In my last blog post about a week ago, I talked about how Cryptolocker and the like are not dead and we will continue to see more of them in action. It’s a successful “business model” and I don’t see it going away anytime soon. Not even a few days after my post a new encrypting ransomware emerged. This one even targets Russians!
Presenting Critroni (aka. Onion)
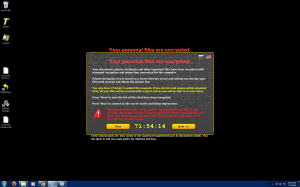
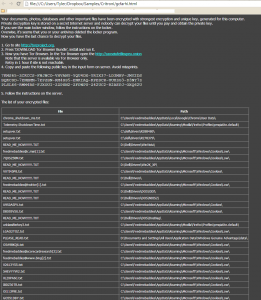
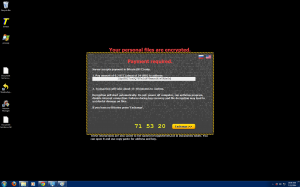
This newest edition of encrypting ransomware uses the same tactics of contemporary variants including: paying through anonymous tor, using Bitcoin as the currency, changing the background, dropping instructions in common directories on how to pay the scam. Some upgrades that are new to the encrypting ransomware scene are logging the entire directory list of files that were encrypted. They store this list in your documents folder for your convenience come decryption time (how nice of them).
The ransom amount scales with how many files are encrypted. My specific encryption only wanted “.2 Bitcoin (about 24USD)” Please note that the exchange rate displayed by the malware is extremely wrong and .2 Bitcoin is about $120.
This specific variant we analyzed does not delete the VSS (Volume Shadow Service) and you can get all your files back by using programs like Shadow Explorer. I expect that once this malware goes into widespread distribution for the US and UK that “issues” like this will get fixed and the price will rise to around .5 BTC (around $300) on average. Webroot will catch this specific variant in real time before any encryption takes place. We’re always on the look out for more, but just in case of new zero day variants – remember that with encrypting ransomware the best protection is going to be a good backup solution. This can be either through the cloud or offline external storage. Keeping it up to date is key so as not to lose productivity. Webroot has backup features built into our product that allow you to have directories constantly synced to the cloud. If you were to get infected by a zero day variant of encrypting ransomware you can just restore your files back as we save a snapshot history for each of your files up to ten previous copies.
Please note there are variations in the naming of this file, including Onion and Critroni.A.







HEY thanx bro.. i was finding fully detailed information on this ransomware and finally got it.. and thanx for the screenshots , those were helpful..
and i wanted to ask that did someone hacked into this ransomware and decrypted it like cryptolocker??
thank you for making webroot.
http://tec24x7.blogspot.in/
Hola, mi pregunta es si ya existe algún software para recuperar los archivos encriptados en ctb2.