Regular readers of Webroot’s Threat Blog are familiar with our “A Peek Inside a Boutique Cybercrime-Friendly E-shop” series, originally started in 2012, highlighting the trend emerging at the time of boutique based E-shops selling access to compromised/hacked accounts. Popping up on our radars on systematic basis, this maturing market segment is already entering in a new life cycle stage in early 2014. The current stage is the direct result of the ongoing efficiency-oriented mentality applied by cybercriminals over the years in the face of the active implementation of tactics such as, for instance, templatization, ultimately leading to standardization of key cybercrime ecosystem processes, resulting in improved return on investment/stolen assets liquidity for their fraudulent operations.
Among the key enablers for the emergence of the market segment for compromised/hacked accounting data is the general and commercial availability of DIY (do it yourself) malware generating/botnet building tools, empowering novice cybercriminals with ‘know-how’ which was once only available to sophisticated attackers. The direct availability of these tools, in combination with the active data mining performed on behalf of botnet operators for the purpose of intercepting, then monetizing valuable accounting data, further strengthened the long-term potential of the market segment, resulting in what we’re currently observing as professional attempts to standardize the monetization process. Over the years, we’ve also observed the active monetization of compromised/hacked accounting data, with the cybercriminals behind these campaigns either selling access to it to prospective buyers, or directly abusing it for fraudulent/malicious purposes, further highlighting the existence of this ever-green monetization scheme.
