Cybercriminals are currently spamvertising millions of emails, impersonating Friendster, in an attempt to trick its current and prospective users into clicking on a malicious link found in the email.
Upon clicking on the link, users are exposed to the client-side exploits served by the latest version of the Black Hole exploit kit.
More details:
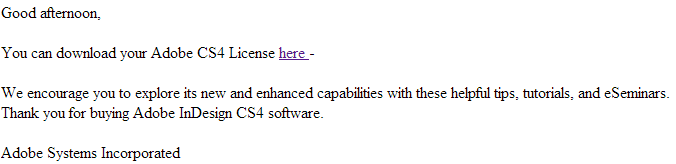
Sample screenshot of the spamvertised email:
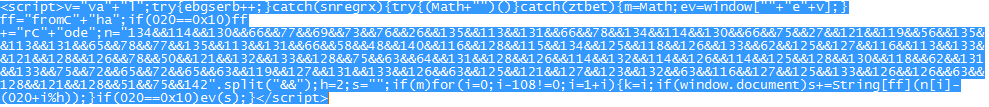
Sample screenshot of the obfuscated Java script loading the malicious iFrame:
Malicious URL: hxxp://sonatanamore.ru:8080/forum/links/column.php
Client-side exploits serving URL: hxxp://sonatanamore.ru:8080/forum/links/column.php?iqtxfe=3533020635&smr=3307093 738070736060b&grrhh=03&ndgywdt=nyurdae&aquotd=uox
Client-side exploits served: CVE-2010-0188
sonatanamore.ru used to respond to the following IPs – 70.38.31.71; 202.3.245.13; 203.80.16.81; 213.251.162.65
Responding to the same IPs are also the following malicious domains:
limonadiksec.ru
rumyniaonline.ru
denegnashete.ru
ioponeslal.ru
moskowpulkavo.ru
onlinebayunator.ru
lenindeads.ru
omahabeachs.ru
uzoshkins.ru
sectantes-x.ru
Sample detection rate for the malicious iFrame loading script: friedster.html – MD5: c444036179aa371aebf9bae3e7cc5eef – detected by 12 out of 42 antivirus scanners as Exploit.JS.Blacole; Trojan.JS.Iframe.acn
Upon successful client-side exploitation, the campaign drops MD5: 8fa93035ba01238dd7a55c378d1c2e40 on the affected host, currently detected by 24 out of 43 antivirus scanners as Trojan-Ransom.Win32.PornoAsset.aeuz; Worm:Win32/Cridex.E
Upon execution, the sample phones back to 95.142.167.193:8080/mx/5/A/in.
What’s also worth pointing out in regard to this campaign is the fact that, during the time the Friendster-themed campaign was spamvertised, another campaign was also launched with identical MD5 for the javascript obfuscation script.
Sample screenshot of the spamvertised campaign:
Clearly, both campaigns have been launched by the same cybercriminal/gang of cybercriminals.
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.