New year; similar Scams. In 2013, I wrote an article talking about the popular Fake Microsoft Security Scams that were doing the rounds. As expected, these type of scams have continued to grow in popularity as a way for nefarious people to get money from users. Unfortunately, today these scams are more popular than ever. While the premise remains the same, some new versions of these blur the lines between what is a scam and what isn’t.
Recap
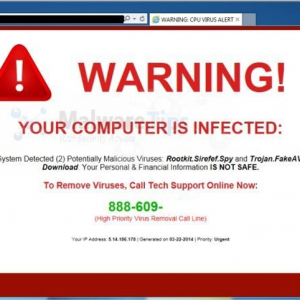
It’s worth having a quick look back at what exactly one of those aforementioned scams entails. The classic Microsoft scam goes something like this: the user gets a pop-up in their browser that tells them that they are infected and says to call a number (toll free of course) to get said infection removed. Once the user calls this number they will be directed to a website that allows the scammers (*agents*) to connect to the PC.
Figure 1: Typical Scam Message
Depending on the version the webpage (see screenshot above), the scam may try to set itself as the homepage, which means that even if the user restarts their PC, they will continue to see this warning message. This can help back up these scammers’ claims that the PC is infected.
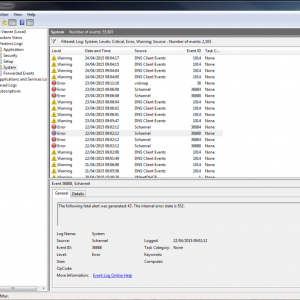
Once the scammers get connected they will show the user all the “infections” that are located in the Windows Event Logs. Windows Event logs are extremely useful to diagnose Windows issues. We would commonly use them to look for hard disk issues as any time Windows has an issue writing to a hard disk it will create a warning/error in the event logs.
After the scammers get connected, they will often install other programs that will show more errors messages. This will either be fake antivirus programs or trial versions of well-known programs that will show cookies that they will use as evidence of an infection.
In the example below, I have shown a snapshot of the warnings and errors from a test PC. It’s worth mentioning that even on a brand new PC there will be warnings or alerts in the Windows event logs.
Figure 2: Windows Event Logs
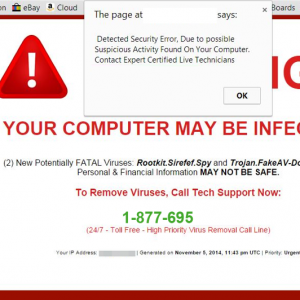
Another version of this type of scam is the version that locks the browser and uses quite intimidating language (as seen in the case below). Apparently, this user has a potentially FATAL Virus! Thankfully, we are a bit away from computer malware being able to cross the organic barrier to kill users but it’s the type of message that can catch less technical users off-guard. In certain cases the alert pop-up will keep re-appearing this locking the browser session.
Figure 3: It’s not fatal
So what’s new for 2015?
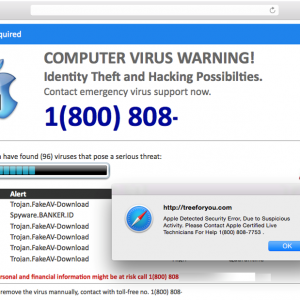
The biggest change compared to when we discussed this topic in 2013 is that these scams have now spread to other platforms, with Mac versions of these scams becoming increasingly popular. And they follow the exact same process as the PC versions. Remember that Macs do get malware and it highly advised that you install an antivirus product on your Mac.
Since these scams use a website, any device that has a browser can fall victim to this type of scam. They’re not OS dependent so if your internet enabled-toaster has a screen and a web browser it could get this type of alert! Joking aside, since it’s a browser-based scam, it’s advisable to have a backup browser installed just in case you have issues with your primary browser.
Figure 4: The Mac version
The Mac versions of this scam are pretty much identical to their PC counterparts. The only difference is that they won’t use the Windows Event Log viewer as it doesn’t exist on the Mac platform but they will use other tricks to try to fool users. In theory you could have a version that targets the Linux platform (since it’s browser based) but that platform (generally speaking) is used by more technical users and thus isn’t the target platform for these scammers.
