Relying on tens of thousands of fake “Your transaction is completed” emails, cybercriminals have just launched yet another malicious spam campaign attempting to socially engineer Bank of America’s (BofA) customers into executing a malicious attachment. Once unsuspecting users do so, their PCs automatically join the botnet operated by the cybercriminal/gang of cybercriminals operating it, leading to a successful compromise of their hosts.
More details:
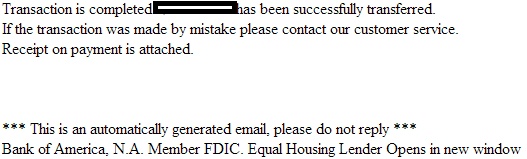
Sample screenshot of the spamvertised email:
Detection rate for the malicious executable:
MD5: c671d0896a2412b42e1abad4be9d43a8 – detected by 31 out of 46 antivirus scanners as Trojan-Spy.Win32.Zbot.kulh.
Once executed, the sample creates the following files on the affected hosts:
C:Documents and Settings<USER>Application DataAxuxjedurqy.exe
C:DOCUME~1<USER>~1LOCALS~1Temptmp92c578d1.bat
C:WINDOWSsystem32WBEMPerformanceWmiApRpl_new.h
C:WINDOWSsystem32WBEMPerformanceWmiApRpl_new.ini
C:WINDOWSsystem32PerfStringBackup.TMP
C:WINDOWSsystem32WBEMLogswmiprov.log
It also creates the following Mutexes:
Global{2E06BA86-8AE7-D5EB-DBC9-BE58FA349D4A}
Global{B0B9FAFD-CA9C-4B54-DBC9-BE58FA349D4A}
Global{B0B9FAFC-CA9D-4B54-DBC9-BE58FA349D4A}
Global{D15F4CEE-7C8F-2AB2-DBC9-BE58FA349D4A}
Global{D15F4CE9-7C88-2AB2-DBC9-BE58FA349D4A}
Global{0BB5ADEF-9D8E-F058-DBC9-BE58FA349D4A}
Global{BB67AFC4-9FA5-408A-DBC9-BE58FA349D4A}
Global{F69375E1-4580-0D7E-11EB-B06D3016937F}
Global{F69375E1-4580-0D7E-75EA-B06D5417937F}
Global{F69375E1-4580-0D7E-4DE9-B06D6C14937F}
Global{F69375E1-4580-0D7E-65E9-B06D4414937F}
Global{F69375E1-4580-0D7E-89E9-B06DA814937F}
Global{F69375E1-4580-0D7E-BDE9-B06D9C14937F}
Global{F69375E1-4580-0D7E-51E8-B06D7015937F}
Global{F69375E1-4580-0D7E-81E8-B06DA015937F}
Global{F69375E1-4580-0D7E-FDE8-B06DDC15937F}
Global{F69375E1-4580-0D7E-0DEF-B06D2C12937F}
Global{F69375E1-4580-0D7E-5DEF-B06D7C12937F}
Global{F69375E1-4580-0D7E-95EE-B06DB413937F}
Global{F69375E1-4580-0D7E-F1EE-B06DD013937F}
Global{F69375E1-4580-0D7E-89EB-B06DA816937F}
Global{F69375E1-4580-0D7E-F9EF-B06DD812937F}
Global{F69375E1-4580-0D7E-E5EF-B06DC412937F}
Global{F69375E1-4580-0D7E-0DEE-B06D2C13937F}
Global{F69375E1-4580-0D7E-09ED-B06D2810937F}
Global{F69375E1-4580-0D7E-51EF-B06D7012937F}
Global{F69375E1-4580-0D7E-35EC-B06D1411937F}
Global{F69375E1-4580-0D7E-B1EA-B06D9017937F}
Global{DDB39BDC-ABBD-265E-DBC9-BE58FA349D4A}
Global{2E1C200D-106C-D5F1-DBC9-BE58FA349D4A}
Local{911F9FCD-AFAC-6AF2-DBC9-BE58FA349D4A}