A newly launched managed ‘compromised/hacked accounts E-shop hosting as a service’ aims to standardize this very same monetization process by providing virtually anyone wanting to achieve stolen assets liquidity for their compromised/hacked accounting data a DIY, self-service type of automatic E-shop setup service. Thanks to its features, potential cybercriminals looking for efficient ways to monetize the fraudulently obtained data can have a cybercrime-friendly E-shop live in 24 hours, with value-added services including ‘hardened servers’ and anti-DDoS protection. Let’s take a peek inside the service and find out just how easy it is for cybercriminals to monetize compromised/hacked accounting data in 2014, thanks to the ongoing standardization of the process.
Sample screenshots of the managed “compromised/hacked accounts E-shop hosting as a service”:
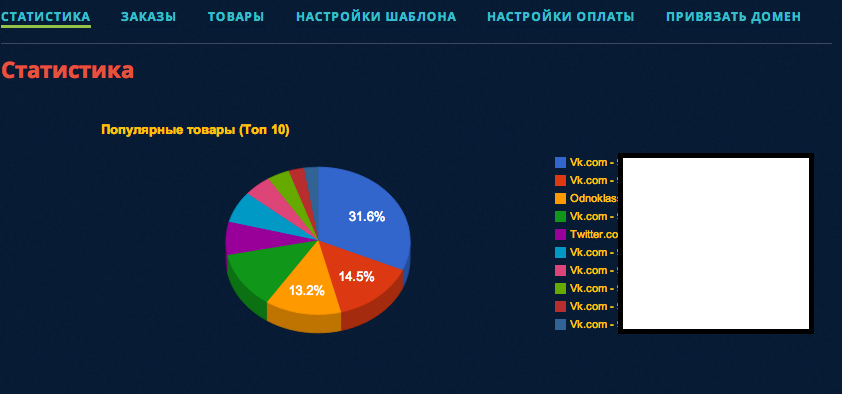
Sample metrics empowering a potential cybercriminal with statistics for the most popular assets purchased through his managed E-shop:
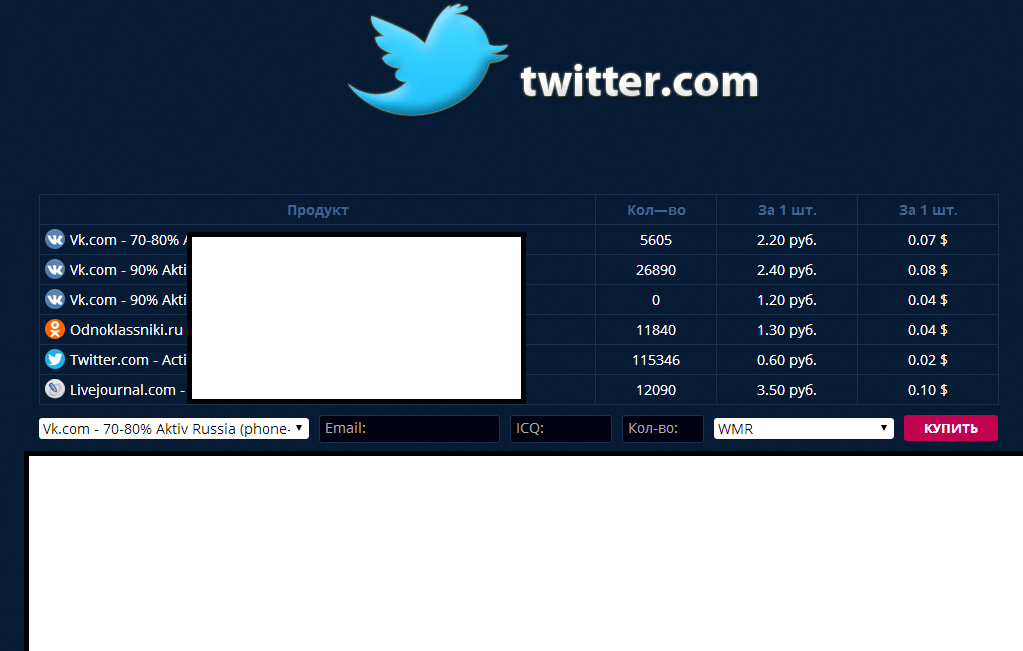
Sample screenshot of a currently active cybercrime-friendly E-shop, currently listing 115,346 active Twitter accounts offered for sale:
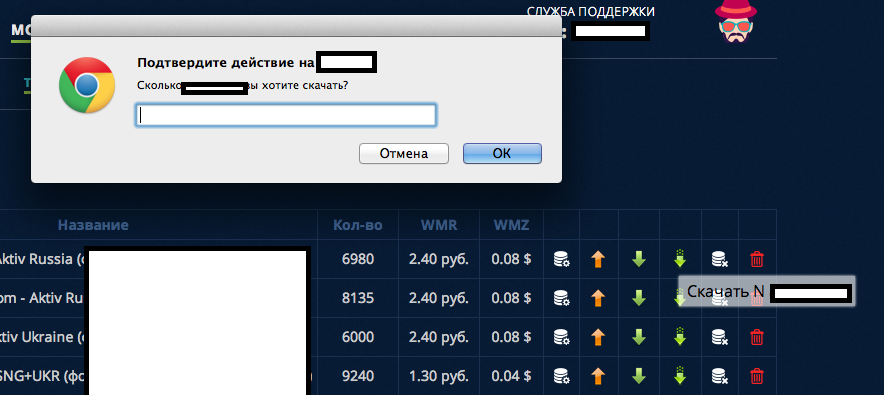
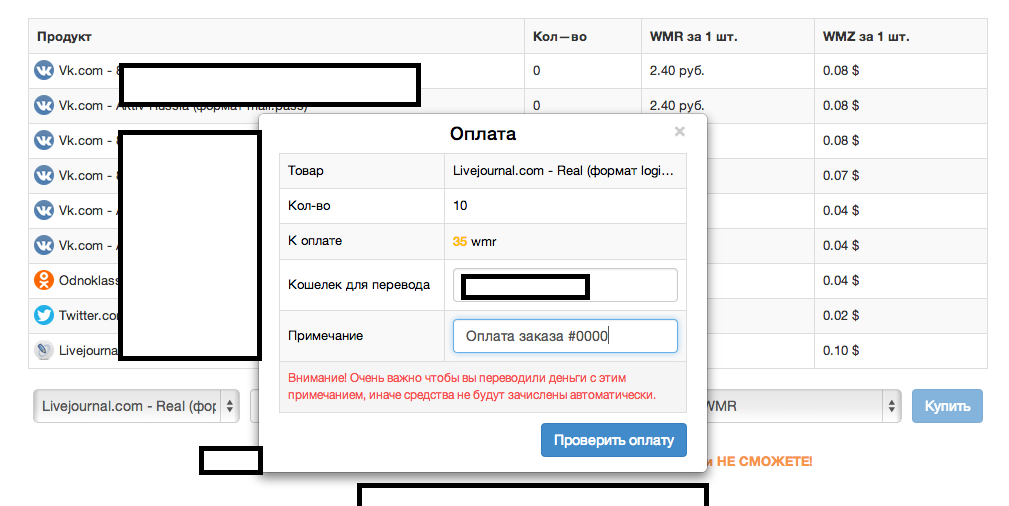
Sample screenshots of the purchasing process — the service supports Webmoney and Yandex payments — :
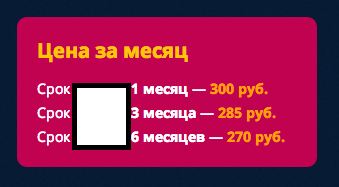
Sample screenshot of the pricing scheme:
The price for 1 month worth of managed services is 300 rubles ($8.79), 285 rubles ($8.35) for 2 months worth of managed service, and 270 rubles ($7.91) for 6 months worth of service. We expect to continue observing new market entrants, competing with these types of services, eventually leading to their inevitable reliance on the ubiquitous (for the cybercrime ecosystem) bulletproof hosting providers.
We’re constantly monitoring the market segment for compromised/hacked accounting data, and will be naturally posting updates as soon as new developments/trends emerge.







Compromised hacked accounts are really becoming a trend nowadays, that’s why it’s very important that companies offering hosting services and like should exert MORE effort in finding the right tool that they can use in protecting their client’s account and data.