The “Legitimate” Scam
The most disappointing of the new trends in Fake Security Scams, is the emergence of the “Legitimate” version. What do we mean by this?That well-known and respected multinational companies are using malware as a reason to charge users a fee to fix a device or service. Talk to anybody who works in IT and probably the most common reason why users suspect hardware isn’t working is due to a virus. It’s rarely (if ever) actually due to a virus, although there are of course exceptions to this. Remember the majority of malware these days is designed with the end goal of financial benefit to the person/group pushing the malware.
There is no real advantage for a scammer to stop your printer from working. The days of malware being made just to cause annoyance is long gone (although occasional cases still exist). So now let’s take a look at some of the common “legitimate” Scam types:
Your PC is part of a Botnet (an ISP favourite)
The botnet is a scam that has grown in popularity. An ISP (Internet Service Provider) will claim that a user is part of a botnet (Zeus being a favourite) and that for a flat fee they can clean out this botnet. Since the call has come from a legitimate source, the user will let their guard down and let the ISP “help” them out.
I have been connected to a number of these cases where the user has a PC that is supposedly part of a botnet. After running through the system with a fine tooth-comb and capturing network events, I was unable to find any evidence of botnet traffic. In these cases I advise the customer to contact the ISP and ask for the evidence used to determine the initial diagnosis. I have yet to hear back from any of these cases with some hard evidence of botnet traffic.
Printer (or other device) is not working because of a virus
This is by far and away the most popular type of “legitimate” scam that we encounter. A user is unable to get their printer working and they contact the hardware manufacturer. After going through a number of basic tests. it is determined that a virus is causing the issue and that they can remove the malware and setup the printer for a flat fee (notice the trend?).
I am picking on printers but it can be for any type of connected hardware. I have been connected to customers’ PC and have installed the printer for them after doing a full check for malware on the PC. In every case, it was just a matter of running through the steps and verifying that the device is installed.
What to do in the cases above
If you suspect that you have a virus that is causing a system issue, DO NOT give any credit card information to a 3rd party. Tell them you will contact them back, get the phone number directly from there Website (not the one they may give you over the phone). Contact Webroot and we can determine if there is a malware issue. Pretending to be from an ISP or an official company is a popular technique used by these scammers.
How to protect yourself from these scams
The tips that I discussed in 2013 are still valid. The first step is simply being aware that these scams exist!
- Microsoft will never call you telling you that your PC is infected
- Never allow strangers to connect to your PC
- Do not give any credit card info to somebody claiming to be from Microsoft
- If in doubt, shut down your PC and callWebroot
Tips to best protect yourself:
- Use a trustworthy antivirus program like Webroot Secure Anywhere
- Keep Windows updates turned on and set them to automatically update
- Use a modern secure browser like Firefox or Chrome
- Update any 3rd party plugins (Java/Adobe Reader/Flash player)
- Use an ad-blocker add-on in Firefox/Chrome
Looking Forward
I would like to think in two years’ time I won’t be writing another one of these but it’s a popular method to get money so I don’t see it vanishing any time soon. With Windows 10 fast approaching and with it being used on multiple platforms we may see these types of scams on all sorts of devices (perhaps even the Xbox one!). We have already seen CryptoLocker style apps on the Android platform and due to the popularity it’s only a matter of time before we start seeing mobile versions.
My advice would be to let people that aren’t technical know about these types of scams. The advanced user isn’t the target group for these scams so if you have less tech-saavy friends or family, let them know. Remember that as a Webroot customer, we can check your PC for malware free of charge.
Please contact us if you have any questions or issues. Click on the “Get customer Support” button or you can contact us over the phone.
Links:
- http://www.microsoft.com/security/online-privacy/msname.aspx
- https://support.apple.com/en-us/HT202225
- www.webroot.com
- www.webroot.com/us/en/support
- wordpressblog.webroot.com/2013/04/30/fake-microsoft-security-scam/







I just received a phone call from a guy named ”Nathan” , He had a strong accent. Maybe from India ?, His phone number is 408.622.0061, He pretented to be from the ”REFUND DEPT. . of Microsoft Security”, He wanted to check my personal informations to make sure I was the right person ! For this he needed to have acces to my PC.. He gave me instructions on how to do this. I told him not to call back and I shut the phone I suspect this to be a fraud. attempt. Michel from Montreal Canada.
hello there, my names madeline and I currently live with my grandmother, Marilyn.
we were on facebook playing our usual games and we had a tab open up or pop up with a message that told us weve been detected with the zeus virus, THE SCREEN WAS ALL BLUE WITH WHTE WRITING AND A VOICE OVER of a voice telling us to call a number which was 1800-018-586 for techniqual assistance. please help us clarify if our PC has actually contracted a virus. thank you so much
we are very humble for your answers
Hello,
That is an example of one of the scams we are referring to in this article. If you ever believe you are infected, please reach out to our support team for assistance.
