Rogue vendors of Potentially Unwanted Applications (PUAs) continue tricking tens of thousands of gullible users into installing deceptive and privacy violating applications. Largely relying on ‘visual social engineering’ tactics and basic branding concepts, the majority of campaigns convincingly present users with legitimately looking ToS (Terms of Service)/EULA (End User License Agreements) which socially engineered users accept, thereby assuming the responsibility for the potential privacy-violating activities taking place on their host.
We’ve recently spotted yet another PUA campaign, relying on deceptive “Download Now” types of ads, enticing users into downloading the bogus GetMyFiles (Adware.Linkular) application, as well as the rogue SpeedUpMyPC (Win32.SpeedUpMyPC.A) PUA. Let’s profile the campaign, and provide actionable intelligence on the infrastructure behind it.
More details:
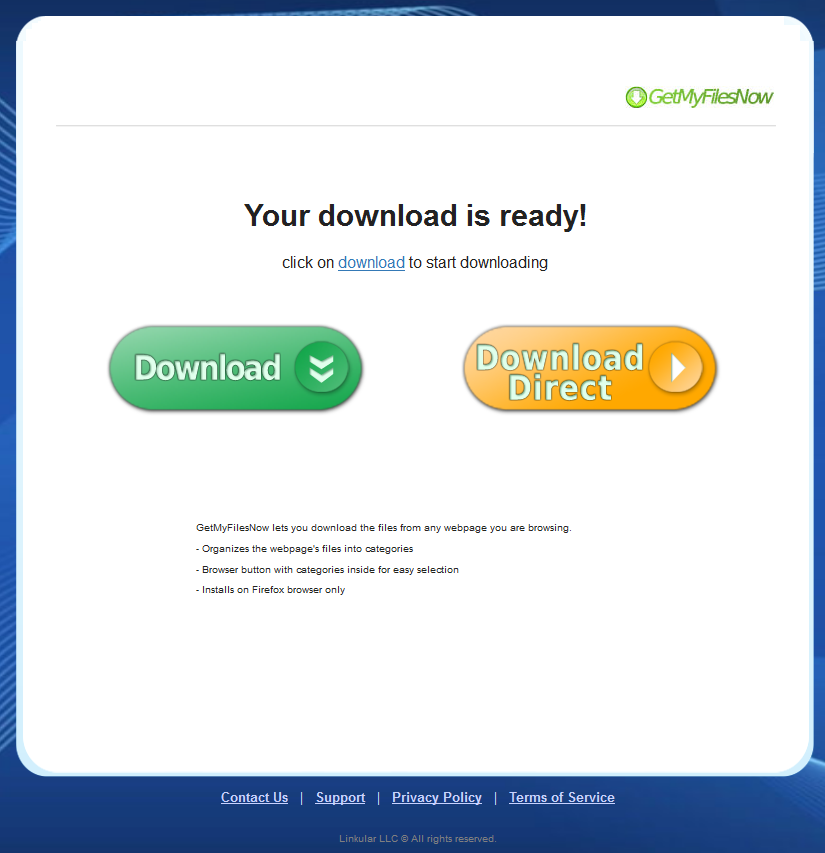
Sample screenshot of Adware.Linkular download page:
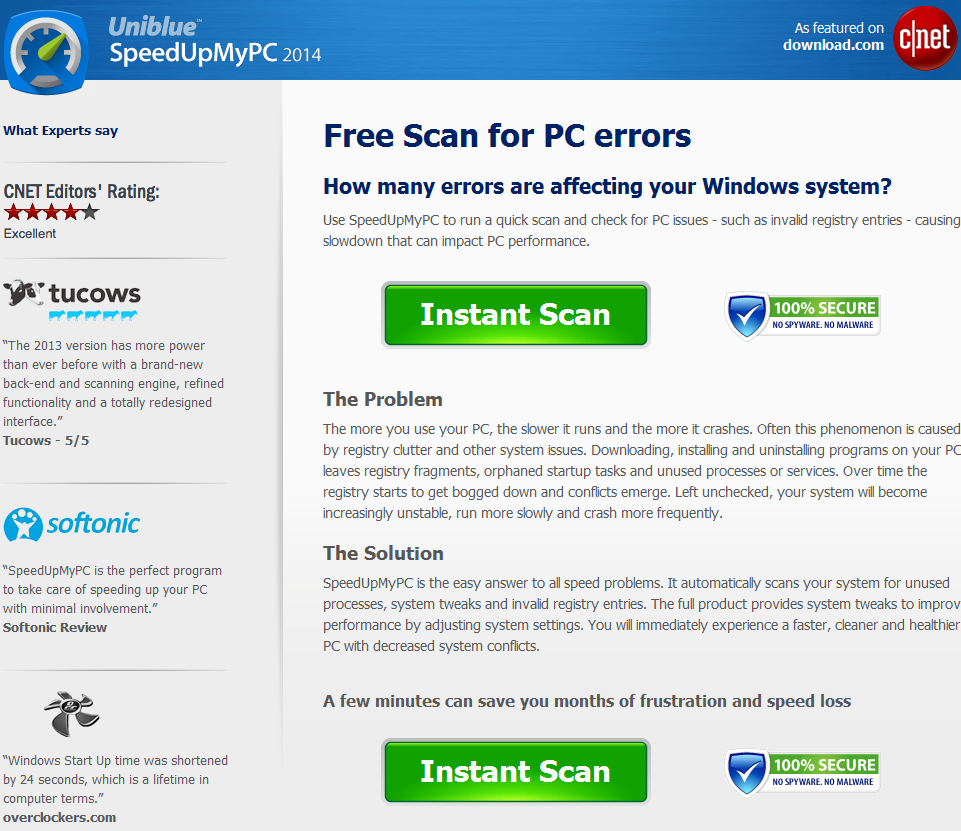
Sample screenshot of Win32.SpeedUpMyPC.A download page:
Sample redirection chain:
hxxp://ad.propellerads.com/ck.php?oaparams=2__bannerid=91608__zoneid=605__OXLCA=1__cb=__oadest=http%3A%2F%2Fwww.getmyfilesnow.info%2F%3Fpid%3D887%26context%3D%24{SUBID} -> hxxp://www.getmyfilesnow.info/?pid=887&context=4912867270
Domain name reconnaissance:
getmyfilesnow.info – 54.208.165.36