Local{0BB5ADEF-9D8E-F058-DBC9-BE58FA349D4A}
Local{D15F4CE9-7C88-2AB2-DBC9-BE58FA349D4A}
Local{D15F4CEE-7C8F-2AB2-DBC9-BE58FA349D4A}
Local{B0B9FAFC-CA9D-4B54-DBC9-BE58FA349D4A}
Local{B0B9FAFD-CA9C-4B54-DBC9-BE58FA349D4A}
And phones back to the following C&Cs servers:
99.150.209.246:13467
190.198.187.99:12407
180.248.91.99:10097
197.251.139.27
82.211.186.140
99.103.42.49
71.193.224.27
81.133.189.232
199.59.157.124
173.239.134.186
67.248.126.173
107.216.164.109
81.149.242.235
195.169.125.228
186.47.28.133
90.156.118.144
173.194.67.147
173.194.67.94
95.228.232.129
178.150.15.40
24.120.165.58
194.94.127.98
79.186.118.100
213.123.186.173
66.159.154.0
201.108.29.121
105.227.88.252
71.239.8.51
94.71.9.152
87.30.121.173
95.227.216.136
More malware variants (SHA256 fingerprints) are known to have phoned back to the same IPs, for instance:
dd388f536ca699b5fa88da86232b11e914cd3e713efd84d2ea5db1de8175fd90
1580bedbe22ad3709910558d9377229a609e9539d3e66010bfa0507a9fb8617b
ef2172114c42eb8b139f13941e02ee309f7e87a48250f774dfd937b693f9ca11
1c4b50e28e54d75afc3cefcbd40515504a617f1bd40bfccc1388091e2f6ab5cb
0e171294d6a7f5b77c82a44787c48e5c3eaba06d224cb3a133338192e737cfd6
b5c7713884d6bdfaf0a42c78cebf368037d726c4da27e6e4b0bcfa5feecdb3eb
2c4b204963a0bf4c242d34b2db8a0e9c0f3f956986459678ee4ef0a1402a8a6f
1b9fc0993cd8f8d171ceef3db59b70b9e440e12b912fd4d2fdc0357857a7ca4a
72bf6831d1c6dc0b7dd59bf4c6c07f064d53448dc82bad6b7359805d1f35295a
2be31ff86d00669d8dd9a4128edb536adaa1735493aa00255f31d3a17faa381d
a1401304f67fb5a5e17e88eee7b66f69cfe101b2cb9c2d785fadd3af873f53be
f5c74532db8f74ad555e942936a21db1d6d900a5eeecda8459a94ddbf1e59b4a
a5e94a56e9a4d6b0f8f4d6b176ab5c2f822a515032a613fa8747507de9b1a914
01f043a95b1c510ef1028c03fb4036e9a2bb3f9686b2a100ee7a0a6a5f5be786
7b76fa242daad8b712700835167a7f8873c6fda64f7ea07e85fe91480b86fa7c
4521d4cffdc936750758174076c89fda93c02cade8bd15845ea11e3586e399e5
bc60ac2db315faf145b2a6f2782bb8a3cb27abfbe90d0101cab956c7cf89ce0e
868fd778575dd790be0c242f630b917c370b0ef64b456855b0ca3e21d5efca45
862390d1fa5f0261bf73a482c848dc358d2c08eb339bfd3b675f3a630b66f1ab
f553605e8d16291f72c26e719ff93ed1da91891681262e626aee74b30c727d4b
e57f702288be13538e74257c44a5ea673fe09a674342ab35cfd4d5b74ff66c8f
7a6b2959f2e6ef8b036838d5cf19e9c54b559c926444942f1ddeb9630fb0d406
17abceb5551390b12abd5900a2261039795a13ff8299c4e95634cb2f567d49d0
63b76a7e0fe45c54d8a9ce890b1f3efd64e6db04d1ca2f8b911dfb130b26e877
8a0167626f408476ac05d0436f3d84be1573fd7a60d23fc18c562275fcd30729