Support Number: 1-866-612-4227
Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
I had that one too. The guy had a really annoying voice and it wouldn’t let me close out of it. I got my brother to help me and he just restarted my computer. After that it went away.
I am using Windows 10 and Microsoft Edge. I have a scam screen and tried using your recommended resolution. When I attempt the link: http://download.webroot.com/FixEdge.zip as advised, the link is not reached, thus I can’t open the zip file. Advice?
Terry, Usually restarting the PC will resolve this issue for you. We advise reaching out to our support team if you cannot get rid of this screen and we can take a look. This could also be caused by a Potentially Unwanted Application.
Hello, I was on my pc yesterday and the Microsoft scam came on, it froze my screen and a loud message kept telling me that my pc was infected, there was a number to call so I called because I believed it to be legit.. my concern is I allow this person to access my computer to supposedly run a scan on my pc, after that he said he could fix it for $149 I told him I would call him back which I never did and after like 30mins it dawned on me that it was a scam I actually disconnected wifi for a while and later on I run a full scan with my protection and there were no virus/no junk files, but my concern is are they still able to connect to my pc and do who knows what to it?? any advice on what I should do know, do they still have access to my pc? How do I find out? Your help will be greatly appreciated.
Rosie
Rosie,
It is unlikely that they can still connect to your PC. They would have to request permission from you again before being able to connect. If you use Webroot and want to be sure you can reach out to our support team for assistance. Support Number: 1-866-612-4227
Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
I have a similar virus on my computer. Can I click the “OK” button and still continue to use my computer until I can have the virus removed?
Mike,
It is unlikely that what you are experiencing is a virus, it is likely a PUA, or Potentially Unwanted Application. We would advise taking a look at https://community.webroot.com/t5/Techie-KB/How-to-Remove-Potentially-Unwanted-Applications/ta-p/40744 and if you are still experiencing issues, reach out to our support team.
Support Number: 1-866-612-4227
Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Hi, I had this happen to me, and I let them take control of my computer. They put a SuperAntispyware program onto my computer. I dont know what else they did, if they planted anything in my computer or if they can still access my system. What should I do now? I understand it was a scam, but what did they get? And is there something I need to check in my system. Thanks for the help!
Hi, Joy. I can understand your concern after letting an unknown individual into your computer. Typically they don’t do anything to harm your information or files. In my experience (coming from Technical Support), they mostly just leave a notepad document on the Desktop with their contact info, and sometimes they also leave the Remote Software they used to “assist” customers (GoToAssist, LogMeIn, etc).
If you have an active Webroot Subscription with us, keep in mind you can contact our Technical Support Team anytime at your own convenience and they can remotely check out your Computer, as sometimes having your Peace of Mind is the most important thing 🙂
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Zeus, a mesage popped up on my computer saying windows detected a sues virus and something keeps opening web pages later I get on one of my other accounts and a message pops up and says my computer has been blocked due to spam on the internet do I do?
Patrick, typically these scam messages will go away by just Restarting your Computer.
If the message still persists after that, you should try resetting your Internet Browser back to Default Settings.
http://www.howtogeek.com/171924/how-to-reset-your-web-browser-to-its-default-settings/
If that still does not work and the messages still keep persisting, please reach out to our Support Team directly and they will be able to ensure they resolve the issue for you:
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Restore Windows to earlier date works.
I got a “blue screen of death” on Thursday night saying my I P Address had been hacked and to call Microsoft tech immediately at 1-888- (I can’t remember the rest) they answered “Microsoft tech” then proceeded to explain the whole thing for me and took me to screens to a screen that looked like a Microsoft screen (I was scared and forgot to look at the https: address!) Then I let them remotely access my computer. He showed me the Zues virus and how harmful it is and they showed me a lot of stuff and including scrolling through something with my passwords and SS numbers etc. Then he said they had a company that was contracted with Microsoft and could fix it for a fee. So he transferred me to GI TECH and I questioned a lot he assured me they would give me security on this and any new computers I should buy I would just have to call them if I got a new computer. Then he said he could charge my Credit Card for 495.99. Then he came on ad said that it didn’t go through which was normal but he needed me to let them know that I was indeed making the payment. When I questioned why it was with Barclay Bank and not an American bank he said their corporate for Zipptech was in Europe and they were in WA State. Long story short they said after 1.5 hours they would send me notification when I could then use my computer. I immediately looked up the Zues virus and concluded I had been scammed. I called VISA and they said the payment had already been made and I had to contact the company and then I could file a dispute if I didn’t get satisfaction. I then closed out my card and sent the company an email. Waiting for a response. Today I started getting calls from “unknown” and then had a guy that started bulling me about not paying for the services they had given me. I said I didn’t know what he was talking about since I had been told it had already been paid by VISA. He was pretty verbally abusive with me saying I should have called them if I had questions and that I had now affected their BBB rating. Anyway. Blue Screen or not don’t trust them! Now I don’t know what to expect next.