getmyfilesnow.com – 174.142.147.2
coollinks.us – 174.142.147.5
linkular.com – 208.109.216.125
Detection rate for the PUA:
MD5: 0d60941d1ec284cab2e861e05df89511 – detected by 6 out of 51 antivirus scanners as Adware.Linkular
Known to have responded to 54.208.165.36, are also the following PUA samples:
MD5: e3d7a5dda69a83a4dbffb195fe41e68f
MD5: 3f9e510e2ebe20141dbb8b61ea15e21b
MD5: 9a4dd0724d8d241d748c6b2d4658a996
MD5: 567545c3947667913853ab34bdf38e3b
MD5: 83d21d9a6a1df8a4b4beb6190dbe8266
MD5: a08a35a241b0c7aa6ed7dda7ae8bab1e
MD5: 07aae60ce06590a3b8a4e86d0b94335a
MD5: 9ab73e226bfd9393b13423490d3ed77d
MD5: 75ec259b97e67f1174820beee4cafa29
Once executed, the sample phones back to:
hxxp://107.23.152.80/api/software/?s=887&os=win32&output=1&v=2.2.2&l=1033&np=0&osv=5.1&b=ie&bv=8.0.6001.18702&c=12&cv=2.2.2.1768
Known to have been downloaded from the same IP (107.23.152.80) are also the following PUAs:
MD5: a3f2dca9cf2fbf0b6221db476b9d889c
MD5: 8f021a07e83f2b455aad969268fbcba7
MD5: 57d1a9c5de77ac85e79ad675df7753dc
Compete Inc’s Certificate Serial ID: 4A 4A CA E0 72 F8 06 5D 9C 03 E2 A2 24 09 75 B0
AdvanceMark’s Certificate Serial ID: 52 32 D1 95 19 B6 63 90 12 01 63 65 2B E1 E8 9E
Linkular LLC, 2012’s Certificate Serial ID: 27 C7 0F 80 92 79 A3
Responding to 107.23.152.80 is also the rogue mspowerpack.com, which redirects to hxxp://www.uniblue.com/cm/foxlingo/speedupmypc/banner1/download (Win32.SpeedUpMyPC.A).
