By Dancho Danchev
Cybercriminals are currently mass mailing tens of thousands malicious ‘CNN Breaking News’ themed emails, in an attempt to trick users into clicking on the exploit-serving and malware-dropping links found within. Once users click on any of the links found in the bogus emails, they’re automatically exposed to the client-side exploits served by the Black Hole Exploit Kit.
More details:
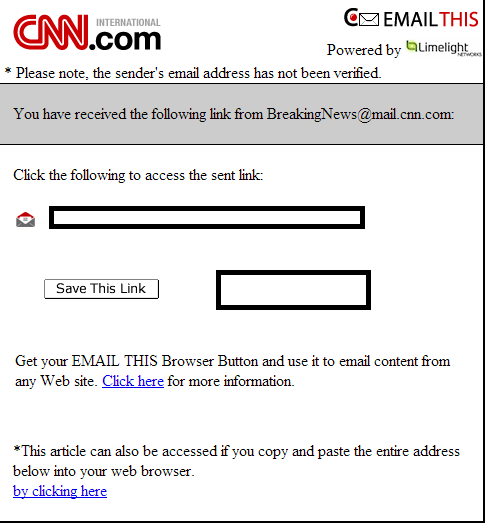
Sample screenshot of the spamvertised email:
Sample compromised URLs used in the campaign:
hxxp://320315.ru/popeabuse.html
hxxp://bigznakomstva.ru/popeabuse.html
hxxp://cescasworld.com/popeabuse.html
hxxp://c-s-x.ru/popeabuse.html
hxxp://create-serv.ru/popeabuse.html
hxxp://adobeart.ru/popeabuse.html
hxxp://cescasworld.com/popeabuse.html
hxxp://bloodygames.ru/popeabuse.html
hxxp://blackstyle.l2uc.ru/popeabuse.html
hxxp://bksxnations.com/popeabuse.html
hxxp://bidlo.lv/popeabuse.html
hxxp://create-serv.ru/popeabuse.html
hxxp://c-s-x.ru/popeabuse.html
hxxp://barrygloria.com/popeabuse.html
Sample client-side exploits serving URL: hxxp://webpageparking.net/kill/borrowing_feeding_gather-interesting.php
Sample malicious payload dropping URL: hxxp://webpageparking.net/kill/borrowing_feeding_gather-interesting.php?
vxbzcc=1n:33:2v:1l:1h&tvwogqxl=3i&hkrjvnuc=1l:2v:1i:1i:2v:31:1n:1l:1o:1m&levo=1n:1d:1f:1d:1f:1d:1j:1k:1l
Malicious domain name reconnaissance:
webpageparking.net – 109.74.61.59; 24.111.157.113; 58.26.233.175; 155.239.247.247 – Email: mtviclub@yahoo.com
Name Server: NS1.STREETCRY.NET
Name Server: NS2.STREETCRY.NET
We’ve already profiled the same Name Servers in the following malicious campaigns:
- Spamvertised BBB ‘Your Accreditation Terminated” themed emails lead to Black Hole Exploit Kit
- ‘ADP Package Delivery Notification’ themed emails lead to Black Hole Exploit Kit
Responding to 24.111.157.113 are also the following malicious domains part of related campaigns:
secureaction120.com
secureaction150.com
fenvid.com
heavygear.net
cyberage-poker.net
hotels-guru.net
porftechasgorupd.ru
gatovskiedelishki.ru
sawlexmicroupdates.ru
buxarsurf.net
buyersusaremote.net
cyberage-poker.net
hotels-guru.net
openhouseexpert.net
picturesofdeath.net
plussestotally.biz
teenlocal.net
Upon successful clienet-side exploitation, the campaign drops MD5: 24d406ef41e9a4bc558e22bde0917cc5 – detected by 15 out of 45 antivirus scanners as Worm:Win32/Cridex.E