Hello Barb,
If you read what other users have commented above, you can see that these types of messages/scams are very common. If you get a message like this, you can rest assured that you are not infected and simply experiencing a Hijacking Pop-up in your Internet Browser.
The most important thing to do whenever you receive any message on your screen like this (telling you to call a phone # or anything like that) is to NOT call the phone number. Typically these messages will go away just by simply restarting your computer. If you do call the number, they will want to remotely access your computer and show you the supposed “Zeus” virus, which is completely not real. They may also go through something called the Event Viewer on your Computer and tell you the errors mean you are being hacked. None of their claims are true, it is all complete rubbish and they’re really just going after your wallet.
If you ever get a message like this on your Computer and have trouble getting it to go away, please reach out to our Support Team directly and they would be happy to review your System to ensure everything is secure.
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Fell for this hook, line and sinker
I hope this helps someone else in this situation: was surfing and had a message that told me my computer had been infected with the zeus virus, THE SCREEN WAS ALL BLUE WITH WHTE WRITING AND A VOICE OVER of a voice telling us to call a number which was 1800-817-2065 for techniqual assistance. So, like an idiot I did. They then took control of my computer and showed me all the errors and computers trying to gain access to my information. They didn’t ask for a credit card but, asked for a check. Like an idiot, I gave them a check. It all look legit! I swear! I was even able to print out a receipt. The check was made out to Techmeds LLC, 623-207-1273. After reading all the comments here, I stopped payment on the check immediatly. Let them call me. I dare them! Needless to say I’ll be watching my checking account like a hawk and may have to close the account but, at least they, who ever they are, won’t be getting my money. By the way, the check was for $300!!
You did the right thing, Glenn 🙂
When I worked back in Tech Support for Webroot, the thing I told our callers was:
“If you get a message popping up on your screen telling you you’re infected and to call a number, just have comfort that your Computer is TOTALLY fine!”
Warm Regards,
Josh P.
Webroot Community Support
I wish I had known about this before it happened to me (yesterday). the warning message was very ominous and even included sound. I could not make it go away. (Unfortunately, I didn’t think about shutting my computer down.) In any case I spent about 40 minutes on the phone with the ‘supposed’ Microsoft technician. When he got to the point of asking me to pay $200 for a firewall, I just said to him that it sounded like a scam. He got very angry and basically told me that I was technically challenged and should take some classes. I wish I had told him to get a legitimate job. if he was such a hotshot technical guy. i turned off my computer and it seems to be working fine. I still plan to have some experts look at it just to make sure nothing bad was left behind.
Eileen, I completely understand your concern after having one of these supposed “Technicians” into your Computer. It happens every single day and our Technicians are great at not only handling it but helping educate our users to prevent any future occurrences.
You are more than welcome to reach out to our Technical Support Team directly so they can remotely check your system to help ease your conscience:
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Warm Regards,
Josh P.
Webroot Community Support
I got the dreaded blue screen today and almost fell for it. I got as far as typing in the http://www.support.me and them my gut feeling took over. I don’t have very much but what I do have is mine and I have worked hard for and I won’t let anyone else have it . Trust your feelings. If you think it’s wrong it probably is. Thank you webroot for making us aware of these scams
This just happend to me I legit thought it was real…. they told me not only was my computer 90%comprised already but our phones and other electronics can be harmed and will just shut down …they gave me an a dress to take ny computer,all our phones and our router..or an online source both cost $300 dollars..I told them well I font have the money and I have to talk it over with my hubby and they kept insisting that they can connect me to online support to save me trouble of having to explain to them…. but I told them I don’t have any money I’m a stay at home mom… well once my hubby woke from his nap and I explained what happend he automatically says it’s a scam …. my question is since I let them have remote access to the computer can they do any harm from here on in ?????