9c5b22700b9ec07a0b4ca893884dcbad37183020633b960cce32d72adda69ba7
8c6c659110a9be368884111db7889ff8745c942b257088cbf9924a750b0b4f88
016f051c6c66fa725ac4da5cd55dd3d7dada01c2469b3f8f49f040f5e61781e1
1042fa15d0ad53be3c724a5b12d0a50dc02dd9aa8487571cbf6b6848b569ed21
14d7d240024e411df1fb7e80fb2dc5f1fb22673c8969ac334d4207b3b13dfa1d
48dd15d56ed49e3735c8b4a36a20405a4248f62f1fa5994f640229d7910df8ab
975cbf9b9509df43e588a6ff9acada093f7dc1cfeb9898f73fb22ff131f0739b
e0849e5d6cebd727391add2e1781f301834f378e072f824fcb192a0777307035
1fb1dfdbade1591460c0a09a8055a57b20fce525ec3c154ed62286cb49841b87
35b8ca7823c5559cc556108fddd2e67814bc23e45b80182a239759da48cbfe8f
c85bf154a41355d728526d5b826b344f12e839394257c1c4a1f7869992fbb656
80bc7a929825b66afeeb8ca991a1d83425f40187565f60c245cbbbba89a83fd4
a4ee41287f4fdda934e8e0ca74608ac1b2045403680c1e2384e26bb6bdd6c6c3
f996849059d74cda88460a917b66e5b74572296de9ab1312488cff98fdcd11c3
8ddedf1d24d8ef94e44f6ab659f6ffa80eaef9e30637b3943115485ab5e0f082
4cb928ad4a5de0eea1120f64a7ed2f246f63e493334c444e0fa788065879e007
92d518f080fda738d091b1061c465b4e718ab259bf5aecf72056f66906930898
34fc1bbef1c1a9d249c5640afb8b968ff8bfeb963b7d71248c7ecaf2397f02e1
b51889a30a23121b93ed9bd5a3af963ad8cda3f9e35f4661ba35e0341b0dda66
dfcf14b00b6cb3eaafa4a8aaeaec900ece1a707e9c5e262275bbeaa56015f217
e410200a22fcecf06b1dfa0a717960d36485df109333a802fd17515305408499
9f8d4010f4d9b4d21e8bef3dca897fa18184fe799d0092e2855568657aab74e5
241fa0371f21bb81260d9f14afd15fe1ed024722f2af9637cbb29dddb68661bc
dd40132ebd545205d7b1b8e198ddafd0b7c0dde07a7d07cb2f9466ba84cc3e94
5e177d2a57bca8c7c0207737e64ac437e683bb19f66fdeb491cd0f95a34b507e
248978ae8d5be35cb6e89ceacf8b029f079ad8c0e2126d58c1de805be1e44659
234bf4a125300c3f06021f838c1fa4f7b80f2331597fa1996a95a2db3333f14c
465368262173ee407ff9fddd6510c1b3b51f8a05cbdcf4bd6754e59aea8a9171
88220d82c7ce4d2b44ce90f8950c1500c0c54657be77aba63f9316c3dc48c36d
54889a3db40b760a0fcceaf0de4b1d207bebfdcd76a7e54bb891b11f983a0d0e
05ace7c732426fd67247120aef9ba4e7fb8ee7bc61983955f7fb9e97d039c1b9
5764d63ce147c0a80f25d13826874803608f5be487d5b762d9e55e514ac2074b
91f7a47e2250b5a6df275da87655d91772ec65528271a403750abc4808cf5ad1
dc8690d1ba81398fc2e759c08e3bcc7eb4f9a4e33065b1396b4374fd1bd58867
c5c35031e4a6944647d0d2e5621b3582db79bd83ea5807e72575b18e03f5a9f8
aa147e6d8f5144e0b0978d3b5d049d82c233982040c7397b21eafd8d99491ed1
be3b0e9000d43a76b779e0e08d41337016ffe46e454b3f3c88316bb83e74a79f
08b5d43886e848873a2d5320f2e978035e0210e490c6a8ba9cd6fe2e7a59fc8f
29169947ea875b15f9135402db9830596945a62cf4bc7929a755ca3b460ec163
