By Dancho Danchev
Bitcoin, the digital peer-to-peer based currency, is an attractive target for cybercriminals, who persistently look for new monetization tactics to apply to their massive, but easily generated botnets. Not surprisingly, thanks to the buzz surrounding it, fraudulent Internet actors have begun to look for efficient ways to take advantage of the momentum. A logical question emerges – how are market oriented cybercriminals capitalizing on the digital currency?
Instead of having to personally infect tens of thousands of hosts, some take advantage of basic pricing schemes such subscription-based pricing, and have others do all the infecting, with them securing a decent revenue stream based on a monthly subscription model.
Let’s profile the international underground market proposition, detailing the commercial availability of a stealth Bitcoin miner, feature screenshots of the actual DIY miner generating tool, screenshots provided by happy customers, and perhaps most importantly, MD5s of known miner modifications ‘pushed’ since its first commercial release.
More details:
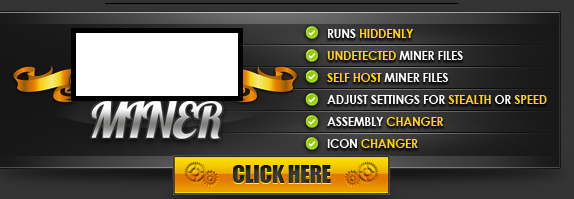
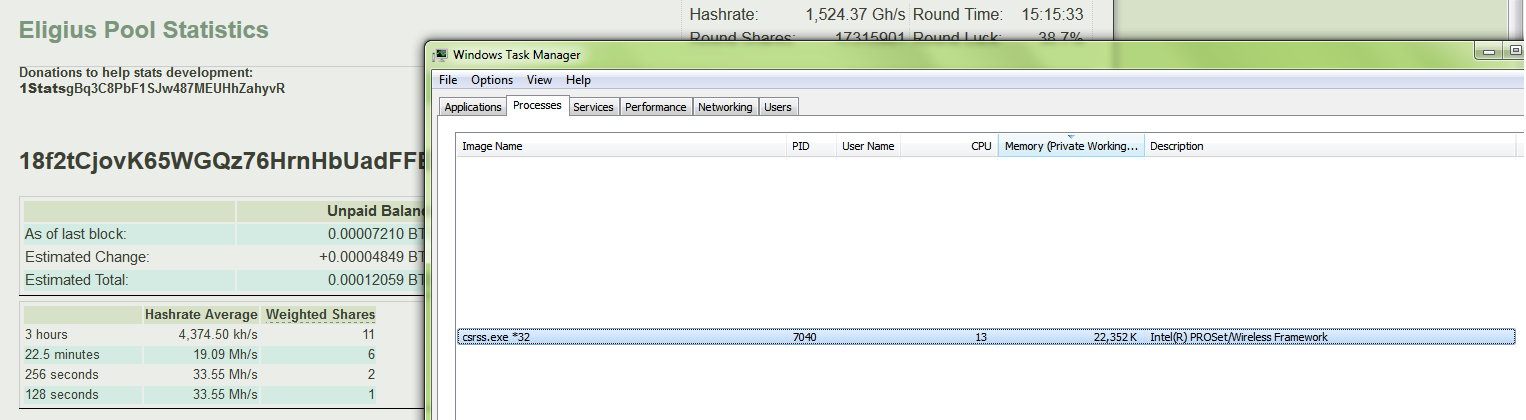
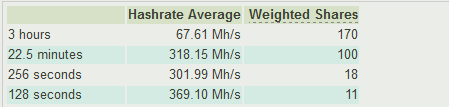
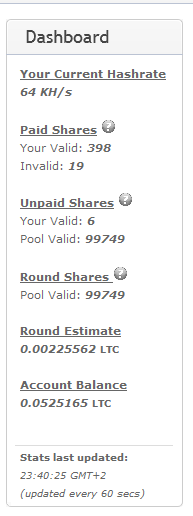
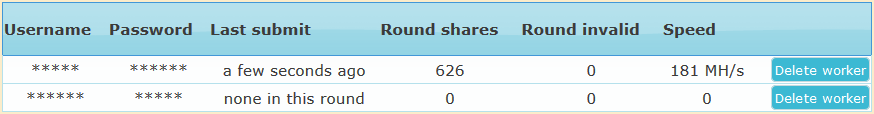
Sample screenshot of the actual advertisement for the stealth Bitcoin miner:
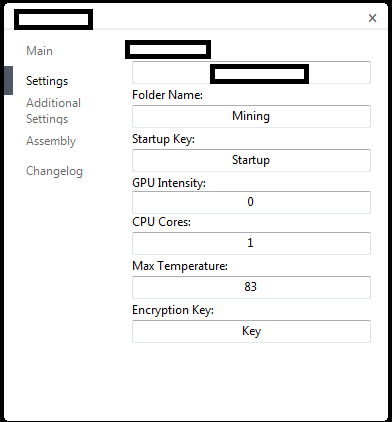
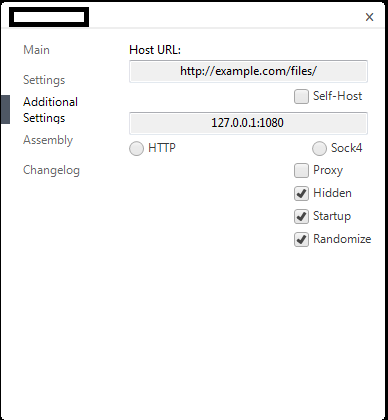
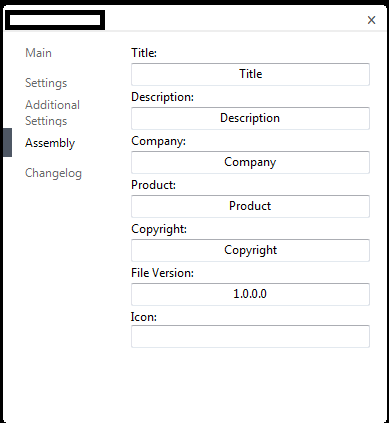
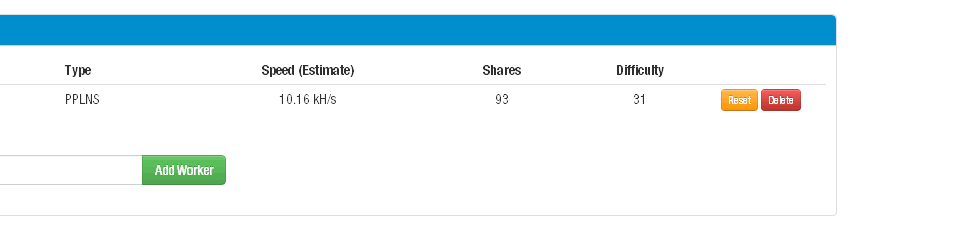
Sample screenshots of the stealth Bitcoin mining generator:
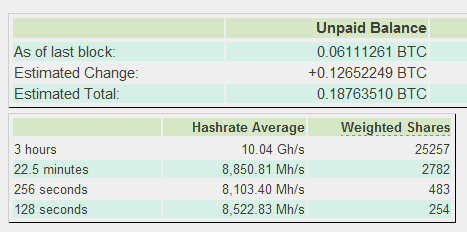
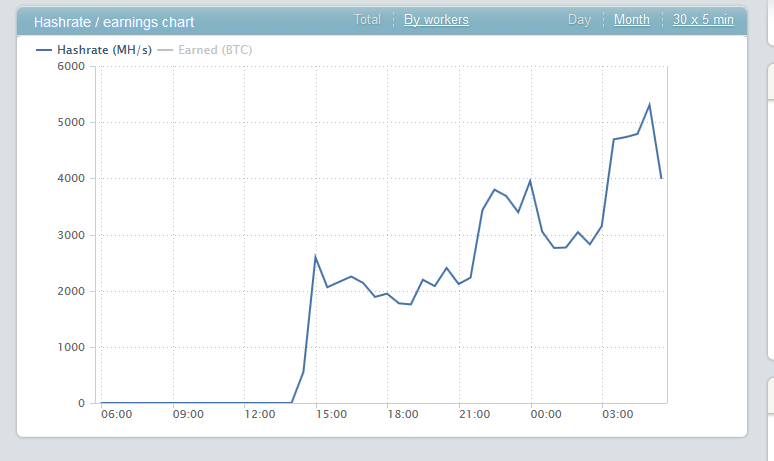
