help stay protected from attacks like these.
Android Devices:
- Ensure the latest version of Webroot SecureAnywhere Mobile is installed from the official Google Play Android app store.
Webroot SecureAnywhere (PC users):
- Ensure USB shield is enabled (on by default)
- Steps: Open Webroot > Select PC Security Tab > Select Shields > Slide USB Shield to on (green)
- Advanced users can modify USB heuristic settings:
- Steps: Open Webroot > Select PC Security Tab > Select Scan > Select Change Scan Settings > Select Heuristics > Select USB > Select desired protection settings
For all users, we recommend ensuring that AutoRun is disabled on your computer. Even though Microsoft rolled out updates to disable, it is possible it could be enabled. Finally, always ensure you scan USB and other connected devices for malware before storing data or using on other PCs.
For more information and to keep up with the conversation, head to our community: http://bit.ly/11RKiFa
Source: SecureList http://www.securelist.com/en/blog/805/Mobile_attacks

by Blog Staff | Feb 5, 2013 | Industry Intel, Threat Lab
Kindle owners, watch what you click on!
Cybercriminals are currently attempting to trick Kindle owners into thinking that they’ve received a receipt from an E-book purchase from Amazon.com. In reality, when users click on any of the links found in the malicious emails, they’re automatically exposed to the client-side exploits served by the Black Hole Exploit Kit.
More details:
(more…)

by Blog Staff | Feb 4, 2013 | Industry Intel, Threat Lab
On a daily basis, we intercept hundreds of thousands of fraudulent or malicious emails whose purpose is to either infect users with malicious software or turn them into victims of fraudulent schemes. About 99% of these campaigns rely on social engineering tactics, and in the cases where they don’t include direct links to the actual malware, they direct users to the market leading Black Hole Exploit Kit.
In terms of volume and persistence, throughout January, 2013, a single malicious campaign impersonating FedEx topped our metrics data. What’s so special about this campaign? It’s the fact that the digital fingerprint of one of the most recently introduced malware variants used in the campaign corresponds to the digital fingerprint of a malware-serving campaign that we’ve already profiled, indicating that they’ve been launched by the same cybercriminal/gang of cybercriminals.
Sample screenshot of the spamvertised email:
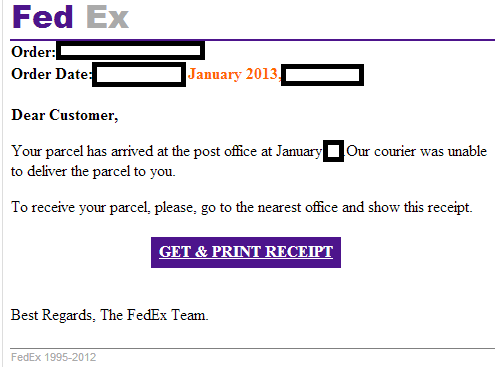
Sample spamvertised compromised URLs part of the campaign:
hxxp://relax-legend.ba/ZXSZUSBLZG.php?receipt
hxxp://stylephone.co.il/misc/teasers.php?receipt
hxxp://voguepay.com/FEZDVUUCLG.php?receipt=
hxxp://sunrisemedya.com/HAEJMKGUMT.php?receipt
hxxp://sunseekerownersclub.com/OOLZRZQTIW.php?receipt
hxxp://selimi-fugenabdichtungen.de/IYSZJVVIRA.php?receipt
hxxp://sunseekerownersclub.com/OOLZRZQTIW.php?receipt
hxxp://www.cursillodeorientacion.com/OLKIHLKYSB.php?receipt
hxxp://www.diocesebatroun.org/UEKFWHOJPF.php?receipt
hxxp://suarevista.com.br/QGQRXAOJLV.php?receipt
hxxp://fundloan.info/AYKQRUYOSL.php?receipt
hxxp://secretmobilemoneyprofits.com/SCTQOFXHVC.php?php=receipt
hxxp://www.matwigley.co.uk/SOJAJDTLAX.php?php=receipt
hxxp://rossiangelo.it/ALAGZUCWHV.php?receipt
hxxp://tqm.com.ua/misc/teasers.php?receipt
hxxp://metalphotosplus.com/PAUDSPBBXE.php?receipt
hxxp://businesscoaching24.com/BWMIZNPQAT.php?receipt
hxxp://www.bsf.org.pk/misc/teasers.php?get_receipt
hxxp://ferz.kiev.ua/misc/teasers.php?get_receipt
Detection rate for the malware variants distributed over the past 24 hours:
MD5: 980ffe6cee6ad5a197fbebdeeac9df57 – detected by 31 out of 46 antivirus scanners as Trojan-Downloader.Win32.Kuluoz.amg
MD5: bf061265407ea1f7c21fbf5f545c4c2b – detected by 6 out of 46 antivirus scanners as PAK_Generic.001
MD5: 6bb823d87f99da067e284935ca3a8b14 – detected by 36 out of 46 antivirus scanners as TrojanDownloader:Win32/Kuluoz.B
MD5: 75db84cfb0e1932282433cdb113fb689 – detected by 29 out of 46 antivirus scanners as TrojanDownloader:Win32/Kuluoz.B
Deja vu! This is the same MD5: 75db84cfb0e1932282433cdb113fb689 that we profiled in the “Fake Booking.com ‘Credit Card was not Accepted’ themed emails lead to malware” analysis, indicating a (thankfully) low QA (Quality Assurance) applied on behalf of the cybercriminals launching these campaigns.
The campaign is ongoing, so watch what you click on! Webroot SecureAnywhere users are proactively protected from these threats with our comprehensive internet security solution.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.

by Blog Staff | Feb 1, 2013 | Industry Intel, Threat Lab
Cybercriminals are mass mailing tens of thousands of emails, impersonating Booking.com, in an attempt to trick its users into thinking that their credit card was not accepted. Users are then urged to click on a fake “Print Booking Details” link, which leads them to the malware used in the campaign.
More details:
(more…)








 Recently, two applications designed with malicious intent were discovered within the Google Play application store. The apps were built with a façade of being utility cleaners designed to help optimize Android-powered phones, but in reality, both apps had code built in designed to copy private files, including photos, and submit them to remote servers.
Recently, two applications designed with malicious intent were discovered within the Google Play application store. The apps were built with a façade of being utility cleaners designed to help optimize Android-powered phones, but in reality, both apps had code built in designed to copy private files, including photos, and submit them to remote servers.