Cybercriminals are currently spamvertising malicious USPS-themed emails, that entice end and corporate users into clicking on malicious links found in the emails.
More details:
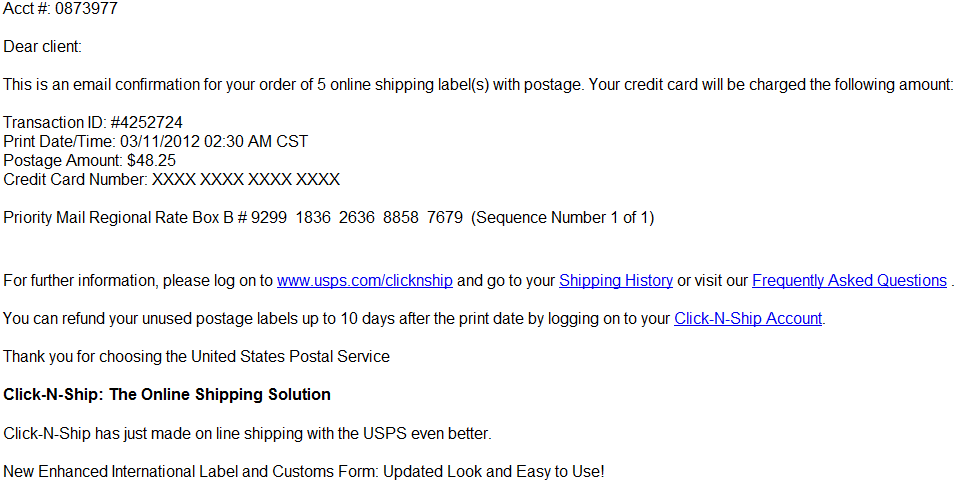
Sample subject: USPS postage labels order confirmation; Your USPS postage labels charge
Sample message: Acct #: 0873977 Dear client :This is an email confirmation for your order of 5 online shipping label(s) with postage. Your credit card will be charged the following amount: Transaction ID: #4252724Print Date/Time: 03/11/2012 02:30 AM CST Postage Amount: $48.25Credit Card Number: XXXX XXXX XXXX XXXX Priority Mail Regional Rate Box B # 9299 1836 2636 8858 7679 (Sequence Number 1 of 1) For further information, please log on to www.usps.com/clicknship and go to your Shipping History or visit our Frequently Asked Questions .You can refund your unused postage labels up to 10 days after the print date by logging on to your Click-N-Ship Account.Thank you for choosing the United States Postal Service Click-N-Ship: The Online Shipping Solution Click-N-Ship has just made on line shipping with the USPS even better.New Enhanced International Label and Customs Form: Updated Look and Easy to Use!* * * * * * * *This is a post-only message
Sample malicious URL spamvertised in the campaign: hxxp://blazewear.assetict.com/sgENCGn0/index.html
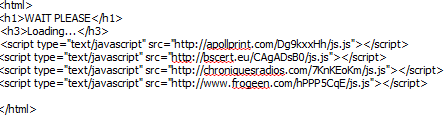
Upon clicking on the links, end and corporate users will view a “WAIT PLEASE, Loading…” page. In between, the campaign will attempt to load up to 4 different javascript files from multiple compromised URls in an attempt to serve client-side exploits and malware to users.
Structure of the client-side exploits serving process is as follows.
Malicious javascript loads from the followung URLs:
hxxp://apollprint.com/Dg9kxxHh/js.js
hxxp://bscert.eu/CAgADsB0/js.js
hxxp://chroniquesradios.com/7KnKEoKm/js.js
hxxp://frogeen.com/hPPP5CqE/js.js
Once the campaing loads the malicious javascript, the following redirections take place:
hxxp://blazewear.assetict.com/sgENCGn0/index.html
hxxp://apollprint.com/Dg9kxxHh/js.js
hxxp://jadecellular.com/showthread.php?t=73a07bcb51f4be71
hxxp://jadecellular.com/content/Qai.jar
The compromised legitimate web site participating in the campaign, has a very low detection rate.
Webroot’s security researchers will continue monitoring the spamvertised campaign, to ensure that Webroot SecureAnywhere customers are protected from this threat.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.







The javascript and jars are blackhole related QAI.jar should be detected by just about all AV now. The showthread.php is the actual exploit kit injected into jadecellular.
YOU are so right about this .there are a few people I know that got this. and the virus security 2011 was included with it.as soon as unzipped .also fedex has had a few also