Bridgette,
I totally understand your concern after letting an unauthorized individual into your Computer.
There is very little chance of them being able to do any harm to your Computer. As long as you remove whatever software they installed to establish the remote connection (LogMeIn, GoToAssist, etc.), you have nothing to worry about.
Because we know how important your peace of mind is, one of our Support Technicians would be happy to review your System to ensure everything is 100% okay if you like. Please feel free to contact them directly at your own convenience:
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Warm Regards,
Josh P.
Webroot Community Support
This happened to me today & I gavegave control of my computer over. My concern is did he get my credit card & bank info? Did not ask for any money so what did he get?
Doni,
I totally understand your concern after letting an unauthorized individual into your Computer.
There is very little chance of them being able to do any harm to your Computer. As long as you remove whatever software they installed to establish the remote connection (LogMeIn, GoToAssist, etc.), you have nothing to worry about. Even if they did not get to the part where they ask for your Money, you must know that this is their only end goal and the only real risk you’re presented with.
Because we know how important your peace of mind is, one of our Support Technicians would be happy to review your System to ensure everything is 100% okay if you like. Please feel free to contact them directly at your own convenience:
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Warm Regards,
Josh P.
Webroot Community Support
I have webroot and it is running — yet when I opened a browser window from a link to a news article today, I got this windows error message and audio alert. How did this get through and how can I find out of my computer is compromised or not now?
Gloria, your computer is not compromised, but our Team does need to ensure we completely remediate whatever caused the audio alert to pop up on your screen.
Please contact our Support Team directly at your earliest convenience for assistance. They can also answer any questions you may have.
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Warm Regards,
Josh P.
Social Media Coordinator
on the bar @ bottom of screen the Webroot sign, which is usually green, is grey withred/white exclamation point. When hi-lighted, not clicked, it says “Webroot Secure Anywhere v9.0.12.52 – infected”. I hesitate to open it up to see what’s going on. Is it safe?
Eileen, it is completely safe to click on once a Threat has been identified. The scan will need just a few clicks in order to remove any threats identified.
Once it has completed removing the threats, it will re-scan your System to ensure no other Infections remain.
Please feel free to contact our Support Team if you have any issues or additional concerns:
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Warm Regards,
Josh P.
Social Media Coordinator
Yesterday it was Jousha from Microsoft and today it was Roy from Windows security dept. Since the ID on the phone said either unknown caller or anonymous I did not accept the call. Your instructions to hang up are a blessing. THANX
Greetings, Sheila!
So glad to hear that you’ve learned how to deal with these scumbags.
Remember: the names will always change, but their intent will never.
Thanks so much for sharing your experience with us! 🙂 Your gut will never let you down.
Warm Regards,
Josh P.
Social Media Coordinator
I Received one of theses hoaxes today after clicking on a “You wont believe what happened next” “ad’s”. I looked in the upper left hand of the browser and saw a Microsoft htp with a lock… The voice over was warning me of impending doom and ten I noticed the typical windows “X” in the right hand side of the browser. I use chrome for mac, so I knew this was bs. How ever it had all the hallmarks of everything you described In your article. It would let me close the “browser”, so I force quit the window and restarted my mac with out further issues. So, guess what happened next? NOTHING! Thanks for your service webroot… Appreciate what you’re doing.
Hi Steve,
Thanks for letting us know! We appreciate you sharing your Story so that others can know before it’s too late.
Our Support Team is always here to help as well if you have a message/window/voice that won’t go away! Our Advanced Malware Team will take down the baddies for you 🙂
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Warm Regards,
Josh P.
Social Media Coordinator
Well I wish I had had a reason to look here before tonite! I just got taken big time it seems. My screen got hijacked and I didn’t know enough to know I could just shut it off and be ok. I called the #, a 1-888 number. The screen in the background struck me as being Microsoft looking. When i callex a gal answered, had me repeat what the screen said and sent me to a tecnician who i thought was from Windows! I gave him control of my laptop! He showed me the things that were wrong with my laptop and for how long on screens that sure looked official. Showed it had been going on since Nov; but now that I think of it I had good coverage and scanned every week..nothing ever showed up. He said there were 9 intruders that were into all my accounts. I was in the phone with him for almost an hour and crying!! They wanted 350 for permanent 1 year security fix for my laptop, cell and tablet. I said I couldn’t do that in one pmt..he said they could split the e yr cost of 569 into two. AND I BOUGHT IT. With a check..one in Jan and one in Feb. I cried and he tried to make me feel better as he robbed me!!!
