Despite the prevalence of Web based client-side exploitation tools as the cybercrime ecosystem’s primary infection vector, in a series of blog posts, we’ve been emphasizing on the emergence of managed/hosted/DIY malicious Java applet generating tools/platforms, highlighting the existence of a growing market segment relying on ‘visual social engineering’ vectors for the purpose of tricking end users into executing malicious/rogue/fake Java applets, ultimately joining a cybercriminal’s botnet.
We’ve recently spotted yet another Web based Java drive-by generating tool, and decided to take a peek inside the malicious infrastructure supporting it.
More details:
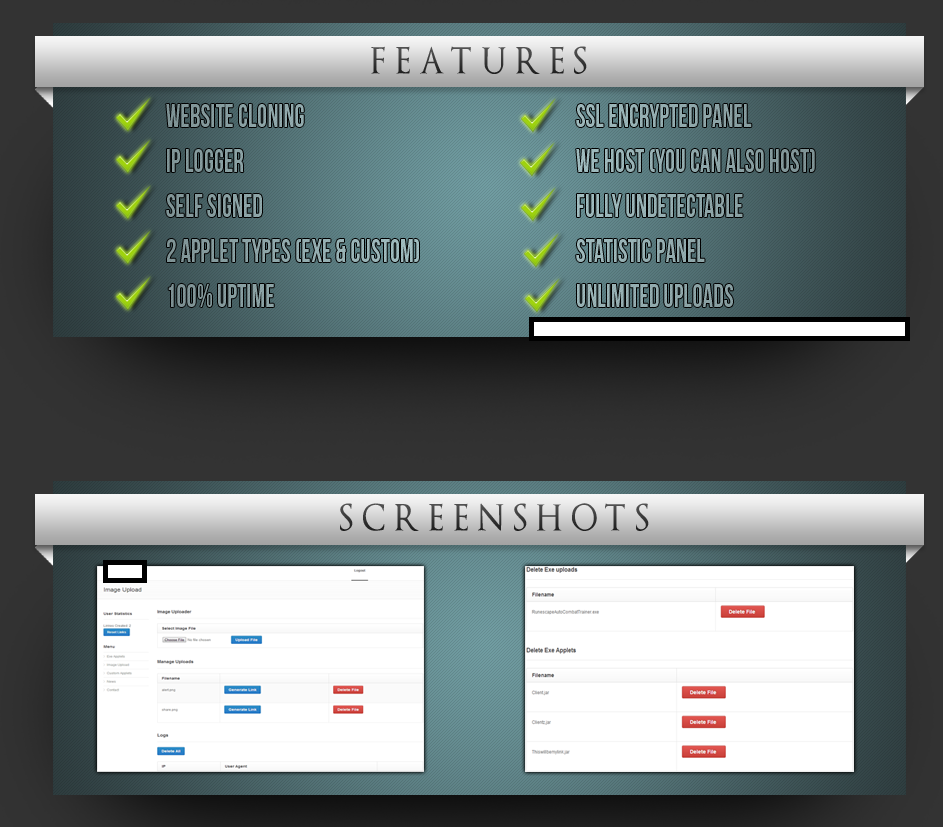
Sample screenshot of the malicious Web-based Java drive-by generating tool:
Among the tool’s key differentiation features is the ability to generate undetected applets, make identical copies of legitimate Web sites for the purpose of socially engineering end users into thinking that they’re legitimate ones, as well as the option to host a potential cybercriminal’s campaign within the vendor’s own malicious bulletproof hosting infrastructure.
Known to have been downloaded from the same IP (76.114.67.26) as the original hosting location is also the following malicious MD5: 1d03779cc7325c7b299fb2302210ec59 – detected by 41 out of 50 antivirus scanners as Trojan.Win32.Inject.fzhy.
Related malicious MD5s known to have phoned back to the last known IP (208.91.197.132), responding to the original hosting location:
MD5: ce7024013553bf577f116378e04b59c3
MD5: 96101e4c8ed7d1e909f6584e91ac468d
MD5: 6cca75f3bd1d826885084f3a242a72e9
MD5: bc4e877262fff465be4b60f46e0a6e5b
MD5: baa6c4ef642df212a869af4986db2636
MD5: aa532f11404b8ab4e11b2c0b242230b8
MD5: a9ebd2e6a762955ed6ffb3aae6379986
MD5: 08505bc34fb00a34f6c7fb780bcb33d7
Once executed MD5: 96101e4c8ed7d1e909f6584e91ac468d phones back to the following C&C servers:
os.gigatagu.com (54.212.249.225)
telecharger-gratuit.com (212.83.179.20)
enableencore.com (208.91.197.132)
img.gigatagu.com (199.58.87.155)
Known to have phoned back to the same C&C server (54.212.249.225) are also the following malicious MD5s:
MD5: b6bfe14882c126d76da6d1ad140fca60
MD5: 46272b49bfc601ce67ff3a03b2c92fca
MD5: 856820a46ae73e98b1ed2911141240c4
MD5: d1c31d9cbb44c156e58b1b35459a7d53
MD5: de7b39e74301691ae2c79e796adc9785
MD5: c01d142010979b3da4463b455b627843
We’ll continue monitoring the development of the market segment, and post updates as soon as new developments take place.
Webroot SecureAnywhere users are proactively protected from these threats.