We’ve recently intercepted a localized — to Bulgarian — malware campaign, that’s propagating through Facebook Wall posts. Basically, a malware-infected user would unknowingly post a link+enticing message, in this case “Check it out!“, on their friend’s Walls, in an attempt to abuse their trusted relationship and provoke them to click on the malicious link. Once users click on the link, they’re exposed to the malicious software.
More details:
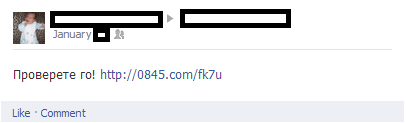
Sample screenshot of the propagation in action:
Sample spamvertised URL appearing on Facebook users’ Walls:
hxxp://0845.com/fk7u
Sample redirection chain:
hxxp://0845.com/fk7u -> hxxp://connectiveinnovations.com/mandolin.html?excavator=kmlumm -> hxxp://91.218.38.245/imagedl11.php
Sample detection rates for the malicious executables participating in the campaign:
hxxp://91.218.38.245/imagedl11.php – MD5: 1ad434025cd1fb681597db80447290e4 – detected by 23 out of 46 antivirus scanners as Backdoor:Win32/Tofsee.F
hxxp://91.218.38.245/imagedl11.php – MD5: 95a29c9652accb0b66036f026b6c85da – detected by 16 out of 46 antivirus scanners as Trojan-Dropper.Win32.Dorifel.zek
hxxp://91.218.38.245/11c.exe – MD5: 6807409c44a4a9c83ce67abc3d5fe982 – detected by 30 out of 46 antivirus scanners as Trojan-Dropper.Win32.Dorifel.ypu
hxxp://91.218.38.245/10c.exe – MD5: c032551a9c917af3a33dd48dfb68807c – detected by 37 out of 46 antivirus scanners as Trojan-Ransom.Win32.Gimemo.atzi
hxxp://91.218.38.245/4c.exe – MD5: 11bc0e87a3a71ed39d070eb8c8c66368 – detected by 22 out of 45 antivirus scanners as Backdoor:Win32/Tofsee.F
hxxp://91.218.38.245/2c.exe – MD5: 851429df461b2f5787cdfbdc0e525bfc – detected by 6 out of 46 antivirus scanners as Artemis!851429DF461B
hxxp://91.218.38.245/6c.exe – MD5: cd7c00403703ff2f97c92673464a9749 – detected by 35 out of 46 antivirus scanners as Trojan-Ransom.Win32.Gimemo.atzi
hxxp://91.218.38.245/9c.exe – MD5: ff7a64bee4dda13251988f77e2bccfc4 – detected by 38 out of 46 antivirus scanners as Trojan-Ransom.Win32.Gimemo.atzi
hxxp://91.218.38.245/8c.exe – MD5: 2d4c5b95321c5a9051874cee9c9e9cdc – detected by 38 out of 46 antivirus scanners as Trojan-Ransom.Win32.Gimemo.atzi
Responding to this IP (91.218.38.245, AS197145 Infium Ltd.) are also the following malicious/fraudulent domains:
fblegit.tf
wlvfzs.swansdown.co.uk
darai.info
aqfswt.darai.info
ruination.info
cbrjy.ruination.info
wwmgsn.fblegit.yt
ghgxsbsd.funche.eu
lwvk.funche.eu
annafi.eu
pyju.chickon.eu
kntg.dianabo.eu
forgather.eu
proconsul.biz
technical.name
fblegit.tf
wlvfzs.swansdown.co.uk
darai.info
aqfswt.darai.info
ploughman.info
ruination.info
cbrjy.ruination.info
otplh.fblegit.yt
wwmgsn.fblegit.yt
ghgxsbsd.funche.eu
lwvk.funche.eu
pyju.chickon.eu
kntg.dianabo.eu
housefather.eu
forgather.eu
seductive.proconsul.biz
metricize.net
overcapitalise.com
ploughman.info
proconsul.biz
roodscreen.net
ruination.info
technical.name
Sample behavioral analysis for the associated MD5s:
MD5: 11bc0e87a3a71ed39d070eb8c8c66368 creates the C:Documents and SettingsAdministratortbdv.exe and C:DOCUME~1ADMINI~1LOCALS~1Temp1014.bat files on the affected hosts. It then phones back to 91.218.38.245.
MD5: 851429df461b2f5787cdfbdc0e525bfc creates the C:Documents and SettingsAdministratorhhqpbnac.exe and the C:DOCUME~1ADMINI~1LOCALS~1Temp4628.bat files on the affected hosts. It then phones back to 91.218.38.245
MD5: 2d4c5b95321c5a9051874cee9c9e9cdc creates the following file on the affected systems: %UserProfile%yzrpofko.exe. It also modifies the registry: [HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun] MSConfig = “”%UserProfile%yzrpofko.exe”, and phones back to 185.4.227.76:443.
MD5: cd7c00403703ff2f97c92673464a9749 creates the following file on the affected hosts: %UserProfile%btewpzqa.exe. It also modifies the Registry: [HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun] MSConfig = “”%UserProfile%btewpzqa.exe”, and phones back to 185.4.227.76:443.
MD5: c032551a9c917af3a33dd48dfb68807c creates the following file on the affected hosts: %UserProfile%asvkgzso.exe. It also modifies the Registry: [HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun] MSConfig = “”%UserProfile%asvkgzso.exe”, and phones back to 185.4.227.76:443
MD5: ff7a64bee4dda13251988f77e2bccfc4 creates the following file on the affected host: %UserProfile%tpatewvi.exe. It also modifies the Registry: [HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun] MSConfig = “”%UserProfile%tpatewvi.exe” and phones back to 185.4.227.76:443.
More MD5s are known to have phoned back to 91.218.38.245:
MD5: 20057f1155515dd3a37afde0b459b2cf
MD5: 665419c0e458883122a790f260115ada
MD5: 1ea373c41eabd0ad3787039dd0927525
MD5: f3472ec713d3ab2e255091194e4dccaa
MD5: 4d54a2c022dad057f8e44701d52fec6b
MD5: 6807409c44a4a9c83ce67abc3d5fe982
As well as related MD5s phoning back to 185.4.227.76:
MD5: 6b1e671746373a5d95e55d17edec5623
MD5: 377c2e63ff3fd6f5fdd93ff27c8216fe
MD5: 2D4C5B95321C5A9051874CEE9C9E9CDC
MD5: 3f9df3fd39778b1a856dedebf8f39654
MD5: 82e2672c2ca1b3200d234c6c419fc83a
MD5: 796967255c8b99640d281e89e3ffe673
MD5: bc1883b07b47423bd30645e54db4775c
MD5: e6f081d2c5a3608fad9b2294f1cb6762
What’s special about the second C&C phone back IP (185.4.227.76) is that it was used in another Facebook themed malware campaign back in December, 2012, indicating that this cybercriminal/group of cybercriminals are actively impersonating Facebook Inc. for malicious and fraudulent purposes.
If you catch a Facebook impersonating email in the wild, please forward it to phish@fb.com to notify Facebook of the attack.
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.