This co. Is Vaas Pro Inc. I’m going to stop mot on the check! AND TALK TO COPS. I can’t believe I was so gullible
I think this just happened to me! Got the pop-up with urgent message that all of my logins and passwords had been hacked and to call immediately, all with a very official-looking Microsoft page. Called the toll free number, gave the technician access to my computer, and he showed me many things which got me very concerned and frightened. It wasn’t Zeus but two others, and he showed me on Wikipedia that these were Trojan Horse viruses, and the list of red alerts. And then he offered the solution to a problem i didnt have! Now I just feel utterly stupid! At least it seems that letting them onto my computer probably didn’t hurt it?
You’re exactly right, Kimberly.
Letting them onto your Computer should not do any damage to your files or your system. If you ever come across something that seems suspicious, ALWAYS contact our Support Team first!
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Warm Regards,
Josh P.
Social Media Coordinator
I did get a pop up about the Zeus virus today which said that my hard drive would be destroyed if I turned off my computer and was advised to call an 800 number for TechZcare. They remotely came into my computer, told me they fixed the problem, charged me $120 on top of another $140 for a year for tech support, since my they told me my Vipre anti virus software would not be working for Windows 10; that Windows 10 had its own built in antivirus and that their tech support would offer protection of online banking, shopping, virus protection, malware, etc. I gave them my credit card to be charged for these services plus the code. Now I’m horribly worried about what kind of access they have to my computer, my files, my credit card, etc. Please advise me.
First of all Marilyn, I’m very sorry to hear of the experience you went through with these individuals. They use Fear as their primary weapon of choice.
That being said, so long as you have uninstalled whatever Remote Assistance Software they used (GoToAssist, LogMeIn, TeamViewer, etc.), there is absolutely no way that they can re-gain access to your Computer without going through all of the steps you had to the first time.
I’d highly suggest reaching out to our Technical Support Team so they can review your System to ensure everything checks out A-OK:
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Best Regards,
Josh P.
Social Media Coordinator
I had the pop up message happen to me tonight and yes I did call. While going through the spiel the supposed tech talked down to me and was pretty condecending I thought (just because I’m not a tech doesn’t mean I’m an idiot) then it came time to close the deal came to 149USD (I live in Canada) I said I can’t afford it right now and told them I will get a friend to fix it then I restarted my computer and everything appears to be fine. If somebody is going to try to scam someone else you would think they would have at least some customer service skills.
Unfortunately Don, your Story is very similar to similar accounts I’ve heard from many, many other Customers while I worked on our Consumer Support Team for a year.
They get very militant and vicious when you aren’t giving them exactly what they want($$$$).
Please save this contact information for our Technical Support Team so you can reach them should you ever have an issue like this in the future:
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Warm Regards,
Josh P.
Social Media Coordinator
Just got a call from someone saying he’s from Windows and to go to http://techus.ga because my computer is infected.
I mocked him and he hung up.
Be careful!!!
HI,
I am not sure if I am being scanned or not. I have been working with ALPKEY computers. I have their number save as 1-800-284-5210.When I call it does say I reached ALPKEY and someone does answer. Today they told me to no longer call that number and to instead call 888-980-6447. I am not sure what that’s all about….
Anyway, Alpkey removed my viruses whenever I get one. I supposedly had a lifetime subscription for all my devices which I paid $519.00 for. About a year after paying the fee, my computer got a virus and I contacted ALPKEY. They fixed it but said they had to charge me for the software that they needed to install. I’m afraid that this will just be a continuous cycle….I call to get something addressed and then they charge me for something. What should I do? I cannot tell if they are legit or not.
Tina, any service that operates like this is completely illegitimate.
I recommend contacting your Financial Institution and letting them know of the nature of their business. Hopefully, they will be able to stop the charges.
For the future, any threat-related inquiries or concerns should be dealt with by our Advanced Malware Removal Team directly:
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Warm Regards,
Josh P.
Social Media Coordinator
I fell for the zeus scam today and now not sure how to handle it. I cancelled credit card. These are items that it looks like were installed on my computer today and I need to know if I should get them off: Adblock Plus, Groove Music, Mail & Calendar, People and Webroot Secure Anywhere. If so, what is the best way to do it? Could there be anything else?
