Among the most common misconceptions regarding the exploitation (hacking) of Web sites, is that no one would exclusively target *your* Web site, given that the there are so many high profile Web sites to hack into. In reality though, thanks to the public/commercial availability of tools relying on the exploitation of remote Web application vulnerabilities, the insecurely configured Web sites/forums/blogs, as well as the millions of malware-infected hosts internationally, virtually every Web site that’s online automatically becomes a potential target. They also act as a driving force the ongoing data mining to accounting data to be later on added to some of the market leading malicious iFrame embedding platforms.
Let’s take a look at a DIY (do it yourself) type of mass Web site hacking tool, to showcase just how easy it is to efficiently compromise tens of thousands of Web sites that have been indexed by the World’s most popular search engine.
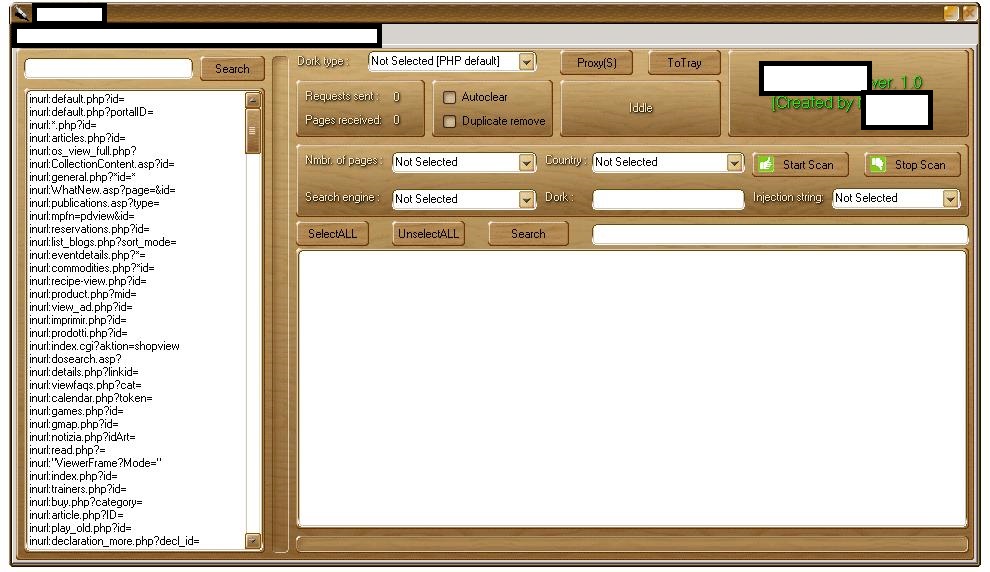
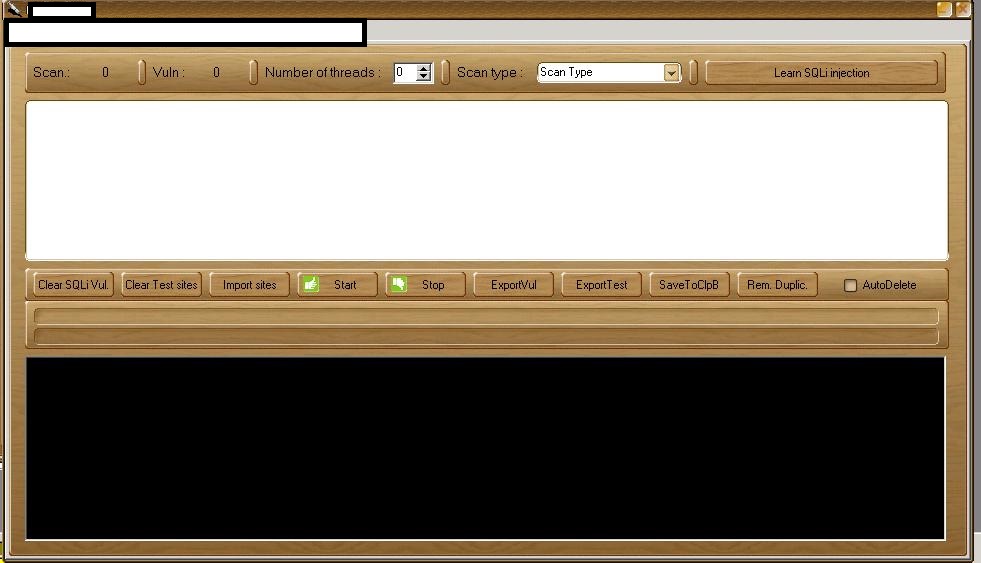
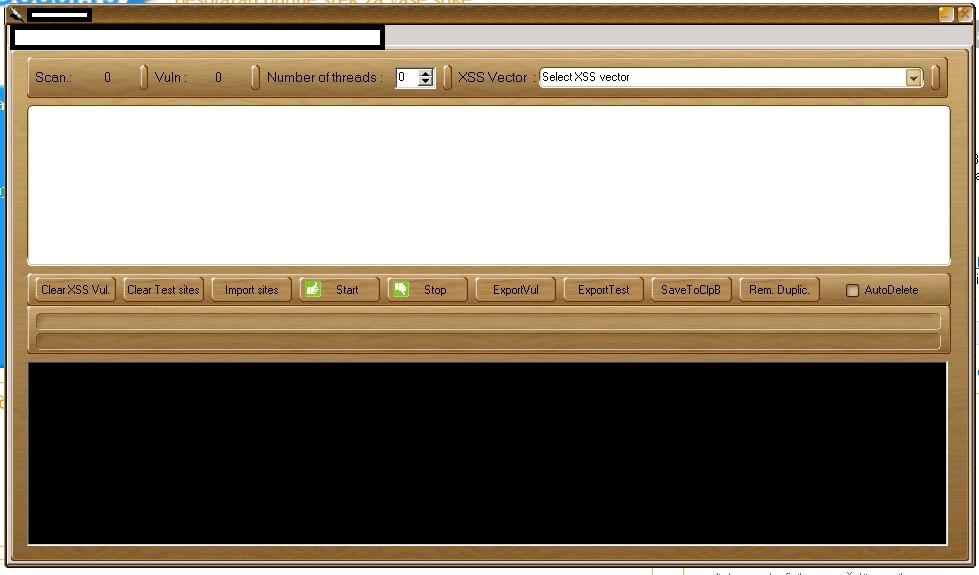
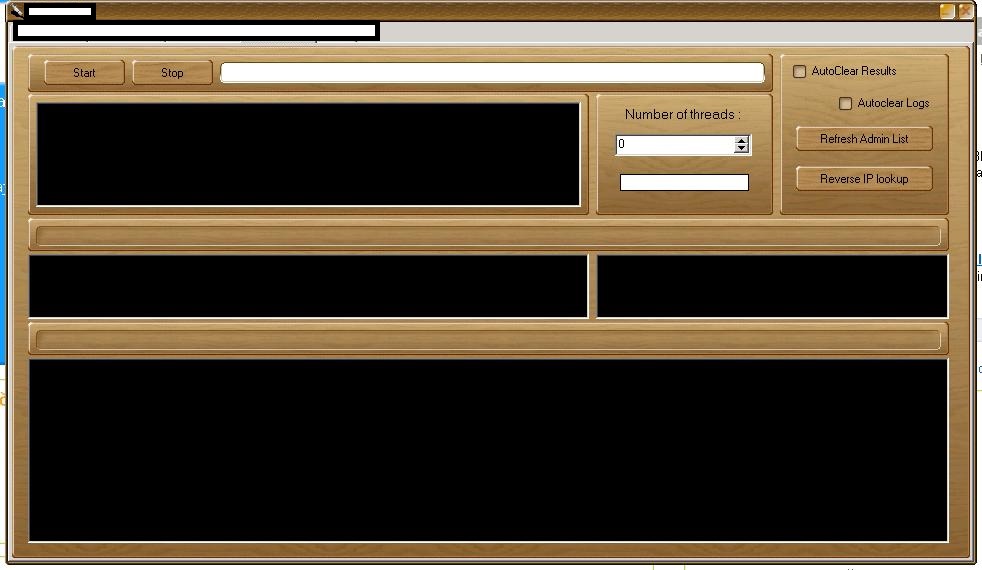
Sample screenshots of the DIY mass Web site hacking/SQL injecting tool based on the Google Dorks concept:
The proxy (compromised malware infected hosts) supporting tool has been purposely designed to allow automatic mass Web sites reconnaissance for the purpose of launching SQL injection attacks against those Web sites that are vulnerable to this common flaw. Once a compromise