Over the past week, we intercepted a massive ‘ADP Payroll Invoice” themed malicious spam campaign, enticing users into executing a malicious file attachment. Once users execute the sample, it downloads additional pieces of malware on the affected host, compromising the integrity, and violating the confidentiality of the affected PC.
More details:
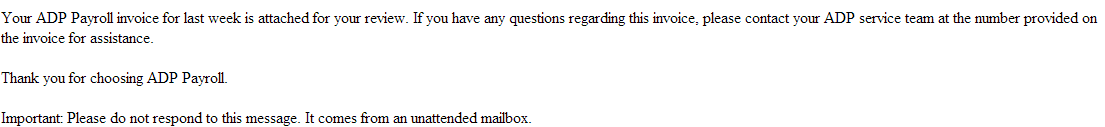
Sample screenshot of the spamvertised email:
Detection rate for the malicious attachment:
MD5: 54e9a0495fbd5c952af7507d15ebab90 – detected by 24 out of 46 antivirus scanners as Trojan.Win32.FakeAV.qqdm
Once executed, the sample creates the following files on the affected hosts:
C:DOCUME~1<USER>~1LOCALS~1Temp109086.exe
C:DOCUME~1<USER>~1LOCALS~1Temp132059.exe
C:DOCUME~1<USER>~1LOCALS~1Temp132981.exe
C:DOCUME~1<USER>~1LOCALS~1Temp135214.exe
C:Documents and Settings<USER>Application DataOrihgyikegfa.exe
C:WINDOWSsystem32cmd.exe” /c “C:DOCUME~1<USER>~1LOCALS~1Temptmp659bfaec.bat
C:Documents and Settings<USER>Application DataUpwegingo.exe
C:WINDOWSsystem32cmd.exe” /c “C:DOCUME~1<USER>~1LOCALS~1Temptmp2f8a78b4.bat
C:Documents and Settings<USER>Application DataYcecnhiocty.exe
C:WINDOWSsystem32cmd.exe” /c “C:DOCUME~1<USER>~1LOCALS~1Temptmp0ffe0049.bat
C:Documents and Settings<USER>Application DataInizlokezy.exe
C:WINDOWSsystem32cmd.exe” /c “C:DOCUME~1<USER>~1LOCALS~1Temptmp97858d3e.bat
Deletes the following files:
C:Documents and Settings<USER>Application DataOrihgyikegfa.exe
C:Documents and Settings<USER>Application DataUpwegingo.exe
C:Documents and Settings<USER>Application DataYcecnhiocty.exe
C:Documents and Settings<USER>Application DataInizlokezy.exe
Creates the following Registry Key:
HKEY_CURRENT_USERSoftwareWinRAR
And sets the following Registry Value:
[HKEY_CURRENT_USERSoftwareWinRAR] -> HWID = 7B 46 45 46 34 31 34 39 38 2D 39 32 38 39 2D 34 45 44 32 2D 41 36 31 46 2D 45 35 46 32 30 33 34 46 34 38 45 30 7D
It also creates the following Mutex:
Global{CB561546-E774-D5EA-8F92-61FCBA8C42EE}
It then phones back to hxxp://www.rpc-ea.com:8080/forum/viewtopic.php and downloads additional malware samples from the following locations:
hxxp://axelditter.de/w91qZ5.exe
hxxp://infoshore.biz/cx5oMi.exe
hxxp://www.makefacebook.com/LxB8.exe
hxxp://www.qualitymachineinc.com/QabtyY.exe
Initiating the following TCP connections:
213.186.47.54:8080
195.93.201.42:80
216.55.186.239:80
77.92.151.6:80
66.118.64.208:80
Detection rates for the downloaded malware samples:
hxxp://infoshore.biz/cx5oMi.exe – MD5: 13eeca375585322c676812cf9e2e9789 – detected by 3 out of 46 antivirus scanners as Heuristic.LooksLike.Win32.Suspicious.B
hxxp://axelditter.de/w91qZ5.exe – MD5: 87c658970958bb5794354a91f8cc5a7d – detected by 18 out of 46 antivirus scanners as PWS:Win32/Zbot.gen!AM
Upon execution, MD5: 87c658970958bb5794354a91f8cc5a7d creates the following processess on the affected hosts:
C:Documents and Settings<USER>Application DataAxujpiwoovaw.exe”
C:WINDOWSsystem32cmd.exe” /c “C:DOCUME~1<USER>~1LOCALS~1Temptmp541b0e3b.bat”
The following Registry Keys:
HKEY_CURRENT_USERSoftwareMicrosoftHior
Sets the following Registry Values:
[HKEY_CURRENT_USERIdentities] -> Identity Login = 0x00098053
[HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun] -> {3DFA1AE4-115C-AD7B-A6BA-A75086AF8442} = “”%AppData%Apasaviqpil.exe””
[HKEY_CURRENT_USERSoftwareMicrosoftHior] -> 21ae50c4 = “gQDD+nAQQMo=”; 1gi1fji2 = “owCu+g==”; eg614da = 86 6A AE FA 97 7B 71 CA 0B 18 89 8E
As well as the following Mutexes:
Global{CB561546-E774-D5EA-8F92-61FCBA8C42EE}
Local{FA4803F7-084F-6AC9-A6BA-A75086AF8442}
Upon execution MD5: 13eeca375585322c676812cf9e2e9789 creates the following processess on the affected hosts:
C:Documents and Settings<USER>Application DataNaarqunayhi.exe”” (successful)
C:WINDOWSsystem32cmd.exe” /c “C:DOCUME~1<USER>~1LOCALS~1Temptmp677a8160.bat”” (successful)
The following Registry Keys:
HKEY_CURRENT_USERSoftwareMicrosoftIcuruq
The following Registry Values:
[HKEY_CURRENT_USERIdentities] -> Identity Login = 0x00098053
[HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun] -> {3DFA1AE4-115C-AD7B-A6BA-A75086AF8442} = “”%AppData%Cyviexylawq.exe””
[HKEY_CURRENT_USERSoftwareMicrosoftIcuruq] -> 1f7edeb4 = 73 78 91 BC 8C 7E 3C 48; 1ih8g5e6 = 51 78 FC BC; 880c122 = 3B 2C FC BC 73 0F 0E 48 FB 16 69 C9
as well as the following Mutexes:
Global{D43DCFB8-3D8A-CA81-0508-B06D3016937F}
Global{D43DCFB8-3D8A-CA81-7109-B06D4417937F}
Global{D43DCFB8-3D8A-CA81-490A-B06D7C14937F}
Global{D43DCFB8-3D8A-CA81-610A-B06D5414937F}
Global{D43DCFB8-3D8A-CA81-8D0A-B06DB814937F}
Global{D43DCFB8-3D8A-CA81-990A-B06DAC14937F}
Global{D43DCFB8-3D8A-CA81-350B-B06D0015937F}
Global{D43DCFB8-3D8A-CA81-610B-B06D5415937F}
Global{D43DCFB8-3D8A-CA81-B90B-B06D8C15937F}
Global{D43DCFB8-3D8A-CA81-190C-B06D2C12937F}
Global{D43DCFB8-3D8A-CA81-4D0C-B06D7812937F}
Global{D43DCFB8-3D8A-CA81-650C-B06D5012937F}
Global{D43DCFB8-3D8A-CA81-C10D-B06DF413937F}
Global{D43DCFB8-3D8A-CA81-310E-B06D0410937F}
Global{D43DCFB8-3D8A-CA81-610E-B06D5410937F}
Global{D43DCFB8-3D8A-CA81-E50F-B06DD011937F}
Global{D43DCFB8-3D8A-CA81-E90B-B06DDC15937F}
Global{D43DCFB8-3D8A-CA81-DD0C-B06DE812937F}
Global{D43DCFB8-3D8A-CA81-A10E-B06D9410937F}
Global{D43DCFB8-3D8A-CA81-1D0E-B06D2810937F}
Global{EEE5022F-F01D-F059-8F92-61FCBA8C42EE}
Global{38E3341C-C62E-265F-8F92-61FCBA8C42EE}
Global{340FE32E-111C-2AB3-8F92-61FCBA8C42EE}
Global{340FE329-111B-2AB3-8F92-61FCBA8C42EE}
Global{5E370004-F236-408B-8F92-61FCBA8C42EE}
Global{D43DCFB8-3D8A-CA81-2D0D-B06D1813937F}
Global{CB561546-E774-D5EA-8F92-61FCBA8C42EE}
Local{55E9553D-A70F-4B55-8F92-61FCBA8C42EE}
Local{744F300D-C23F-6AF3-8F92-61FCBA8C42EE}
Local{55E9553C-A70E-4B55-8F92-61FCBA8C42EE}
MPSWabDataAccessMutex
MPSWABOlkStoreNotifyMutex
MSIdent Logon
MidiMapper_modLongMessage_RefCnt
MidiMapper_Configure
It then attempts multiple UDP connection attempts to the following IPs part of the botnet’s infrastructure:
109.162.153.126:25603
81.149.242.235:28768
88.241.148.26:19376
78.166.167.62:26509
88.232.36.188:11389
80.6.67.158:11016
If you catch an ADP impersonating email in the wild, please forward it to abuse@adp.com to notify ADP of the attack.
Webroot SecureAnywhere users are proactively protected from this threat.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.