Known to have been downloaded from the same IP (107.23.152.80) are also the following PUAs:
MD5: a3f2dca9cf2fbf0b6221db476b9d889c
MD5: 8f021a07e83f2b455aad969268fbcba7
MD5: 57d1a9c5de77ac85e79ad675df7753dc
Sample detection rate for the Win32.SpeedUpMyPC.A PUA:
MD5: 0a8ecb11e39db5647dcad9f0cc938c99 – detected by 3 out of 51 antivirus scanners as PUP.Optional.SpeedUpMyPC
Known to have been downloaded from uniblue.com (176.34.125.17; 46.137.104.179; 50.19.240.60; 54.217.212.162; 54.246.105.117) are also the following PUAs:
MD5: 178e9cf3c95c0867104f14310bec10cf
MD5: 573a55f36b0ff521ac5012a7ae935a04
MD5: 3ee4e5cc4ee74b45fbbba507181efaeb
MD5: 563750b3b4a7f00115c83708a7e95d39
MD5: a59e9a0ce57365bbef2042f52d622539
MD5: abc3534ef2b1086330151ef42423d208
MD5: d41ea1f04ef610566b0ad4750b2040e7
Uniblue Systems’s Certificate Serial ID: 38 B5 E3 0A ED 74 F6 CD 05 D8 F2 0F 18 E8 91 E2
Webroot SecureAnywhere users are proactively protected from these PUAs.







Tigecycline in vitro antibacterial activity against clinical strains
Abstract: Objective evaluation of tigecycline ( tetracycline antibiotic ) in vitro antibacterial activity against clinical strains . Methods broth dilution method for <a href=”http://www.medchemexpress.com/Tigecycline.html">tigecycline</a> and other 14 kinds of drugs for nearly two years in the hospital clinical specimens of 400 bacteria were isolated MIC determined by WHONET5.4 statistical software . The results showed that MIC determination : tigecycline against methicillin-resistant Staphylococcus aureus (MRSA) and Enterococcus showed good antibacterial activity in vitro test has three vancomycin-resistant enterococci (VRE), on behalf of tigecycline and linezolid -sensitive display ;<a href=”http://www.medchemexpress.com/Daptomycin.html">Daptomycin</a>, against Gram- negative bacteria Escherichia coli and ESBL-producing Klebsiella spp MIC ∞ are 1trg · mL ~, behind or below meropenem ; present study for tigecycline against Acinetobacter baumannii
The MIC. (2trg · mL a ) a minimum in all tests of antimicrobial drugs ; against Pseudomonas aeruginosa MIC ∞ value of 16p. g · mL ~.<a href=”http://www.medchemexpress.com/Tigecycline-hydrochloride.html">Tigecycline hydrochloride</a>, Conclusion tigecycline against clinical pathogens have good broad-spectrum antimicrobial activity against Pseudomonas aeruginosa Yin poor antibacterial activity.
Tigecycline (tigecycline) is a derivative of minocycline , is the first clinical application of new glycyl doxycycline antibiotics . Intravenous drug formulations, in 2005 the U.S. Food and Drug Administration (FDA) approval : tigecycline for the treatment of patients aged 18 and older infections caused by susceptible strains , indications include : complicated intra-abdominal infections ( such as complicated appendicitis ,<a href=”http://www.medchemexpress.com/Tigecycline-mesylate.html">Tigecycline mesylate</a>, burns infections, intra-abdominal abscesses, deep soft tissue infections and infected ulcers ) and complicated skin and soft tissue infections. The drug can overcome the limitations of many two main resistance mechanisms of antimicrobial drug use : efflux pumps and ribosomal protection. 1 shows a lot of old literature : the drug can be used to treat multi-drug resistant , such as MRSA, VRE, producing extended-spectrum 13 -lactamase bacterial infections caused by Enterobacteriaceae .<a href=”http://www.medchemexpress.com/Ofloxacin.html">Ofloxacin</a>
To understand the in vitro antibacterial activity of the drug , the trial of the 2009 and 2010 clinical isolates from the Ministry of Health, Beijing Hospital, 400 clinical MIC common bacteria were measured to evaluate the in vitro antibacterial activity of the drug .
Medchemexpress Can provide the above product,its website:<a href=”http://www.medchemexpress.com">www.medchemexpress.com</a>