f9de80561b379eb741046ff77f5e48914554977a0cd668fe7155a7e18d073df7
9b1dbf5a4f2ccef598f8332da7bf51bc5d5a9c35bcef7d18472d5cc08b3547d5
c3d7bde1ad141e6fcb4fd4a353ac1410a45534d4d1de2ee4ce26d94a60a0e29e
7897e719a1b389d7df58ac0a240a8fe1dca2a4e91c55329f1aa5b6673a4d6ddb
041db97b30cc1402d268a25b204de76a0abd4ef6fef503af5f60fcec33c9fafc
7f23ec4cb15241da3be574d06c77e40675587773ee36fbf40ecfff3b43d8b38f
7d21a0ad9d36227412da5550c364cddbe3c1bfc8afce0852eb7d740403f0cc87
e0657780885d656c8ff4a4a260dc493b8ca858ed3cf253853af58928b56f0ad4
80af858e12e6799beb5673714baf3b5ebd69082a8626bba71dc6d8eb1818fd83
54dc399d673193808513a59f1d27783eea75a437a61c83e4b90917f0bce6efc7
84e61a33e7e967ff6e0ac2e6a12035f2d5c113d5c71cb285e0e1c3df8b565420
edd335e53152f4d19ca32b1c315d32ab77d92dc313f3719e13b37f690c6cccd7
bc4c5bc7be997971c59fd5ca3aea2554874abc8492ad77256134fdb602c40805
4d0a3aa812096bae68ecc0b8000a4afcbf8d123fc9a74da23c4e3767eed14874
2648aab4b546709a0f37aaf5a3a65d75eff93a48fc25122905516c2c36f93731
1583f1ff4f4874cb6591a727894d35dd097420686ce9943def2cd4724ce506e4
e657944d81dd697b6eb84bd14ccf0a28de01056deb7f584892e0ae0adf9532fe
f3791c4f508b1c6940f0914ff9756718ca399d890c91d2dae36b5729b581d6b8
01b4d9e87a70243455dfdb924c9c42537426507d13a2e1c15e7ab6ee52df3792
d356d2d3286c8945dca457c8ceab81f3b2be04ef197ce2f0ddbfba004ac779f0
ca3a56abeb49553e764e79eb35ef99c4e641dafb9dc8149f69257b6aa3ecdb16
ab5e5eee97b92e88cc6ba831e44a271ac60f551a4ecbf387581529edf9baacaa
05f26df2733bb82be9b852d80a310fc3db4adc8e1d947f0225077d7bb34e3ea1
0f03a1edea1b34c96d031be460e151518f0e27141dafa7ff6275f78d0a2caed8
93a3544d369b54790943c26c45fc330e141c589c25b1d672e2b0a69c6f0d995b
1804a29196ca365426cda21fdd2ceff3b001623513eed857b326db425c19e505
07e9cad85689f2afdca86bf44143b32974501c39a7359e95d12fa8baa6a950a0
4a584eb5f3f4317f7bd4da5a360898a4d296e03a5f3c5669ae8f940de0ba92f4
6f35ea4f3a105531be55a0c7ef27d2610982f291d868d6b7e6d8a833bed54aef
146038c969f87e1de02a44d41c6828d8057641a186787f48094eae5c7a1cb166
d201eca15eed4482acdd8a1e2d7fc7eeddada81fe2928b42c4599e7214508438
b24159214ff4c0c6fc80cfb63938363accfb0d124260e5c9c7b5c8cc5d217ee0
beff41cd1d4d22f983b44c77827c075e58bf70738e44ad64e78db917856c4e53
b152e47152c1759e8f58120bd9682b5e01e3d3a98aa86bc7dd336012ffd5003e
231791d2448413457c4279660f76c65e5c85a85c1f61648a793d055384bb64a0
625802ae10be85c529bf7bc7e082b2d3acf6ccf99d8789399b66f6f2f921284f
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.







173.194.67.94 appears to be a Google server.
173.194.67.147 also Google.