takes place, the attacker is in a perfect position to inject malicious scripts on the affected sites, potentially exposing their users to malicious client-side exploits serving attacks. Moreover, as we’ve seen, the same approach can be used in a combination with privilege escalation tactics that could eventually “convert” the compromised host as part of an anonymous, cybercrime-friendly proxy network, as well act as a hosting provider for related malicious of fraudulent content like malware or phishing pages. With the list of opportunities a cybercriminal could capitalize on being proportional with their degree of maliciousness or plain simple greed, Web site owners are advised to periodically monitor their site’s reputation by taking advantage of managed Web application vulnerabilities scanning services, or through Google’s SafeBrowsing.
We expect to continue observing such DIY efficiency-oriented underground market releases, with the logical transformation of DIY type of products, to actual managed services launched primarily by novice cybercriminals, either enjoying a lack of market transparency through biased exclusiveness of their proposition, or through propositions aimed at novice cybercriminals who wouldn’t have access to such tools.







how can i download this program?
please e-mail me,,,,
magnet:?xt=urn:btih:D3261FEACD4911DF5D357590BD8522BB86611E68&dn=havij+advanced+sql+injection+1+152&tr=udp%3A%2F%2Ftracker.publicbt.com%2Fannounce&tr=udp%3A%2F%2Fopen.demonii.com%3A1337