Driven by the never ending supply of newly released DIY (do it yourself) underground market releases, in combination with the systematically rebooted life cycles of releases currently in circulation, cybercriminals continue actively developing new cybercrime-friendly malware generating/botnet building applications. Motivated by the desire to further continue the monetization of this ever-green market segment, a key driving force behind the consequential rise of E-shops offering access to compromised accounting data like those we’ve extensively profiled at Webroot’s Threat Blog in the past, these cybercriminals continue to ‘innovate’ and reboot the life cycles of known releases through the systematic and persistent introduction of new features.
We’ve recently spotted a newly released, commercially available Web-based DDoS/Passwords stealing-capable DIY type of botnet generating tool, whose general availability is prone to empower potential cybercriminals with DDoS attack capabilities, as well as an efficient platform for the mass harvesting of accounting data, both of which will be inevitably monetized through the usual, now standardized monetization channels. Let’s take a peek inside the tool’s command and control interface, and discuss its key differentiation features in the broader context of their applicability in the overall threat landscape.
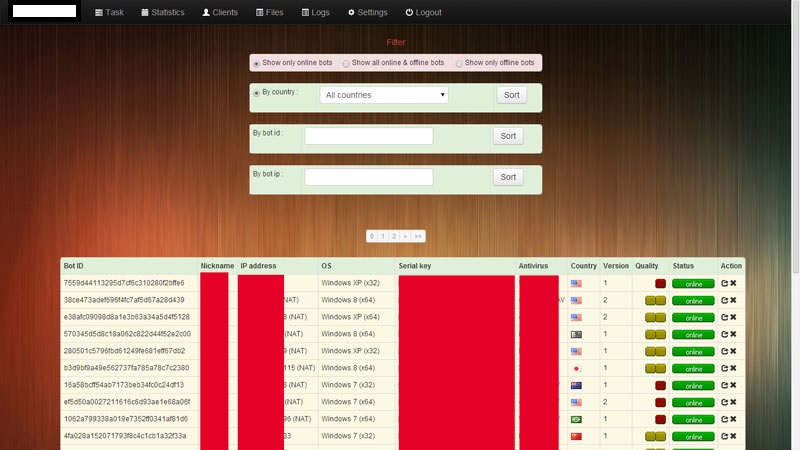
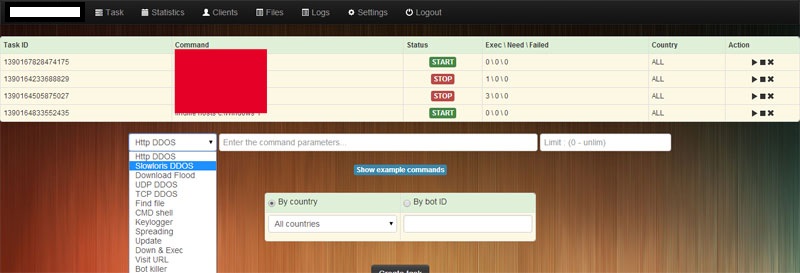
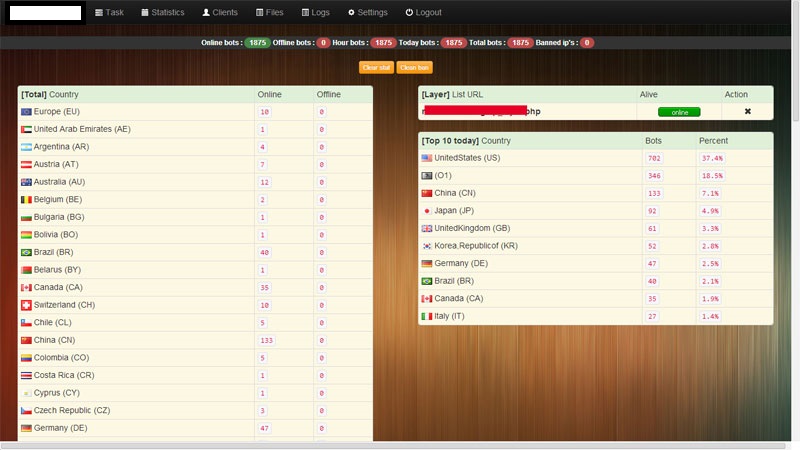
Sample screenshots of the Web-based command and control admin interface, detailing the key features of the malware/botnet generating tool:
Types of DDoS attack modes supported:
– HTTP
– Slowloris
– Download
– TCP flood
– UDP flood
Key differentiation features:
– Multi-lingual keylogging capabilities
– Command shell
– File extension based file stealing capabilities
– Loader capabilities
– USB/Archive spreading
– Competing bots killer
– Anti VMWare
– Detection of process monitoring applications
– Bot protection features
Based on the tool’s description, the average size of the binary is 50kb and works on all versions of Windows from XP to 8.1 (x32/64). The price of the full package, including support for unlimited domains, is $250 and $10 for each rebuild, $20 for updates. The price of the actual builder is currently set at $650, with WebMoney as the primary accepted payment method. The commercial availability of these DIY Web-based malware/botnet generating tools is a great example of a cyclical pattern, with the developers periodically introducing new releases on the underground marketplace in an attempt to gain market share through basic branding concepts. Although the proliferation of these “me too” malware/botnet releases lacking key differentiation factors doesn’t necessarily translate into malicious ‘innovation’, their introduction to the underground marketplace automatically generates revenue for the developers, whose releases also gain market share that, in the long term, is proportional to the persistence and sophistication of the features newly introduced by the vendor. In combination with the commercial availability of DIY malware crypting services, and the ubiquitous for the cybercrime ecosystem bulletproof hosting providers, these DIY malware/botnet generating tools represent a key driving force behind the proliferation of new malware families internationally, successfully undermining signature based antivirus scanning.
We’ll continue monitoring the development of the tool.