Once executed, the sample writes the following files on the affected hosts:
C:DOCUME~1<USER>~1LOCALS~1Tempexp1.tmp.bat
C:DOCUME~1<USER>~1LOCALS~1Tempexp2.tmp.exe
C:Documents and Settings<USER>Application DataB2CB1881B2CB1881
C:DOCUME~1<USER>~1LOCALS~1Tempexp3.tmp.bat
Copies the following files:
Source: C:3e40e6903716e0a59a898242161c55c2ca100e539a665a8634e101346ce289be
Destination: C:Documents and Settings<USER>Application DataKB00927107.exe
Source: C:DOCUME~1<USER>~1LOCALS~1Tempexp2.tmp.exe
Destination: C:Documents and Settings<USER>Application DataKB00927107.exe
Creates the following processes:
C:WINDOWSsystem32cmd.exe” /c “C:DOCUME~1<USER>~1LOCALS~1Tempexp1.tmp.bat””
C:Documents and Settings<USER>Application DataKB00927107.exe
C:DOCUME~1<USER>~1LOCALS~1Tempexp2.tmp.exe
C:WINDOWSsystem32cmd.exe” /c “C:DOCUME~1<USER>~1LOCALS~1Tempexp3.tmp.bat””
The following Mutexes:
LocalXMM000007B4
LocalXMI000007B4
LocalXMM00000308
LocalXMI00000308
LocalXMS6C66A66E
LocalXMM00000630
LocalXMI00000630
LocalXMQ6C66A66E
LocalXMR6C66A66E
LocalXMM000004E4
LocalXMI000004E4
LocalXMM00000660
LocalXMI00000660
LocalXMM000000CC
LocalXMI000000CC
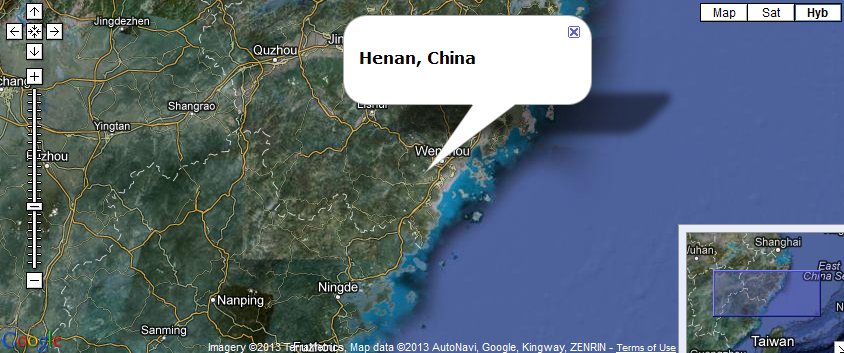
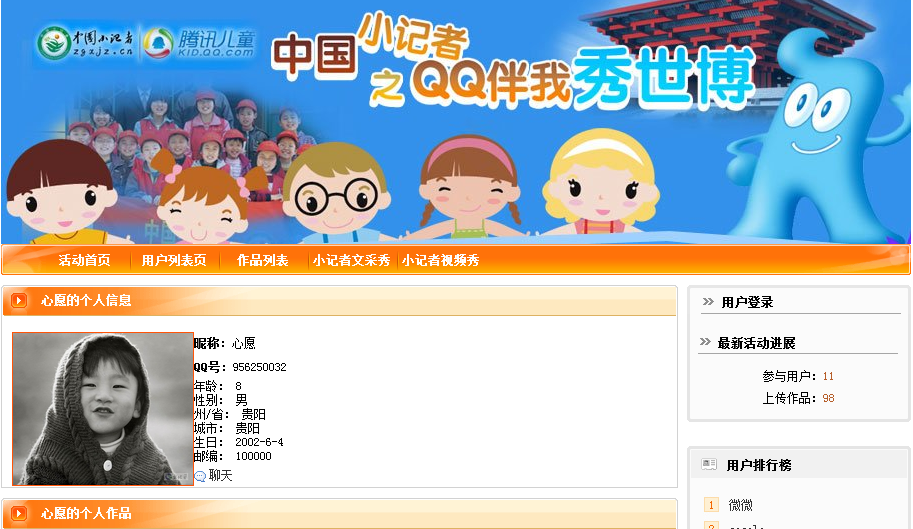
It then phones back to hxxp://203.171.234.53:8080/DPNilBA/ue1elBAAAA/tlSHAAAAA/. The IP resolves to lrdf.org.cn (Email: 956250032@qq.com); zgxjz.com (Email: gmc@sohumail.net)
The command and control IP (203.171.234.53) use to respond to a Name Server in a previosly profiled malicious campaign – “Malicious ‘RE: Your Wire Transfer’ themed emails serve client-side exploits and malware“.
The following malicious Name Servers are known to have responded to the same IP (203.171.234.53):
ns4.forumilllionois.ru
ns4.forumla.ru
ns4.forum-la.ru
ns4.forumny.ru
ns4.forum-ny.ru
ns4.faneroomk.ru
ns4.familanar.ru
ns4.filialkas.ru
ns4.forummoskowciti.ru
ns4.forumrogario.ru
ns4.forumkinza.ru
ns4.fuigadosi.ru
ns4.forumbmwr.ru
ns4.forummersedec.ru
ns4.forumvvz.ru
ns4.famagatra.ru
ns4.fzukungda.ru
ns4.ejjiipprr.ru
ns4.finalions.ru
ns4.eiiiioovvv.ru
ns5.efjjdopkam.ru
ns5.eipuonam.ru
ns5.eminakotpr.ru
ns4.emmmhhh.ru
ns5.epionkalom.ru
ns4.errriiiijjjj.ru
ns5.ewinhdutik.ru
ns5.ejiposhhgio.ru
ns5.esigbsoahd.ru
We believe that the C&C server is a compromised host based in China, as well as the actual emails, as the QQ ID appears to be a legitimate one.
Webroot SecureAnywhere users are proactively protected from this threat.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.