Hi, Cindy.
The most important things you will want to make sure are removed is any Remote Tools they used to get onto your Computer (GoToMeeting, LogMeIn, Teamviewer, etc).
Our Advanced Malware Removal Team can review your system in its entirety to ensure that nothing malicious still remains on your System:
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Warm Regards,
Josh P.
Social Media Coordinator
Hi, after reading all of the encounters above, I realized that me too fell into this scam! The popped up screen said that if I turn off my computer, I will not be able to turn it back on again!
So I followed the direction– called the number and allowed them to remotely access my computer because they sounded regetimate representing Microsoft. But when they asked for money I told them I cannot afford it– I retired. I said I will call them back when I have money. I turned off my computer. Now the problem is when I try to turn on my computer again, I cannot access it. It has a box saying that I need a code to access! They probably did it. What should I do now?
Hello Somchai,
You can try performing a System Restore to a time before they access to your Computer.
https://www.howtogeek.com/howto/windows-vista/using-windows-vista-system-restore/
If you’re unable to do that, you can reach out to our Support Team and they can see if there is anything they can do to help:
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Warm Regards,
Josh P.
Social Media Coordinator
Same happened to me yesterday, I questioned him and didn’t get to the money part. Thank God. I unplugged my PC, took it to Geek Squad to clean and set it back to original manufacturing setting. However, he had access to my PC for about 20 mins, doing what seemed like scanning. Is there a chance he could copy my files or confidential information to steal my identity later on? Or is there a chance he had all my passwords and should I change all my passwords immediately? Thank you for your service.
Changing your passwords after any sort of outside intrusion is always a good security practice, Tom.
It’s very unlikely that he would’ve copied any files from your system, they normally are solely after getting dollars out of your wallet and nothing.
Our Support Team is always here to help if you have any questions or concerns that you need to have addressed:
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send a Support Ticket: wbrt.io/eyqx
Warm Regards,
Josh P.
Social Media Coordinator
I have a feeling I may have been scammed. I responded to a pop-up “may I help you” box at a site I thought was HP to get help about my printer. The company that charged me for unwanted firewall protection was KE IT Cart. Is this a legitimate company?
Lillian, it doesn’t sound like you were dealing with a reputable company.
I recommend reaching out to our Support Team at your earliest convenience to review your system:
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Warm Regards,
Josh P.
Social Media Coordinator
I thought I was talking to someone from HP about my printer not printing. They handed me over to Sapphire Technical to solve the problem. I allowed them to access my computer (wrong decision). I was able to print while on the phone but later I was not.
I finally suspected a scam and called my bank to cancel the charge for a firewall. Is there anything else I need to do?
Hello, Steven.
These individuals do typically like to pose as a reputable company like HP or Microsoft.
Please feel free to reach out to our Support Team directly to review your system. They’ll do a clean-sweep of your machine and also address any other questions/concerns you may have.
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send a Support Ticket
Warm Regards,
Josh P.
Digital Care Coordinator
Hello Steven
Is this Fake Security Scams againt the law ?
In italy we have a company http://www.pcitaly.com that under some normal Services they get the clients with some very agressive fake scams or pop ad..
I have read your postings with interest. I have experienced a few such incidents but when I do I always shut down the computer at once. So far this has ended all the problems. But I am worried that the scammers may be upgrading their scammy softtware and one day the shutoff tactic won’t work.
I don’t want to offend you but I must say that I have some questions about _you_. How do I know you are not yourself a more sophisticated scammer? What if I call that ‘support number’ you give in every message? How can I be sure you are what you claim to be?
Dammit, I hate to be so suspicious but the Internet is a very big, very dark place inhabited by all sorts of people who aren’t who or what they claim to be. So, once again, how do I know for sure that you are to be trusted?
I completely understand taking everything with a grain of salt, Andrew.
Webroot is a Global CyberSecurity Company that takes our reputation very seriously. We strive to educate users at any opportunity to help make the Internet a safer place.
https://en.wikipedia.org/wiki/Webroot
The information I provide is the same contact information that is listed on our Official Website.
https://www.webroot.com/us/en/about/contact-us
Don’t take just my word for it, always test the waters and see for yourself. If your gut tells you otherwise, follow it.
Appreciate the conversation!
Happy Weekend,
Josh P.
Digital Care Coordinator