Sample screenshots courtesy of happy customers demonstrating that the service works:
The price is $10 USD per month through PayPal, which includes automatic updates to the miner executable. The EULA also reserves the right not to be held responsible for any unauthorized use of the stealth Bitcoin miner. Now, why would someone want to hide something from himself remains a mystery, similar to the commercial availability or Remote Access Trojans pitched as Remote Access Tools, given the fact that they come with built-in rootkit/evasive features.
Although at the initial commercial release of the miner, the author was manually updating the executable on a periodic basis, as of April, 2013, the updates are delivered automatically. Here are some MD5s of known variants that we’re currently aware of:
MD5: 226640cad180b11add53aeca10fd41cb
MD5: 7222fbe30d2016e23006c86f97c4a16d
MD5: e6a7d8c0191717b4c42ebeaca19fa2cf
MD5: b57d24469184d1f920a160bcd94f73fc
MD5: 58a37543d436574b7d560a8b3106b2b5
MD5: ff36078529de25cce4c488c18fe9fd9a
MD5: de8004da46658cb916ba6b549b980b05
MD5: cc3312a2f6c307ac06f146be20854061
MD5: fada1f789bd7b174fa6a52a23076f015
MD5: 850c56dd94e4e108af8c68f9dda06334
MD5: 4d6107c1872bbb06eb9cfa0f5f9df252
MD5: fada1f789bd7b174fa6a52a23076f015
MD5: 373b88dc8641e05126a1e89160ecfc38
MD5: 1b3475f885d86ac60f3c26bc672fe7b9
MD5: 738a06ed975041e18f062963188a53a0
MD5: 4eb05249c9aad2b465dd59ae7bdf92cf
MD5: 738a06ed975041e18f062963188a53a0
MD5: 430cdcfaf90a3fc4441b1ab88aa77c08
MD5: a8b407f9bd937f0b508519d21a4c4087
MD5: b9ade02f38ccbd77136ab54043b08c69
MD5: 81f43255d4c3c1212744d6d96109e4f2
MD5: a5c280ead0a5c9b9a40f21419d10a9aa
MD5: a9332ec09d35ac0b5550ffd52953a1e6
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.